CryptoWall Makes a Comeback via Malicious Help FilesCryptoWall Makes a Comeback via Malicious Help Files
Hackers use .chm attachments to execute malware on unsuspecting users.

A new spam wave has hit hundreds of mailboxes with malicious .chm attachments to spread the infamous CryptoWall ransomware, malware researchers from Bitdefender Labs found.
Interestingly, hackers have resorted to a less “fashionable,” yet highly effective trick to automatically execute malware on a victim’s machine and encrypt its contents – malicious .chm attachments.
.Chm is an extension of the Compiled HTML file format, a type of file used to deliver user manuals along with software applications. HTML files are compressed and delivered as a binary file with the .chm extension. This format is made of compressed HTML documents, images and JavaScript files, along with a hyperlinked table of contents, an index, and full text searching.
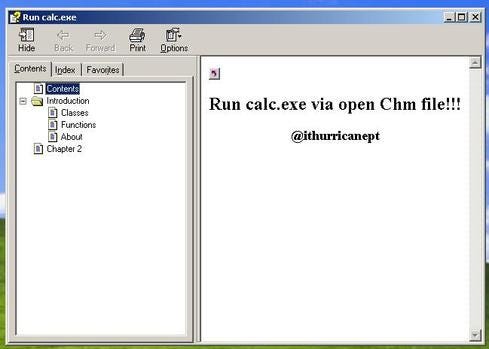
What Is So Dangerous About Help Files?
These .chm files are highly interactive and run a series of technologies, including JavaScript, which can redirect a user toward an external URL after simply opening a .chm file. Attackers began exploiting .chm files to automatically run malicious payloads once the file is accessed. And it makes perfect sense: The less user interaction, the greater the chances of infection.
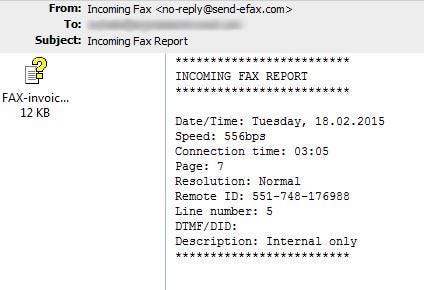
The fake incoming fax report email claims to be from a machine in a user’s domain, which leads us to believe the email targets employees from different organizations to infiltrate company networks.
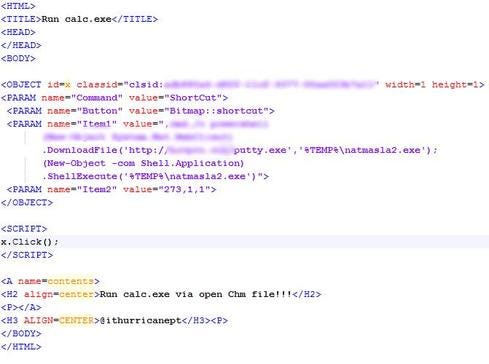
Once the content of the .chm archive is accessed, the malicious code downloads from this location http://*********/putty.exe, saves itself as %temp%\natmasla2.exe, and executes the malware. A command prompt window opens during the process.
CryptoWall is an advanced version of CryptoLocker, a file-encrypting ransomware known for disguising its viral payload as a non-threatening application or file. Its payload encrypts the files of infected computers in an effort to extract money for the decryption key.
Ransomware is one of the most challenging breeds of malware, especially for security companies, which are forced to create increasingly aggressive heuristics to make sure internal data remains private. Learn more about how companies can bolster defenses against ransomware here.
The email blast occurred on the 18th February and targeted a couple hundred users. The spam servers appear to be in Vietnam, India, Australia, the US, Romania, and Spain. After analyzing the recipient domain names, it looks like attackers are after users from around the world, including those in the US, Europe, and Australia.
Bitdefender detects the malware as Trojan.GenericKD.2170937.
How to Prevent Getting Infected with CryptoWall
Bitdefender researchers have made a list of recommendations to prevent CryptoWall infections, including keeping a copy of the data on external drives. Read more about it here. To add extra protection, Bitdefender has also developed the CryptoWall Immunizer, a tool that allows users to immunize their computers and block any file encryption attempt before it happens. Bitdefender recommends users keep their antivirus solution always on and use this tool as an additional layer of protection.
This article is based on spam samples provided courtesy of Bitdefender Spam Researcher Adrian Miron and the technical information provided by Bitdefender Virus Analysts Doina Cosovan and Octavian Minea.
About the Author
You May Also Like


_marcos_alvarado_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)

