DOS Attacks Dominate, but System Intrusions Cause Most PainDOS Attacks Dominate, but System Intrusions Cause Most Pain
In the latest Verizon "Data Breach Investigations Report," denial-of-service attacks are the most common type of security incident, but when it comes to breaches, nearly four-in-ten attackers compromise systems.
June 9, 2023

Denial-of-service attacks continued to dominate the threat landscape in 2022, but breaches — those security incidents that resulted in confirmed data loss — more likely included system intrusions, basic Web application attacks, and social engineering.
Out of more than 16,300 security incidents analyzed in Verizon's "2023 Data Breach Investigations Report," more than 6,250, or 38%, were denial-of-service attacks, while almost 5,200, or 32%, were confirmed data breaches. While the denial-of-service attacks were disruptive until they were mitigated — much of the data in the report came from DOS defense providers rather than victims — data breaches through system intrusions, web application compromises, and social engineering usually resulted in significant impacts on business.
The two top attack types in the report — DOS attacks and system intrusions — target different parts of the CIA (Confidentiality, Integrity, Availability) triad. System intrusions typically affect confidentiality and integrity, while denial-of-service attacks target availability, says Erick Galinkin, principal researcher at vulnerability management firm Rapid7.
"Ultimately, the use of DDoS is to put pressure on a target and force them to focus on getting availability back up," he says. "This can be used as part of an extortion campaign, to distract a target from contemporaneous compromise attempts, or even as a standalone tactic to disrupt some target."
The data highlights the differences in threat activities that become notable incidents and those that cause real harm to companies. The damage caused by the average ransomware incident, which accounted for 24% of all breaches, doubled to $26,000, according to the report. In contrast, only four of the 6,248 denial-of-service incidents resulted in data disclosure, the "2023 Data Breach Investigations Report" stated.
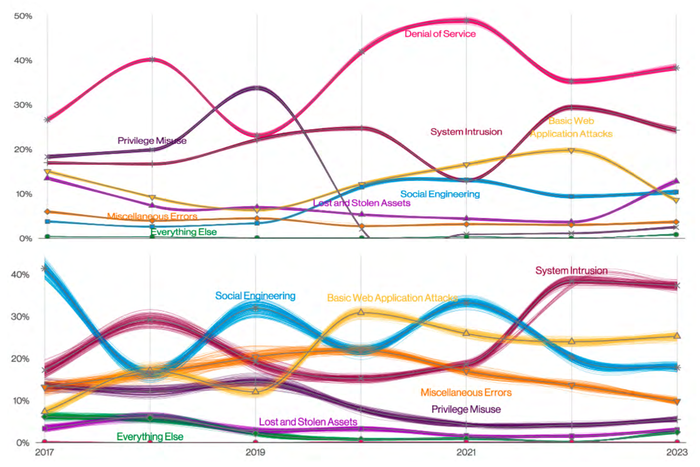
Denial-of-service attacks dominated incidents (top) while system intrusions dominated breaches. Source: 2023 Verizon DBIR
The report also underscored the fact that while patterns are informative, they can also vary widely, says Joe Gallop, intelligence analysis manager at Cofense, an e-mail security company.
"Every incident is different, making it very difficult to come up with an exhaustive and exclusive, yet detailed set of incident categories," he says. "Because of the overlap between various methods, and the potential for an attack chain to cycle between activities that might fall under several categories, it is extremely important to maintain a holistic approach to security."
More System Intrusions, Because More Ransomware
The most common pattern in the system intrusion category is malicious software installed on a computer or device, followed by data exfiltration, and, finally, attacks on the availability of a system or data — all hallmarks of ransomware attacks. In fact, ransomware accounted for more than 80% of all actions in the system-intrusion category, according to the DBIR.
Because of the continued popularity of ransomware, the system intrusion pattern should be one the companies focus on detecting, says David Hylender, senior manager of threat intelligence at Verizon.
"The primary reason that system intrusion has risen to the top is the fact that it is the pattern where ransomware resides," he says. "As ransomware continues to be ubiquitous among organizations of all sizes, verticals, and geographic locations, the system intrusion pattern continues to grow."
Yet, other vectors of attacks are also leading to breaches, including basic Web attacks and social engineering. A quarter (25%) of breaches were caused by basic Web application attacks, while 18% of breaches were caused by social engineering. And within the system intrusion category, attacks through Web applications accounted for a third of all attacks that resulted in a system intrusion.
Employees Critical to Defense
An incident that starts as social engineering can quickly turn into a system intrusion as the attack chain progresses. In fact, the blending of incidents make protecting systems and data against breaches a very holistic exercise, says Rapid7's Galinkin.
The defensive strategy also depends on what organizations value. In a healthcare setting, a DDoS attack will usually impact public-facing resources, such as payment or scheduling portals, which are critical, but might not impact the core functionality of patient care, he says.
"The things an individual organization values can vary wildly," Galinkin says. "Thus, it's important for organizations to consider what their most important resources and assets are, and then evaluate how different threats may target those resources. Ultimately, that will inform the best defense."
Yet, because social engineering has such a broad footprint across different breach types, employees are a critical piece of the defensive puzzle, says Cofense's Gallop.
"Since 74% of all breaches in the report included a human element, addressing human vulnerabilities is critical," he says. "Employees should be trained to be skeptical of social engineering attempts, to recognize suspicious links, and to never share credentials."
About the Author
You May Also Like



_Nils_Ackermann_Alamy_Stock_Vector_.jpg?width=700&auto=webp&quality=80&disable=upscale)
