The Secret Behind the NSA Breach: Network Infrastructure Is the Next Target
How the networking industry has fallen way behind in incorporating security measures to prevent exploits to ubiquitous routers, proxies, firewalls, and switches.

Advanced attackers are targeting organizations’ first line of defense--their firewalls—and turning them into a gateway into the network for mounting a data breach. On Aug. 13, the shady “ShadowBrokers” group published several firewall exploits as proof that they had a full trove of cyber weapons. Whether intended to drive up bids for their “Equation Group Cyber Weapons Auction” (since removed), or to threaten other nation-states, the recent disclosure raises the question: if organizations can’t trust their own firewalls, then what can they trust? Does the cache of cyber weapons exposed by ShadowBrokers signal a shift in attack methods and targets?
We analyzed the dump and found working exploits for Cisco ASA, Fortinet FortiGate, and Juniper (formerly NetScreen) firewalls. The names of the exploits provided by the ShadowBrokers match the code names described in Edward Snowden’s 2013 revelations of NSA snooping.
The exploit names are not the only link to the NSA. By analyzing the implementation of a cryptographic function, researchers at Kaspersky have found the same encryption constant used in malware attributed to the Equation Group (Kaspersky’s nickname for the NSA) and python code in the latest breach.
Cyber Attacks with a Side of EXTRABACON
Researching one of the Cisco ASA exploits (dubbed EXTRABACON) in our lab, we found that it’s a simple overflow using SNMP read access to the device. The additional payload bundled with the exploit removes the password needed for SSH or telnet shell access, providing full control over the appliance. The payload can also re-enable the original password to reduce the chance that the attacker will be detected.
The python code handles multiple device versions and patches the payload for the version at hand. This indicates the amount of operations the group had in the past as the developers probably modified the exploit on a case-by-case basis. We ran the exploit against a supported version of a Cisco ASA in our lab multiple times and it didn’t crash once, showing the prowess of the exploit developers.
Our attempt yielded a shell without password protection:
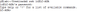
Networking Equipment in the Crosshairs
While the exploits themselves are interesting in their own right, no one is addressing the elephant in the room: attackers increasingly target network infrastructure, including security as a means to infiltrate networks and maintain persistence. While the entire cybersecurity industry is focused on defending endpoints and servers, attackers have moved on to the next weak spot. This advancement underscores the need to detect active network attackers because they can certainly—one way or another—penetrate any given network.
Persisting and working from routers, proxies, firewalls or switches requires less effort than controlling endpoints; attackers don’t need to worry that an anti-virus agent will detect an unusual process, and networking devices are rarely updated or replaced. Most networks have the same routers and switches from a decade ago. Plus, few forensics tools are available to detect indicators of compromise on networking devices and attackers can gain an excellent vantage point within the network.
Network devices vendors have fallen behind operating system vendors in terms of implementing stronger security measures. A wide range of networking equipment still run single-process operating systems without any exploit mitigation enabled (Cisco IOS, I’m looking at you) or exhibit the effects of little to no security quality assurance testing. In recent years, endpoint and mobile operating systems have incorporated security techniques such as address space layout randomization (ASLR), data execution prevention (DEP), sandboxes, and other methods that made life harder for every exploit writer. The affected networking devices provide none of these security mechanisms and it shows.
Not the First and Definitely Not the Last
The Equation Group breach is not the first example of highly capable attackers targeting network devices. The threat actor behind last year’s Hacking Team breach leveraged a vulnerability in a VPN device to obtain full access to their internal network without any obstacles. The attacker moved from the networking device to endpoints without using a single piece of malware, only taking what he needed from endpoints remotely or running well-known administrative tools. This is a soft spot in every endpoint solution’s belly; a privileged attacker using credentials to access files is not considered malicious as long he doesn’t use any malicious software. Notice that as we have stated earlier, the attacker, quoted in pastebin, opted for an embedded exploit and not the other options, stating that it’s the easiest one:
So, I had three options: look for a 0day in Joomla, look for a 0day in postfix, or look for a 0day in one of the embedded devices. A 0day in an embedded device seemed like the easiest option, and after two weeks of work reverse engineering, I got a remote root exploit.
As always, nation-state attacks are usually a step ahead of the entire industry on both the defensive and offensive. We will probably see the same methods employed by less sophisticated attackers as it becomes increasingly difficult to compromise endpoint devices and stay undetected. We have seen this happen before; cybercrime attackers stole techniques from Equation Group, as well as Stuxnet and Flame malware and Reign and other APTs and it will surely happen again with the Equation Group’s recently leaked exploits.
In the meantime, here are four recommendations to help fortify network devices against attack:
Recommendation 1: Patch your network devices promptly. Replace network devices that have reached their end of support date.
Recommendation 2: Restrict access to devices management addresses to the minimum required, and block any unneeded, seemingly benign protocols including SNMP and NTP.
Recommendation 3: Manage your device passwords as you would with your administrator accounts by periodically changing your passwords and defining a different password for each device. Do not use a standard template for passwords. For example, the password Rout3rPassw0rd192.168.1.1 might seem strong, but after compromising one device, the attacker will know all of the passwords.
Recommendation 4: Deploy a network monitoring solution that can profile users and IP-connected devices to establish a baseline of normal behavior and then detect unusual activity originating from network devices. Attackers have no way of knowing what “normal” looks like for any given network and network detection is the only generic way to stop attackers from compromising network devices.
Related Content:
About the Author
You May Also Like




