How Proactive Threat Hunting Redefines the Zero-Day
Threat hunters are continuously and actively scouring the environment for clues of a malicious incursion.

Amidst record volumes of vulnerabilities, the field of threat hunting is redefining what “zero-day” means for organizations. Proactive and systematic hunting for post-exploitation behavior ensures there is never a “time before the threat” — threat hunters are continuously and actively scouring your environment for clues of a malicious incursion.
For most parties involved, the disclosure of a vulnerability is like the starter pistol going off in a race. Every minute counts as adversaries rush to exploit the vulnerability, organizations scramble to patch, and security vendors quickly adapt their automated detection and prevention tools.
In the midst of such chaos, threat hunters are steadily running their own race — and winning. Because while the rest of the pack waits for the starter pistol to sound on a new vulnerability, threat hunters are already out there proactively hunting for post-exploitation behavior and looking for signs of the adversary, wherever and however they invade a victim’s environment. They are looking for someone probing Active Directory, spawning processes through webshells, creating new accounts, and using other adversary techniques. This systematic and scalable approach to finding threats provides an effective defense against the unknown.
Humans at the Cutting Edge of Attack and Defense
Human ingenuity is at the heart of every threat. It takes originality to find ways to misuse or circumvent systems, and it takes expertise to do so in a way that evades existing technology-based detections. Threat hunting focuses squarely on the human element in order to stay a step ahead of the adversary.
Threat hunters harness their own ingenuity to uncover threats in ways that automated and technology-based solutions cannot. Human-driven threat hunting uses originality to pre-empt adversaries’ likely next moves and expertise to track and trace behavior patterns that are indicative of a malicious presence. Threat hunters also apply a level of informed skepticism to their analysis and explore the broader context of threat activity, empowering them to determine the true nature of activity that may otherwise blend into the background noise of day-to-day operations.
For example, activity originating from a valid user account or legitimate application may fall within a threshold that technology considers normal. However, human-led threat hunting teams work to identify and piece together subtle signs of irregular behavior that expose these seemingly mundane actions as malicious follow-on activity.
Post-Exploitation Behavior is Key to Defense
Hunting for this malicious follow-on activity — otherwise known as post-exploitation behavior — is a key piece of the defense puzzle. New vulnerabilities emerge constantly, but the fundamental behavior of an adversary once they breach an organization’s perimeter remains largely unchanged.
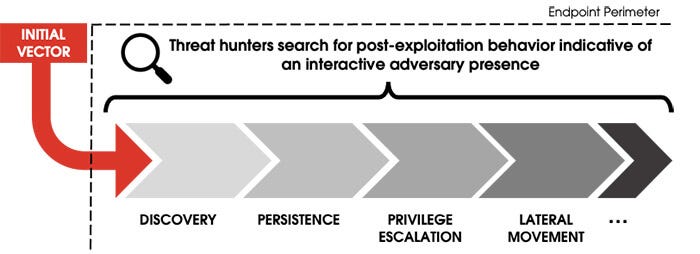
Source: CrowdStrike
Rather than focusing on the initial attack vector, proactive threat hunting is predicated on the ability of highly skilled experts to uncover recognized patterns of adversary behavior. Because these patterns are fundamental to the adversary progressing their mission, they are not substantially altered by the initial access vector. This means that mature threat hunting teams can apply their deep understanding of adversarial post-exploitation tradecraft to effectively and systematically reduce places for threats to hide, regardless of how and where they originate.
The Makings of a Mature Threat Hunting Program
Threat hunting can be done either-in house or outsourced as a managed service. Regardless of the approach your organization takes, the fundamentals of an effective threat hunting program remain the same.
A mature threat hunting program must be:
A continuous 24/7/365 operation — because the adversary doesn’t sleep
Human-led, to capitalize on the power of human ingenuity
Built upon a finely tuned and repeatable hunting methodology
Supported by up-to-the minute threat intelligence
Supported by rich telemetry that provides broad context around activity in the environment
Supported by effective tooling that can efficiently collate, process and distill telemetry to enable hunters to leverage the data at speed and scale
Deployed across the entire environment to ensure comprehensive visibility — because you can’t stop what you can’t see
A threat hunting program structured in this way will redefine what zero-day and newly disclosed vulnerabilities mean for your organization.
About the Author
You May Also Like



_KonstantinNechaev-Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
