Cyberattackers Abuse Facebook Ad Manager in Savvy Credential-Harvesting CampaignCyberattackers Abuse Facebook Ad Manager in Savvy Credential-Harvesting Campaign
Facebook lead-generation forms are being repurposed to collect passwords and credit card information from unsuspecting Facebook advertisers.
September 13, 2022

Attackers are piggybacking on the power of the Facebook brand by using emails that look like they're coming from Facebook Ads Manager. The idea is to lure victims into coughing up credentials and credit card information on a Facebook lead generation form.
According to a Tuesday report by the security research team at Avanan, attackers are sending phishing messages that appear to be urgent warnings from Meta's "Facebook AdManager" team. The messages claim the victim is not complying with the company's ad policies and that the ad account will be disabled if the target doesn't appeal the phony violation.
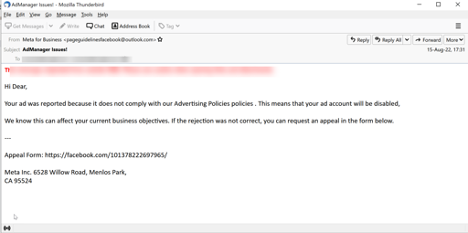
The Facebook Ads phishing message. Source: Avanan
The "appeal form" link leads to a credential harvesting site that uses a real Facebook lead-generation form to collect passwords and credit card information.
Abusing the Facebook Ads System
An interesting aspect to the campaign is that rather than using a harvesting site hosted on a sketchy IP somewhere, attackers are gaming the Facebook ads system to create lead-generation forms with malicious intent. Doing so kills two birds with one stone: First of all, it fools a lot of automated checks for malicious links used by email platforms. Using legitimate sites is what the Avanan team refers to as the Static Expressway.
"Hackers are leveraging sites that appear on static Allow Lists," explained Jeremy Fuchs, cybersecurity researcher for Avanan, in the report. "That means that email security services have broadly decided that these sites are trustworthy, and thus anything related to them comes through to the inbox."
Additionally, using Facebook Ads forms also offers a high degree of verisimilitude for any of the eight billion advertising users that Facebook works with who are already familiar with the Ads Manager platform and the lead-generation forms it produces.
"For the end user, seeing that their Facebook ad account has been suspended is cause for concern," Fuchs said. "Since it’s a legitimate Facebook link, the user would feel confident continuing on."
Tell-Tale Signs of 'Brandjacking'
Fuchs wrote that while the sites used in this credential harvesting campaign appeared to be legitimate, there is a red flag in the phishing messages they uncovered: Typically, these are coming from Outlook accounts such as [email protected].
Additionally, the physical address footer in the emails are wrong. But if users didn't notice these details, they could easily be foiled by this ploy.
According to research released earlier this year, brand impersonations, or brandjackings, like these increased by 274% last year as attackers continue to peddle their scams by looking like they come from reliable sources. Facebook is a particular favorite among phishers to impersonate. A report released by Vade this spring found Facebook was the No. 1 impersonated brand last year, edging out perennial favorite Microsoft for the top spot.
According to Abnormal Security research detailing data from the first half of 2022, email attacks increased by 48% in that timeframe, with more than 1 in 10 attacks impersonating well-known brands. Some 256 individual brands were impersonated, with LinkedIn and Microsoft appearing to be the favorites so far in 2022.
About the Author
You May Also Like




