Heated Seats? Advanced Telematics? Software-Defined Cars Drive Risk
Carmakers are offering all kinds of over-the-air subscriptions and features, many of which benefit the businesses that use them. But this also opens up a wider attack surface for vehicle attackers.
March 13, 2024

Driven by the promise of new lines of revenue and lower manufacturing costs, automobile manufacturers are enthusiastically turning vehicles into next-gen application platforms. Increasingly, organizations that run fleets or have transport as a key part of their business can opt into "software defined" features that can be turned on and off over the air, offered on a subscription basis. The bad news is that this next version of smart-car ingenuity also increases the vehicular attack surface and business risk, experts warn.
Deloitte defines software-defined vehicles (SDVs) as reflecting "the gradual transformation of automobiles from highly electromechanical terminals to intelligent, expandable mobile electronic terminals that can be continuously upgraded."
This means offering bug fixes and improving safety features such as anti-collision systems and driver assistance via OTA software updates; offering subscriptions for infotainment systems such as music and video streaming, or on-board Wi-Fi access; the ability to opt in for bells and whistles with the push of a button, like seat heaters or self-driving; and perhaps most interestingly for fleet managers, continuous telematics and diagnostics, allowing for more effective preventative maintenance.
There are some not-so-great elements of the SDV revolution, too: Not only do manufacturers have the ability to turn features on and off, but they also can remotely disable the car using a starter-interrupt device, when, for example, loan payments are late.
Software-Defined Vehicle Risk Is Multipronged
Sure, this is all very futuristic and convenient, but SDVs open drivers to a plethora of risks that can result in vehicle theft, physical dangers, vehicle distributed denial of service (DDoS) via the remote disablement feature, follow-on social engineering attacks, and more.
The main issue is that this next generation of cars has fewer platforms and SKUs but more advanced telematics and software interfaces. This results in less retooling of assembly lines at factories, but a bigger code base also means more exploitable vulnerabilities. And with the over-the-air (OTA) capabilities that these cars offer, those attacks could potentially be carried out remotely.
Indeed, IOActive published a report last year finding that nearly half of all vulnerabilities discovered in 2022 involved network connections, compared with 40% local vulnerabilities and 10% physical hardware flaws. The share of local vulnerabilities have increased, driven by the exponential increase in the volume of code in the vehicle software stacks, the firm stated.
"In some ways, software-defined vehicles increase the opportunity for you to make a mistake," says Liz James, a senior security consultant at NCC Group, a cybersecurity consultancy that does assessments of vehicle cybersecurity. "The more complex your software stack gets, the more likely you are to have implementation bugs, and now you also have software installed that might never be run, which runs counter to traditional embedded system advice."
It's not just traditional vulnerabilities at issue. With the move to SDVs, cars increasingly resemble cloud infrastructure with virtual machines, hypervisors, and application programming interfaces (APIs), and with the increased complexity comes greater risk of failure, says John Sheehy, senior vice president of research and strategy at cybersecurity consultancy IOActive.
"A hypervisor compromise completely defeats all the great work automakers and suppliers have done to create segregation and isolation inside vehicle networks between critical control systems and non-critical ones," Sheehy says. A compromise of a car's telematics unit followed by a hypervisor escape, for example, would allow an attacker to control, modify, and manipulate any operation and data in a virtualized electronic control unit (ECU) running on that hardware. "This is a complete game over for passenger and vehicle safety," he says.
There's also a privacy risk. Car manufacturers collect a wide variety of data from the car's owners as they operate their vehicles. A proliferation of sensors, microphones, cameras, the phones and devices drivers connect to their cars, car apps, and vehicle telematics allow carmakers — including BMW, Ford, Toyota, Tesla, Kia, and Subaru — to collect deeply personal data that might be surprising. This includes intel on immigration status, race, facial expressions, weight, health and genetic information, geolocation — even data on in-car sexual activity, according to a 2023 analysis conducted by the Mozilla Foundation. All of that data can then be shared or sold to third parties, often used for marketing.
The Biden administration even warned in February that such capabilities, in the hands of Chinese carmakers, is a danger, since they "could collect sensitive data about our citizens and infrastructure."
Automakers Drive Software-Defined Cybersecurity
The concerns come as security researchers subject SDV architectures and their supporting infrastructure to more scrutiny. Consultancy SBD Automotive, for instance, has carried out ongoing penetration tests over the past three years. They found about a quarter of car vulnerabilities affected the off-board infrastructure supporting vehicles, such as mobile apps and APIs, while 76% directly affected the vehicles, including in the in-vehicle infotainment (IVI), the transmission control unit, and the gateway to the vehicle's control systems.
In mid-April at the Black Hat Asia in Singapore, researchers from Chinese Internet giant Baidu will discuss critical security issues found in the autonomous driving domain controllers that are used in many smart cars. At last year's Black Hat USA, cybersecurity researchers showed how they have been able to activate certain features on Tesla vehicles without paying.
This researcher focus is giving automakers' security efforts more impetus. IOActive's report, for instance, outlined the changes in the vulnerability landscape the company has encountered during six years of vehicle assessments: overall, car-makers have reduced the incidence of critical and high-severity bugs and made them harder to exploit, according to the firm.
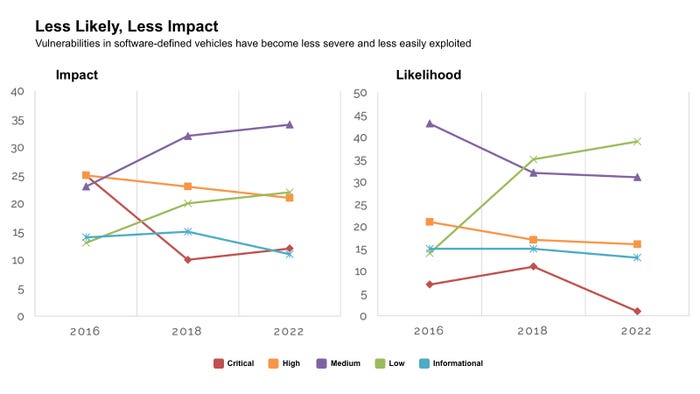
Software-defined vehicles have fewer critical and high-severity flaws, and they are less likely to be exploitable. Source: IOActive
A Long Road Ahead for SDV Security
While the vulnerability trends are good news, car manufacturers and their OEM suppliers still need to focus on creating development processes that prioritize security, says Dennis Kengo Oka, senior automotive security strategist at Synopsys Software Integrity Group.
Specifically, companies need to focus on "designing and building security controls from the start into these systems [and] establishing secure development processes to ensure secure coding and continuous testing in order to find issues early on and fix them," he says.
NCC's James also notes that utilizing unique cryptographic credentials for each ECU should be table stakes. And to secure vehicle-to-cloud (V2C) functionality, manufacturers should adopt a zero-trust architecture and run a security operations center capable of detecting and blocking anomalous behavior.
Manufacturers must also pay attention to the integrity of their supply chains. If a vehicle manufacturer's telematic service is compromised by attackers, then all of the vehicles serviced by that ecosystem are at risk — a significant problem for companies that manage a fleet of vehicles, says IOActive's Sheehy.
"This type of supply chain attack is a difficult problem to solve," he says. "Long term, all high-consequence cyber-physical devices like vehicles need a set of policies around supply chain integrity."
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




