Everybody Wants Least Privilege, So Why Isn't Anyone Achieving It?Everybody Wants Least Privilege, So Why Isn't Anyone Achieving It?
Overcoming the obstacles of this security principle can mitigate the damages of an attack.

When I was forming the idea for the company that would become Veza, my co-founders and I interviewed dozens of chief information security officers (CISOs) and chief information officers (CIOs). No matter the size and maturity of their modern tech-savvy companies, we heard one theme over and over: They could not see who had access to their company's most sensitive data. Every one of them subscribed to the principle of least privilege, but none of them could say how close their company came to achieving it.
"Least privilege" is defined by NIST's Computer Security Resource Center as "the principle that a security architecture should be designed so that each entity is granted the minimum system resources and authorizations that the entity needs to perform its function." That sounds simple, but things have changed. Data is now spread across multiple clouds, hundreds of SaaS apps, and systems old and new. As a result, all modern companies accumulate "access debt" — unnecessary permissions that were either too broad in the first place or no longer necessary after a job change or termination.
A KPMG study found that 62% of US respondents experienced a breach or cyber incident in 2021 alone. If any employee falls prey to phishing, but they only have access to non-sensitive information, there may be no economic impact at all. Least privilege mitigates the damage of an attack.
There are three obstacles to achieving least privilege: visibility, scale, and metrics.
Visibility Is the Foundation
It's hard to manage something you can't see, and access permissions are spread across countless systems in the enterprise. Many are managed locally within the unique access controls of a system (e.g., Salesforce admin permissions). Even when companies implement an identity provider, such as Okta, Ping, or ForgeRock, this only shows the tip of the iceberg. It cannot show all the permissions that sit below the waterline, including local accounts and service accounts.
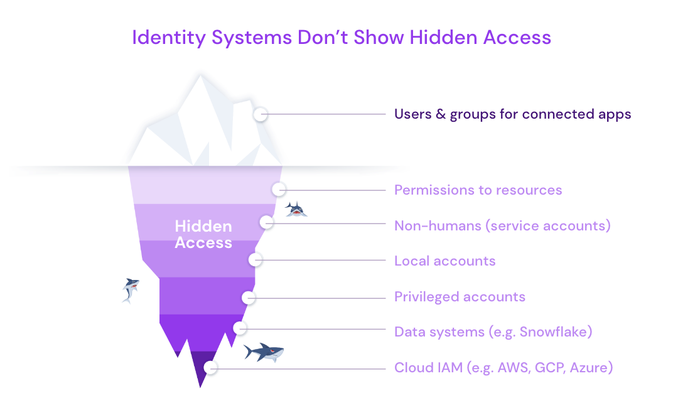
Source: Veza
This is especially relevant today, with so many companies conducting layoffs. When terminating employees, employers revoke access to the network and SSO (single sign-on), but this does not propagate all the way to the myriad systems in which the employee had entitlements. This becomes unseen access debt.
For companies where legal compliance mandates periodic access reviews, visibility is manual, tedious, and vulnerable to omissions. Employees are dispatched to investigate individual systems by hand. Making sense of these reports (often, screenshots) might be possible for a small company, but not for one with a modern data environment.
Scale
Any company might have thousands of identities for employees, plus thousands more for non-humans, like service accounts and bots. There can be hundreds of "systems," including cloud services, SaaS apps, custom apps, and data systems such as SQL Server and Snowflake. Each offers tens or hundreds of possible permissions on any number of granular data resources. Since there is an access decision to make for every possible combination of these, it's easy to imagine the challenge of checking a million decisions.
To make the best of a bad situation, companies take a shortcut and assign identities to roles and groups. This addresses the scale problem but worsens the visibility problem. The security team might be able to see who belongs to a group, and they know the label on that group, but labels don't tell the whole story. The team can't see access at the level of tables or columns. When identity access management (IAM) teams are receiving a never-ending stream of access requests, it's tempting to rubber stamp approvals for the closest-fit group, even if that group confers broader access than necessary.
Companies can't overcome the scale challenge without automation. One solution is time-limited access. For example, if an employee was given access to a group but doesn't use 90% of the permissions for 60 days, it's probably a good idea to trim that access.
Metrics
If you can't measure it, you can't manage it, and nobody today has the tools to quantify how much "privilege" has been granted.
CISOs and their security teams need a dashboard to manage least privilege. Just as Salesforce gave sales teams the object model and dashboards to manage revenue, new companies are creating the same foundation for managing access.
How will teams quantify their access? Will it be called "privilege points"? Total permission score? A 2017 paper coined a metric for database exposure called "breach risk magnitude." Whatever we call it, the rise of this metric will be a watershed moment in identity-first security. Even if the metric is an imperfect one, it will shift a company's mindset toward managing least privilege like a business process.
Going Forward
The landscape has changed, and it has become practically impossible to achieve least privilege using manual methods. Fixing this will require new technologies, processes, and mindsets. The CISOs and CIOs I work with believe least privilege is possible, and they're making prudent investments to move beyond the bare minimum of quarterly access reviews. It won't be long before manual reviews are a thing of the past, and automation tames the complexity of modern access control.
About the Author
You May Also Like



_Nils_Ackermann_Alamy_Stock_Vector_.jpg?width=700&auto=webp&quality=80&disable=upscale)
