Top Application Security Mitigations in Q1 of 2022
What is the best way to mitigate application security attacks? Learn how companies have mitigated the top threats.
April 7, 2022

In this article, we present some best practices to mitigate attacks. We pay special attention to bots and APIs, but you can find broader attack patterns anytime at radar.cloudflare.com.
When looking at global threats, these are the top Cloudflare mitigation measures that were used from January 2022 to March 2022 to keep customer sites and applications online, as well as secure.
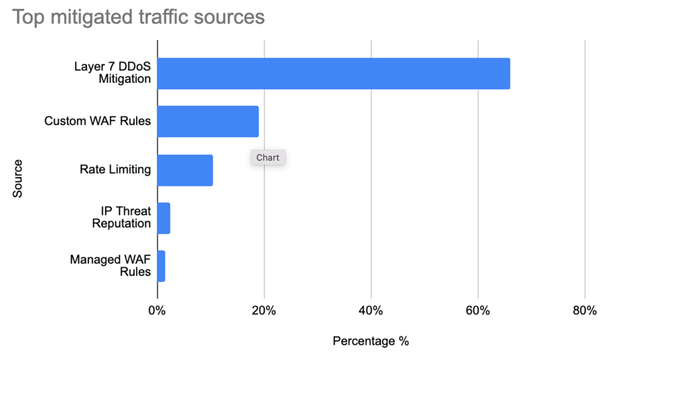
Source: Cloudflare
Looking at each mitigation source individually:
66% were Layer 7 DDoS mitigation; unsurprisingly, this group is the largest contributor to mitigated HTTP requests. Cloudflare's layer 7 DDoS rules are fully managed and don't require user configuration: They automatically detect a vast array of HTTP DDoS attacks. Volumetric DDoS attacks, by definition, create a lot of malicious traffic!
19% were due to Custom WAF Rules. These are user-configured rules defined using Cloudflare's wirefilter syntax.
10.5% were contributed by Rate Limiting. Rate Limiting allows customers to define custom thresholds based on application preferences. It is often used as an additional layer of protection for applications against traffic patterns that are too low to be detected as a DDoS attack.
IP Threat Reputation is exposed in the Cloudflare dashboard as Security Level. Based on behavior we observe across the network, Cloudflare automatically assigns a threat score to each IP address. When the threat score is above the specified threshold, we challenge the traffic. This accounts for 2.5% of all mitigated HTTP requests.
Our Managed WAF Rules match only against valid malicious payloads. They contribute to about 1.5% of all mitigated requests.
Bot Traffic Insights
Using Bot Management classification data, customers gain insight into the automated traffic that might be accessing their application.
38% of HTTP Traffic Is Automated
Over the time period analyzed, bot traffic accounted for about 38% of all HTTP requests. This traffic includes bot traffic from hundreds of bots tracked by Cloudflare, as well as any request that received a bot score below 30, indicating a high likelihood that it is automated.
Overall, when bot traffic matches a security configuration, customers allow 41% of bot traffic to pass to their origins, blocking only 6.4% of automated requests. This includes traffic coming from verified bots like Googlebot, which benefit site owners and end users.
API Traffic Highlights
Due to the underlying format of the data in transit, API traffic tends to be a lot more structured than standard Web applications, causing all sorts of problems from a security standpoint. First, the structured data often causes Web application firewalls (WAFs) to generate a large number of false positives. Second, due to the nature of APIs, they often go unnoticed, and many companies end up exposing old and unmaintained APIs without knowing, often referred to these as "shadow APIs."
Below, we look at some differences in API trends compared with the global traffic insights shown above.
10% of API Traffic Is Mitigated
A good portion of bot traffic is accessing API endpoints. API traffic is the fastest-growing traffic type on the Cloudflare network, currently accounting for 55% of total requests.
APIs globally receive more malicious requests compared with standard Web applications (10% vs. 8%), potentially indicating that attackers are focusing more on APIs for their attack surface as opposed to standard Web apps.
DDoS mitigation is still the top source of mitigated events for APIs, accounting for just over 63% of the total mitigated requests. More interestingly, Custom WAF rules account for 35% compared with 19% when looking at global traffic. Customers have, to date, been heavily using WAF Custom Rules to lock down and validate traffic to API endpoints, although we expect our API Gateway schema validation feature to soon surpass Custom WAF Rules in terms of mitigated traffic. This is important considering SQLi is the most common attack vector on API endpoints.
Start With Attack Protection
In the first quarter of this year, governments, companies, and individuals experienced cyberattacks of increasing complexity. These mitigation insights underline the need to explore the proper way to block attacks without altering or slowing down the business of the day. Learn more about how to manage security posture.
About the Authors

Michael Tremante is a London-based product manager at Cloudflare for WAF (Web application firewall). He considers Web security and performance "nice added perks of my job." He keeps busy with side projects at dodify and Spesati, where he's also a sys admin, front-end developer.

Sabina Zejnilovic is a Cloudflare Data Scientist from Sarajevo, Bosnia and Herzegovina, and with industry and academic experience. She is a dual-degree Ph.D. in Electrical and Computer Engineering (ECE), at Instituto Superior Técnico of the Universidade Técnica de Lisboa (IST/UTL) and Carnegie Mellon University (CMU).

David Belson is Head of Data Insight at Cloudflare and has more than 25 years' experience in the Internet infrastructure space, including Content Delivery Networks, DNS, and Web hosting. He has also been generating thought leadership and earned media coverage based on Internet measurement and monitoring data for over a decade.
You May Also Like


