The New Frontier in Email Security: Goodbye, Gateways; Hello, Behavioral AI
As email attackers move to more targeted and sophisticated attacks, email security needs to understand the organization, not past attacks, to keep up with attacker innovation and stop novel threats on the first encounter.
April 24, 2023

In an evolving threat landscape email remains the primary target for cyberattacks, and traditional methods of email security are no longer adequate. Solutions that rely on historical attack data can only catch what they've seen before and remain inevitably on the back foot, racing to match the pace of innovation of cybercriminals — in fact, they take an average of 13 days to recognize novel attacks.*
An Escalating Threat Landscape
Phishing attacks are advancing in frequency and sophistication as attackers experiment with two key ingredients: malware delivery and social engineering. Regarding delivery, there is a surge in cybercriminals "hitching a ride" off legitimate infrastructure like OneDrive and SharePoint to conceal malware, exploiting their trusted reputations to bypass security tools. On the human side, attackers are using generative AI technologies to impersonate trusted contacts — including damaging business email compromises and realistic spear-phishing. Worryingly, Darktrace found that the average linguistic complexity of phishing emails has increased by 17% since the release of ChatGPT.
These trends demonstrate a shift in the attack landscape: from high-frequency, low-impact, generic phishing tactics to more targeted, sophisticated, and higher-impact attacks that can evade security tools relying on rules and signatures.
.jpg/?width=700&auto=webp&quality=80&disable=upscale)
Figure 1: The progression of attacks and relative coverage of email security tools.
What's more, email security for the digital age needs to stretch beyond the inbox, for a full picture of every user across their email, account, and apps. Effectively, tools that only focus on blocking known threats from the inbox are no longer enough.
The Industry Picture
Traditional gateways and many modern integrated cloud email security (ICES) providers have something in common: They look to previous threat intelligence in order to predict the next attack. Some newer vendors apply AI to this flawed approach, looking for direct matches and using "data augmentation" to identify similar-looking emails. Despite leveraging AI, this approach is still historically focused and therefore blind to novel threats.
These tools are also resource-intensive, requiring continuous policy maintenance and manual triage of held-but-legitimate emails. The stage is set for email security that autonomously separates bad from good and continuously adapts to every organization — technology that fits the definition of "set and forget".
The Shift Toward Behavioral AI
The industry is experiencing a seismic shift from "secure" email gateways to intelligent AI-driven approaches.
Only a complex understanding of each employee's everyday interactions can accurately determine whether or not an email belongs in their inbox. This approach understands behaviors — how each person uses their inbox and what constitutes 'normal' for each user — in order to detect what's not normal.
Within the threat landscape, this approach builds on native email security to tackle the high-level attacks that use novel or seemingly legitimate infrastructure.
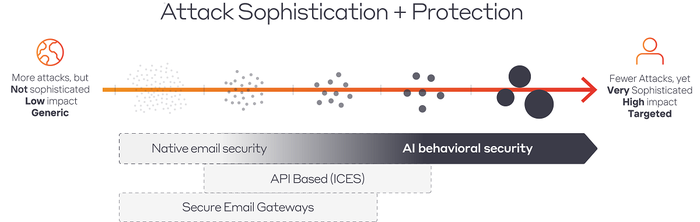
Figure 2: Native email security plus AI covers more types of attacks.
Full confidence in detection allows for a precise and targeted response — action that removes only the riskiest parts of an email rather than taking a blanket ban out of caution — to minimize risk without disrupting normal business operations.
A Full Picture for Every User
Existing email tools focus solely on inbound email, which doesn't take into consideration the significant potential damage of an account compromise. Today's email security can't be limited to the inbox alone — it needs to comprise a full understanding of a user's behavior across email and beyond.
To have complete context of a single user, it's crucial to understand their activity on apps, networks, and devices for a full-picture view of identity-based attacks. Understanding a user in the context of their organization — including network, cloud, and endpoint data — connects email security with the enterprise and external attack surface for a richer picture of potential attacks.
Bringing the End User Into the Loop
In the digital age, security is everyone's responsibility. Email security needs to educate and engage employees at the right level, giving them the context they need to make the right decisions, without overwhelming them or giving them too much control.
The tools that succeed best will be those that can leverage AI to improve employees' security consciousness — with contextual banners, explainable digests, and bespoke actions to neutralize risky elements — bringing the end user into the loop to harden defenses. By empowering employees with information, while still leaving critical decisions to the security team, organizations can further strengthen their security posture, while lifting security teams out of firefighting mode towards higher-level more strategic decision-making .
The new frontline of email security fights cybercrime with intelligent AI, and organizations that fail to get ahead of the curve may end up paying the price. For CISOs, the question is not if they should upgrade their email protections, but when – how much longer can they risk depending on email security that's stuck in the past?
About the Author
.png/?width=700&auto=webp&quality=80&disable=upscale)
As VP of Product at Darktrace, Dan Fein has helped customers quickly achieve a complete and granular understanding of Darktrace's product suite. Dan has a particular focus on Darktrace email, ensuring that it is effectively deployed in complex digital environments, and works closely with the development, marketing, sales, and technical teams. Dan holds a bachelor's degree in computer science from New York University.
*Thirteeen days mean average of phishing payloads active in the wild between the response of Darktrace/email compared to the earliest of 16 independent feeds submitted by other email security technologies. (https://darktrace.com/news/darktrace-email-defends-organizations-against-evolving-cyber-threat-landscape)
You May Also Like


