Healthcare Organizations Must Consider The Financial Impact Of Ransomware Attacks
Sometimes the impact of an attack can extend well beyond the attack itself.

Intel Security’s five-year threats projection report predicted that ransomware would become a major growth area, given higher ransom “returns” achievable from organizations suffering the potential loss from paralyzed organizational systems. By Q1 of 2016, these predictions have already come true. From February onward this year, press headlines have revealed that numerous healthcare organizations in the United States and around the world have been hit by ransomware attacks. In some cases, these attacks were random instances of individual systems falling prey to commoditized ransomware. But in multiple instances, the attacks were targeted (see https://blogs.mcafee.com/mcafee-labs/targeted-ransomware-no-longer-future-threat). And in at least one case, a healthcare organization chose to pay the ransom.
It’s notable that the healthcare vertical -- the sector that arguably holds the most extensive and non-changeable stores of our most personal, intimate data -- arguably possesses one of the poorest track records for cyberattack preparedness. This poor reputation for preparedness has earned medical clinics, hospitals, and insurance providers the “soft target” label. But as in other industries, an assessment of vertical-specific cyberattack costs can lead to better IT security investments and more effective organizational processes that “harden” these targets.
Besides the paid ransom, what can be said about the other costs that are related to these attacks? Some of the major areas we should examine include:
Lost or stolen record(s) costs
Downtime costs
Incident response and audit/assessment services
A great resource for gauging the value of breaches is the 2015 Ponemon Institute’s Cost of Data Breach study. The report assesses the differences in cost per stolen or lost record by industry, including a healthcare industry approximation of $363 per record.
Healthcare organizations face particularly high stakes in dealing with ransomware because disruptions in availability can jeopardize the core mission of the organization. Surgeries and appointments will be delayed, lab results will take longer, and patients will have to travel to other facilities -- all inconvenient results of systems that were impacted.
Sometimes the impact of a ransomware attack can extend well beyond the attack itself. A study conducted by the AC Group concerning downtime cost calculations of electronic healthcare records gives us an indication. The study assessed several cyberattack factors, including the additional time spent to perform tasks manually and to update records after the systems were up again. The study established an average cost of $488 per hour per physician.
Not every healthcare organization can afford a dedicated incident-response team or an IT security team that executes ongoing assessments of the organization’s assets and applications. The reality is that most healthcare organizations hire an external company for these services after a breach.
Case In Point
Let’s review an example in which a healthcare organization suffered a ransomware outbreak that affected a small number of endpoints and some network data.
The type of breach, extent of damage, and management focus shape the nature and scope of the incident-response engagement. In a ransomware case, the organization would be most interested in determining the scope of the incident (how widespread it is), which systems are targeted, which files are encrypted, and how the attacker breached the organization.
A team of two incident-response consultants onsite with remote expertise support, management overhead, and reporting will easily require a 10-day assignment. Based on our experience, that effort would result in an engagement of $75,000 to $90,000 per incident response. In the case of a compromised application or asset, an audit/assessment would be required, as well as another quick check once the fix was complete. That would easily cost another $20,000 to $25,000.
The following table is a rough approximation of the additional cost and damages for an organization in this scenario.
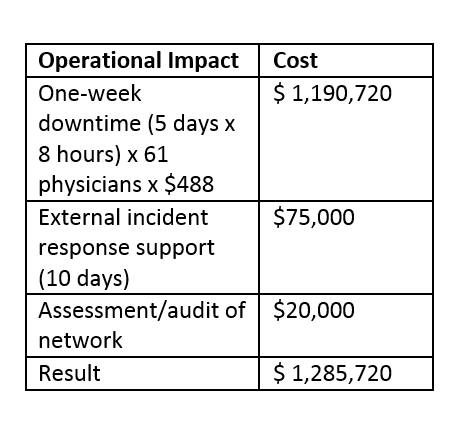
Sources: Intel Security analysis; Ponemon Institute’s Cost of Data Breach study; Modern Healthcare’s annual Hospital Systems Survey.
However, this table shows an incomplete list of costs. On top of these operational impacts are considerations that could include:
Possibly paid ransom
Legal costs
Notification costs
Restoring impacted assets costs
Internal/external communications costs
Overtime costs for IT personnel
Damage to reputation and brand
Regulatory penalties and fines
Increased compliance and audit costs
Lost trust from patients
A ransomware incident as we have described can easily result in a total cost between $700,000 and $1.5 million, depending on the size of the hospital, the impact of ransomware, and whether backups were available.
The Ponemon research notes factors that lower the cost per stolen, lost, or encrypted record. For example, organizations can lower the cost per record by $5.50 by engaging the organization’s board in an effort to prepare for potential attacks. Cybersecurity insurance also appears to reduce damage per record by $4.40. And although few healthcare organizations have budgets for their own dedicated incident-response teams, the engagement of “shared” incident-response teams appears to lower the financial impact by $12.60 per record.
Healthcare organizations should take information security as seriously as they take their mission to provide patients the best possible care. Securing information must have the highest priority so that threats such as ransomware cannot impact the availability of critical systems.
About the Author
You May Also Like



_KonstantinNechaev-Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
