Artifact Poisoning in GitHub Actions Imports Malware via Software PipelinesArtifact Poisoning in GitHub Actions Imports Malware via Software Pipelines
A vulnerability discovered in GitHub Actions could allow an attacker to poison a developer's pipeline, highlighting the risk that insecure software pipelines pose.
December 1, 2022

An attacker submitting changes to an open source repository on GitHub could cause downstream software projects that include the latest version of a component to compile updates with malicious code.
That's according to software supply chain security firm Legit Security, which said in an advisory published on Dec. 1 that this "artifact poisoning" weakness could affect software projects that use GitHub Actions — a service for automating development pipelines — by triggering the build process when a change is detected in a software dependency.
The vulnerability is not theoretical: Legit Security simulated an attack on the project that manages Rust, causing the project to recompile using a customized — and malicious — version of the popular GCC software library, the company stated in the advisory.
The problem likely affects a large number of open source projects because maintainers typically will run tests on contributed code before they actually analyze the code themselves, says Liav Caspi, chief technology officer of Legit Security.
"It is a common pattern today," he says. "A lot of open source projects today, upon a change request, they run a bunch of tests to validate the request because the maintainer does not want to have to review the code first. Instead, it automatically run tests."
The attack takes advantage of the automated build process through GitHub Actions. In the case of the Rust programming language, the vulnerable pattern could have allowed an attacker to execute code in a privileged way as part of the development pipeline, stealing repository secrets and potentially tampering with code, Legit Security said.
"To put it simply: in a vulnerable workflow, any GitHub user can create a fork that builds an artifact," the company stated in its advisory. "Then inject this artifact into the original repository build process and modify its output. This is another form of a software supply chain attack, where the build output is modified by an attacker."
The vulnerability enables an attack similar to the malware-insertion attack that targeted CodeCov and, through that company's software, its downstream customers.
"[T]he lack of native GitHub implementation for cross-workflow artifacts communication led many projects and the GitHub Actions community to develop insecure solutions for cross-workflow communication and made this threat highly prevalent," Legit Security stated in the advisory.
GitHub confirmed the issue and paid a bounty for the information, while Rust fixed its vulnerable pipeline, Legit Security stated.
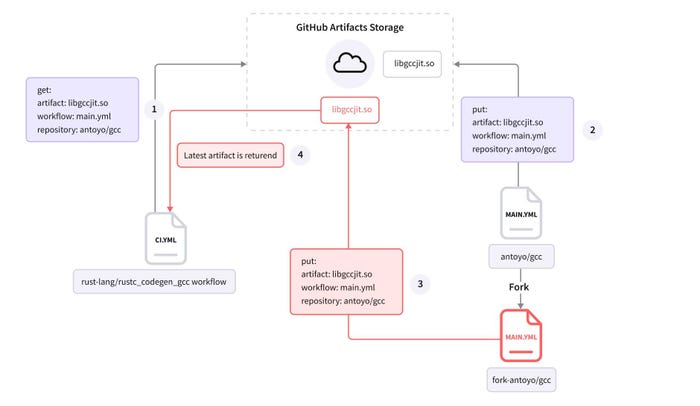
Source: Legit Security
Software Supply Chain Needs Security
The vulnerability is the latest security issue to affect software supply chains. Industry and government agencies have increasingly sought to bolster the security of open source software and software provided as a service.
In May 2021, for example, the Biden administration released its executive order on Improving the Nation's Cybersecurity, a federal rule that, among other requirements, mandates that the government will require baseline security standards for any software its purchases. On the private industry side, Google and Microsoft have pledged billions of dollars to shore up security in the open source ecosystem, which provides the code that comprises more than three-quarters of the average application's codebase.
Logical, But Vulnerable
The security issue belongs to a hard-to-find class of problems known as logic issues, which include issues with permissions, the potential for forked repositories to be inserted into a pipeline, and a lack of differentiation between forked and base repositories.
Because software projects often use automated scripts to check code submissions before forwarded them to the maintainers, pull requests will be run through automation before any human checks them for malicious code. While the automation saves time, it also should be considered a way for attackers to insert malicious code into the pipeline.
"When you are doing open source development, the problem is bigger, because you are accepting contribution from anyone in the world," Caspi says. "You are executing things that you cannot trust."
GitHub acknowledged the issue and expanded the ways of excluding submissions from outside collaborators from being automatically inserted into the Actions pipeline. The company updated its GetArtifact and ListArtifacts APIs with the goal of providing more information to help determine whether an artifact can be trusted.
"Anyone that does anything like the Rust project did — trusting the input from a third party — then they are still vulnerable," Caspi says. "It is a logic problem. GitHub just made it easier to write a safer script."
About the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025




_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)