
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
An Inside Look at an Account TakeoverAn Inside Look at an Account Takeover
AI threat find: Phishing attack slips through email gateway and leads to large-scale compromise.

In the last few years, email attacks have rapidly increased in volume and sophistication, with well-researched and convincing impersonation attacks accompanying rising cases of account takeovers. Their sophistication has particularly accelerated over the course of 2020, with globally pertinent news trends such as COVID-19, natural disasters, and social upheaval providing ready-made content for believable phishing emails, and remote working practices proving to be fertile ground for attacks.
In this threat landscape, traditional email tools – which create rules for what "bad" emails look like based on past campaigns – are missing these novel and sophisticated hoax emails. An international logistics company recently found this out the hard way when a spear-phishing attack slipped under the radar of its email gateway – but was detected by Darktrace's artifical intelligence (AI), which was in passive mode as part of a trial.
Darktrace's Antigena Email wasn't configured to actively respond to threats, but looking into its real-time detections allows us to follow the attack from start to finish – and discover the consequences of relying purely on gateways to stop advanced threats.
Without AI taking action, compromising just one employee's email account was all the attacker needed to continue making headway throughout the business. The attacker accessed several sensitive files, gathering details of employees and credit card transactions, and then began communicating with others in the organization, sending out over 200 further emails to take hold of more employee accounts. This activity was picked up in real time by Darktrace's Microsoft 365 SaaS module.
Details of the Attack
The company was under sustained attack from a cybercriminal who had already performed account hijacks on a number of its trusted partners. Abusing their trusted relationships, the attacker sent out several tailored emails from these partners' accounts to the Australian company. All used the same convention in the subject – RFP for [compromised company's name] – and all appeared to be harvesting credentials.
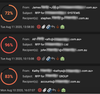
Figure 1: A sample of the malicious emails from the hijacked accounts; the red icon indicates that Antigena Email would have held these emails back.
Each of these emails contained a malicious payload, which was a file storage (SharePoint) link, hidden behind the below text. It's likely the attacker did this to bypass mail link analysis. The organization's gateway did rewrite the link for analysis, but it failed to identify it as malicious.

Figure 2: Darktrace surfaces the text behind which the link was hidden.
When clicked on, the victim was taken to a fake Microsoft login page for credential harvesting. This was an accurate replica of a genuine log-in page and sent email and password combinations directly to the attack for further account compromise.
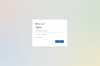
Figure 3: The fake Microsoft login page.
A number of employees read the email, including the CEO. However, only one person – a general manager – appeared to get their email account hijacked by the attacker.
Figure 4: An interactive screenshot of Antigena Email’s user interface.
About three hours after opening the malicious email, an anomalous SaaS login was detected on the account from an IP address not seen across the business before.
Open source analysis of the IP address showed it was a high fraud risk ISP, which runs anonymizing VPNs and servers. This may have been how the attacker overcame geofencing rules.
Shortly afterward, Darktrace detected an anonymous sharing link being created for a password file.
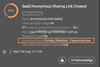
Figure 5: Darktrace's SaaS Module revealing the anomalous creation of a link.
Darktrace revealed that this file was subsequently accessed by the anomalous IP address. Deeper analysis showed that the attacker repeated this methodology, making previously protected resources publicly available, before immediately accessing them publicly via the same IP address. Darktrace AI observed the attacker accessing potentially sensitive information, including a file that appeared to hold information about credit card transactions, as well as a document containing passwords.
Perpetuating the Attack
The following day, after the attacker had exhausted all sensitive information they could elicit from the email account, they used the compromised account to send out further malicious emails to trusted business associates using the same methodology that was used in the initial compromise (credential harvesting, using subject headings "RFP for *Anonymised compromised company*"). Darktrace's SaaS module identified this anomalous behavior, graphically revealing that the attacker sent out over 1,600 tailored emails over the course of 25 minutes.
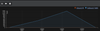
Figure 6: A graphical representation of the burst of emails sent over a 25-minute period.
Why AI Is Needed to Fight Modern Email Threats
For the logistics company in question, this incident served as a wake-up call. The managed security service provider (MSSP) running its cloud security was completely unaware of the account takeover, which was detected by Darktrace's SaaS Module. The organization realized that today's email security challenge requires best-in-class technologies that can not only prevent phishing emails from reaching the inbox, but can detect account takeovers and malicious outbound emails sent from a compromised account.
This incident caused the organization to deploy Antigena Email in active mode, allowing the technology to stop the most subtle and targeted threats that attempt to enter through the inbox based on its nuanced and contextual understanding of the normal "pattern of life" for every user and device.
The reality is, hundreds of emails like this trick not only humans, but traditional security tools every day. It's clear that when it comes to the growing email security challenge, the status quo is no longer good enough. With the modern workforce more dispersed and agile than ever, there is a growing need to protect remote users across SaaS collaboration platforms, while neutralizing email attacks before they reach the inbox.
Find out more about Microsoft 365 email security >
___
Based in New York, Dan Fein is the director of email security products for the Americas at Darktrace. He joined Darktrace's technical team in 2015, helping customers quickly achieve a complete and granular understanding of Darktrace's world-leading Cyber AI Platform and products. Dan has a particular focus on Antigena Email, ensuring that it is effectively deployed in complex digital environments, and works closely with the development, marketing, sales, and technical teams. Dan holds a bachelor's degree in computer science from New York University.
About the Author
You May Also Like

