Supply Chain Attackers Escalate With GitHub Dependabot Impersonation
Armed with stolen developer passcodes, attackers have checked in changes to repositories under the automation feature's name in an attempt to escape notice.
September 28, 2023

In the latest attack to target software supply chains, attackers managed to slip in malicious code updates to hundreds of GitHub repositories by using stolen passcodes to commit changes and then used the name of a well-known tool, Dependabot, to convince developers to accept those updates.
The campaign abused stolen personal access tokens (PATs) — security credentials used to verify the authenticity of a code update — to check code into the GitHub repositories, using a known technique to spoof the name of the contributor, according to an advisory published Sept. 27 by software security firm Checkmarx. The attacks added code to the end of Javascript files that would load and execute code from the attacker's site.
The additional step of labeling the code submissions — or "commits" in developer lingo — is new and could fool unwary developers, says Guy Nachshon, a security researcher at Checkmarx.
"The attacker plants code changes to appear as if they were made by Dependabot — so the victim won't deep dive into the code changes," he says. "This is a software supply chain attack and the first time we've witnessed such a deception technique with the impersonation of Dependabot."
The attack is the latest to target developers in general, and the GitHub platform in particular, as a way to insert malicious code into the software supply chain. In November, attackers stole code from Dropbox's GitHub repositories by convincing a developer to enter their credentials and their two-factor authentication code into a phishing site. In December, another attacker created a malicious Python package that impersonated a software development kit for a popular security client.
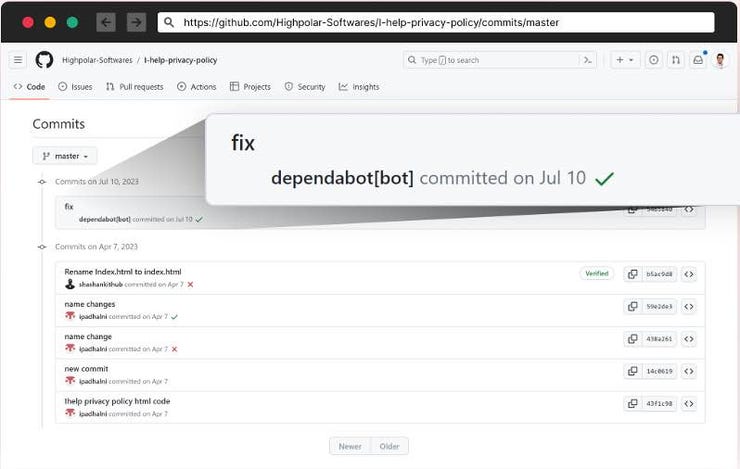
Dependabot message on Github repository. Source: Checkmarx
These types of attacks are not unique to GitHub. The company has repeatedly seen threat actors attempt to use impersonation as a way to trick users into trusting a code commit and often paired with a stolen PAT. The Microsoft company stressed that the issue was not with its service.
"GitHub's systems were not compromised in this attack and there is no evidence to suggest GitHub users are at risk," says a GitHub spokesperson. "Unfortunately bad actors will attempt to compromise personal data and private information wherever they can find it."
Dependabot's Trusted Identity
GitHub bought Dependabot in 2019 when it was still in preview and has developed the automated tool as a way to perform regular software and security checks for projects hosted on the GitHub service. Since then, GitHub has added features, such as automatic triage of updates for known vulnerabilities and a variety of alert-rules engines.
The attackers could have submitted the code under any name, but by using Dependabot, they gain a certain amount of trust, says Nicolas Danjon, a security researcher at repository-scanning firm GitGuardian.
"Dependabot is an automated process that will add some merge requests to your projects to update your dependencies," he says. "And so, as a developer, if you see a request that comes from Dependabot, you're not even going to check the code — you just accept it, because you trust the source."
While labeling the code commits as coming from Dependabot may fool the developer, the actual code submission is made possible by the theft of PATs passcodes, according to the Checkmarx advisory. Without those PATs, the threat is significantly reduced, says Checkmarx's Nachshon.
"Unless their credentials, such as personal access tokens, are stolen by threat actors, GitHub, GitLab, and such users are not affected by the risk demonstrated in this report," he says. "Developers should secure their accounts and implement the principle of least privilege by using fine-grained tokens instead of classic tokens."
Protect Credentials to Secure Supply Chains
Developers should make sure that they harden their software development pipelines against attacks, especially ensuring that the simple theft of a credential could lead to code compromise. GitHub has already started scanning all public repositories for developer secrets, such as passwords and security tokens, and has required two-factor authentication on all developer accounts.
The impersonation attack shows that developers should rely on more than just project attributes — such as the number of developers and number of commits — to determine whether a project is trustworthy. In 2022, researchers showed that several of the signals and metadata used to decide whether a software project is trustworthy could be forged, fooling developers into downloading malicious code.
Companies should not only protect their development secrets, but also use honey tokens — a deception defense that sprinkles fake credentials throughout developers' environments — to detect when attackers are trying to use invalid identities, says GitGuardian's Danjon. Finally, developers should analyze the code from the packages they are using to determine if any malicious code has been inserted into the supply chain.
Checkmarx's Nachshon also had a recommendation for GitHub. The company should allow every user to see their security access logs, he says. Currently, the company only provides that ability to those who have access features for enterprise users.
About the Author
You May Also Like




