Microsoft Azure-Based Kerberos Attacks Crack Open Cloud Accounts
Two common attacks against on-premises Kerberos authentication servers — known as Pass the Ticket and Silver Ticket — can be used against Microsoft's Azure AD Kerberos, a security firms says.
January 25, 2023

Microsoft's Azure AD Kerberos service, a cloud-based identity and access management (IAM) service based on Kerberos authentication, can be attacked using techniques similar to those used by attackers against on-premises Kerberos servers.
Kerberos is a widely used protocol used to authenticate users and devices via symmetric key cryptography and a key distribution center; it enables modern authentication mechanisms such as single sign-on (SSO). Because Kerberos authentication is a standard security measure for many enterprises, attackers have frequently tried to compromise or bypass the authentication servers using identity attacks that spoof legitimate users.
In the on-premises world, a pair of common identity attacks are the Pass the Ticket and Silver Ticket approaches, which allow an attacker to use stolen credentials or mint their own credentials, respectively, and authenticate with enterprise services. Both techniques continue to work to some degree against the cloud versions of Kerberos authentication servers, according to cybersecurity services firm Silverfort, which dubbed the cloud-based iterations of the attacks the Bounce the Ticket and Silver Iodide threats.
"Identity attacks that have existed for some time are still a risk as organizations move into the cloud," says Dor Segal, senior security researcher at the firm. "Azure AD Kerberos is a new implementation but not a new protocol. Security teams need to be aware of this fact and put appropriate mitigations in place."
The fact that variants of the two attacks still work in the cloud show that moving security infrastructure to the cloud has little impact on the threat, Segal says.
"The issues outlined could impact anyone using the new Azure AD Kerberos protocol," he says. "While Azure AD Kerberos is still in initial stages of adoption, as with anything released by Microsoft, the scale of usage will increase. In the past, this type of lateral movement was an issue affecting the on-premises enterprise network. These [new] attacks break this perimeter."
Microsoft added Kerberos functionality to its Azure Active Directory service last August, and attackers are sure to follow, Silverfort argued in a research report issued Jan. 25. After all, IAM systems have become linchpins for many companies' zero-trust security efforts, with Microsoft Active Directory, for example, a target of attacks in nine out of 10 incidents. In addition, Kerberos is a frequent target of attackers, who often go after "tickets" — i.e., encrypted authentication credentials or tokens, used by the Kerberos protocol as proof that a client or device has authenticated to the server.
A successful attempt to duplicate a ticket gains attackers access to protected resources for a limited time, generally on the order of hours, allowing them to move around a corporate network or use SSO services like email that might be protected by the Kerberos credential.
Bouncing & Silver Tickets
In the first attack, dubbed a Bounce the Ticket attack, an attacker who has compromised one user's system and who steals a Kerberos ticket from the machine's memory can then then use the secret key to gain access to cloud workloads. This attack bears similarities to the on-premises Pass the Ticket attack on Kerberos authentication services and gives the attack the ability to "access cloud-based resources that rely on Azure AD Kerberos," according to Silverfort's research.
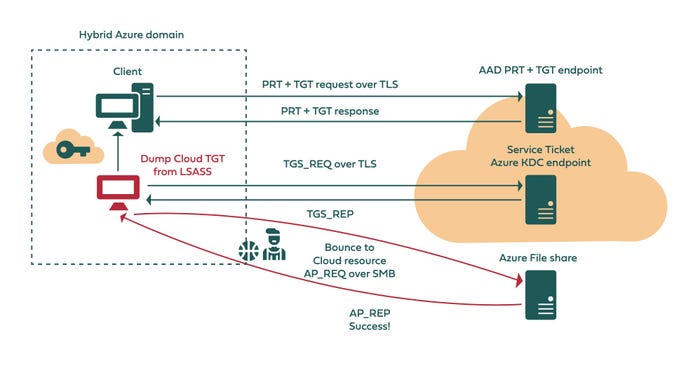
The Bounce the Ticket attack flow. Source: Silverfort
In the second attack, dubbed a Silver Iodide attack, an attacker who gains access to one user's Azure AD account can connect to a specific service — in the example given by Silverfort, the Azure Files cloud sharing service — after finding a "security gap" in the service. Specifically, in Azure, the "Get-AzStorageAccountKey" command returns the access keys for an Azure Storage account. Those keys can then be used to create a new server ticket to access or manipulate information. The technique resembles the Silver Ticket attack against on-premises Kerberos servers.
"The attacker doesn’t necessarily need to have permission to the resource to run the Get-AzStorageAccountKey command," Segal explains. "While in our opinion, it does need to be fixed, Microsoft does not consider obtaining the key using a weak admin a vulnerability."
Unlike the first attack, Silver Iodide might be Microsoft-specific, he adds.
"This specific approach does not necessarily work in any cloud workload, it is specific to Azure Files," he notes. "Additional cloud workloads would need to be examined on a case-by-case basis to see if Silver Iodide could be applied to them."
No Fix Ahead
Overall, the two issues represent ways an attacker — who has compromised either a system on the network or an Azure AD account — could recover Kerberos tickets and reuse those secrets to extend access to other infrastructure.
Silverfort disclosed the issues to Microsoft, and while the company is aware of the weaknesses, it does not plan to fix them, because they are not "traditional" vulnerabilities, Segal says. Microsoft also confirmed that the company does not consider them vulnerabilities.
"This technique is not a vulnerability, and to be used successfully a potential attacker would need elevated or administrative rights that grant access to the storage account data," a Microsoft spokesperson tells Dark Reading. "We recommend customers regularly review their role definitions that include 'listkeys' permissions, and enable software that prevents attackers from stealing credentials, such as Credential Guard."
Silverfort's Segal acknowledges that to fix the issues, the Kerberos protocol would have to be redesigned, and that is unlikely.
"Fixing a weakness in any implementation of Kerberos is not as straightforward as patching a traditional software vulnerability because it would require re-engineering the entire protocol," he says. "This would be a significant undertaking which would take a large amount of resource and impact the compatibility of legacy applications using Kerberos."
Companies can make it harder to exploit any security weakness in their cloud-based Kerberos infrastructure, however. Organizations should review any changes to the Azure Access Control service and monitor updates to the permissions. Reducing the number of systems authorized to hold some of the more critical cloud-based credentials — such as the Ticket-Granting Ticket (TGT) — will harden an enterprise's infrastructure to Bounce the Ticket attacks, Silverfort stated in its report.
About the Author
You May Also Like




