3 Ways To Virtualize Mobile Devices -- And Why You Should Do So3 Ways To Virtualize Mobile Devices -- And Why You Should Do So
The idea of splitting smartphones and tablets into personal and business partitions is gaining strength, for good reason. But be warned -- iOS shops will have a tougher go of it.


InformationWeek Green - July 8, 2013

InformationWeek Green
Download the entire July 8, 2013, issue of InformationWeek, distributed in an all-digital format (registration required).
Your Generation Y employees are really, really attached to their smartphones: Most use them in bed, a recent Cisco Connected World Report found, and one-third use them in the bathroom. Talk about personal computing.
Among the 424 respondents to our InformationWeek 2013 Mobile Security Survey, 68% support bring-your-own-device in some form; an additional 20% are developing policies. Unsurprisingly, 78% say their top concern is lost or stolen devices, well ahead of the No. 2 worry, which is users forwarding corporate information to cloud-based services (cited by 36%). More than half, 55%, have had devices go missing, yet encryption is far from ubiquitous.
>
An alternative: Segment mobile devices into personal and business realms. Let employees do whatever they want on their side of the border; IT retains control on the other. There are a number of approaches to compartmentalization, as we discuss in depth in our full report on the topic. None is yet fully mature or widely used, and iOS shops will have a tougher go of it. Even on Android and BlackBerry, there are still plenty of technical challenges.
But I think these products are worth a look.
The most sophisticated methods work at the hardware level and offer a virtual split between work and play; they're also the most disruptive to the user experience. Type 1 hypervisors (essentially mobile incarnations of vSphere) and Type 2 virtualization software running on top of a base OS effectively turn a smartphone into two separate devices, down to different numbers and data plans. They just happen to share the same screen. Sandboxing applications trade isolation for better hardware support. You're essentially running business apps within an app, similar to using the Google Docs suite within a Chrome browser. Like hypervisors, sandboxes create multiple personas that are partitioned, even down to the wallpaper and contact lists. Each persona can have its own apps, security policies and system preferences. Remote display technologies typically use a local native client or, less often, mobile browser to access applications running on a central server. Finally, encrypted storage containers can protect and control locally stored data according to policies, but they don't isolate the apps, which continue to run within the user's personal environment.
While all of these methods are valid, the holy grail remains full mobile virtualization, and it's a compelling vision, so much so that Gartner predicts 50% of enterprises will grab strong control of the corporate footprint on consumer devices through a combination of native containerization capabilities and mobile device management functions by the end of this year. We think that's wishful thinking; our survey shows only 32% of enterprises have deployed MDM. Given that, it behooves most shops to at least evaluate containerization.
There are three main routes:
>> Full client-side hypervisor: As with PCs and servers, there are two ways to create fully virtualized operating environments on mobile devices: Type 1 bare-metal or Type 2 hosted hypervisors. The former run directly on device hardware, underneath the OS, and thus require extensive hardware support, a major challenge on mobile devices where there's no equivalent to the standard x86 hardware platform. The latter, similar to Virtual Box or Parallels, run on top of the native OS, a seemingly easier task. Yet it's still difficult to port even low-level functionality because mobile operating systems are both tightly controlled (we're looking at you, Apple) and heavily customized for specific hardware configurations (here, Android is the bigger culprit). We discuss the differences between Type 1 and Type 2 in more detail in our full report.
>> App sandboxes and containers: Moving up the compartmentalization stack are applications that can encapsulate complete work environments in a secure sandbox or wrap individual apps within a centrally managed container. Application sandboxes, what some vendors call "dual-persona software," take code-isolation techniques used in everything from HTML5 to mobile operating systems to another level by carving out a secure working environment on the mobile device that holds not only locally installed enterprise apps, but app data, preferences and user home screen profiles. The entire runtime environment is protected from the personal home screen and associated apps, and the experience is completely modal -- a user is in either a corporate or personal workspace.
Sandboxes are much easier to port than true hypervisors, meaning they're more likely to work across platforms. For example, AT&T's Toggle works on any Android device running 2.2 or better, while Enterproid's Divide supports iOS and Kindle Fire.
Secure single app containers take sandboxing techniques a step further by supporting user authentication, app and data usage policies, and data encryption (both stored and network). All of this occurs behind the scenes. Companies including Bitzer Mobile, Mocana (Mobile App Protection), OpenPeak (Sector) and Symantec (App Center Enterprise) offer products in this segment. Most deliver a common set of features: encrypted local data containers (protecting data at rest); encrypted network connections (protecting data in motion); some level of data loss prevention, including policies on local data movement (for example through the clipboard via copy/paste restrictions); identity management (user authentication against a central directory); and even time- or location-based access controls (like limiting app access to certain hours, expiring access after a given date or limiting usage to certain locations).
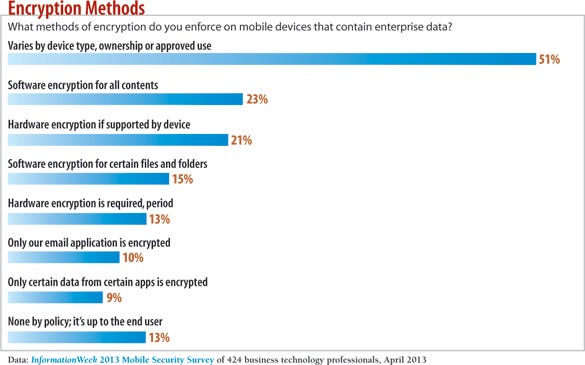
What methods of encryption do you force on mobile devices?
A less effective but more easily implemented alternative to wrapping entire apps is to create a centrally managed encrypted storage volume or local folder for enterprise applications. Although they don't provide control over usage policies or all forms of data movement between business and personal environments (think clipboard or emailing to an external account), encrypted containers do allow for central management of data storage policies and remote wipes. One downside to these products, like Good Dynamics, is that apps need extra code, typically implemented via vendor-supplied SDKs and libraries, to provide the necessary software hooks to use encrypted containers and follow centrally set data access policies. In this era of ubiquitous cloud file storage and sync services, it's probably a better bet to just keep persistent data off the device in the first place via a cloud service like Box or Syncplicity.
>> Trusted remote app execution: An alternative to carving out a separate business environment on personal devices is to simply move app execution off the device entirely, a technique that's been used in various forms -- VDI, terminal services, application streaming, browser apps -- on PCs for years. As with containerized apps, the advantage is that business apps appear in the personal workspace. Application streaming products like Citrix Receiver use a locally installed native client (the receiver) that provides faster app performance and a somewhat better user experience compared with a browser.
There are downsides, however. First, apps generally can't be used offline on mobile devices (though some products do offer caching on Windows devices). This shouldn't be much of an issue in the age of ubiquitous 3G/LTE connectivity. Second, the user experience may suffer if remote applications were developed for a PC with keyboard and mouse, not a touch-sensitive device.
While mobile device virtualization and compartmentalization technologies are still in flux, they make sense now for users accessing sensitive information or in regulated industries.
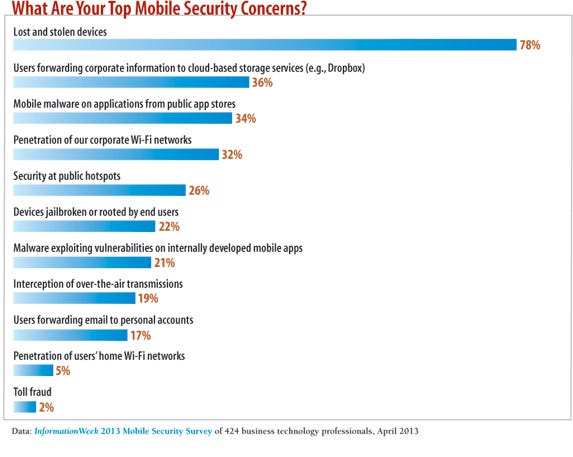
What are your security concerns?
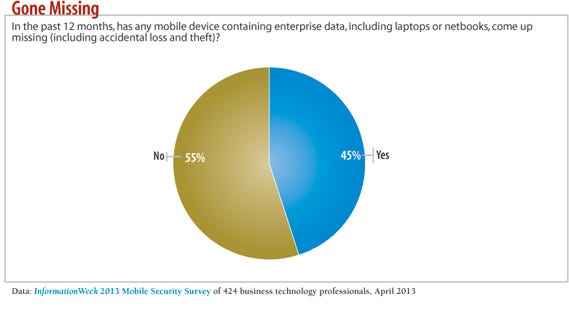
Has any mobile device data gone missing?
About the Author
You May Also Like




