
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Content Credentials Technology Verifies Image, Video AuthenticityContent Credentials Technology Verifies Image, Video Authenticity
The open technology, which tackles disinformation, has gained steam in the past year, surpassing 500 corporate members and continuing to evolve.
February 12, 2025

When armed gangs raided a Haitian prison and released 4,700 prisoners last March, images and videos showing the violence and gunfire saturated social media around the world. Determining which graphic media was authentic — and marking those instances in a way that future viewers could verify for themselves what was real and what was modified — was a significant challenge.
Showcasing a solution to exactly that problem, the British Broadcasting Corporation (BBC) launched its adoption of Content Credentials, a technology for attesting to the authenticity and provenance of digital content, by using the technology to verify a TikTok video of the attack. The BBC verified the location of the video and its likely veracity, but it determined that audio of gunfire had been added after the fact. The company then digitally signed the video so that future viewers would know the BBC had verified it.
Content Credentials — an open technology that aims to solve disinformation and media integrity issues — is being developed by the Coalition for Content Provenance and Authenticity (C2PA), a group of more than 500 media, software, and hardware companies working to create an ecosystem for verified media.
The BBC's adoption of Content Credentials is just one use case but an important one, says Andy Parsons, senior director of the Content Authenticity Initiative (CAI) at Adobe and a steering committee member of the C2PA.
"The BBC [is] declaring that — regardless of whether this is a photo or whether AI was used to do a photo illustration — you can be guaranteed that it came from BBC, and even that simple proof-of-date or proof-of-origin is something we don't have in media right now," Parsons says.
In 2019, technology and media companies created the CAI to find solutions to disinformation and ways for news organizations to authenticate photos and video. Two years later, six companies — Adobe, Arm, BBC, Intel, Microsoft, and Truepic — founded the C2PA to pursue an open standard for establishing the provenance of various types of media files. The two efforts eventually combined forces to advance Content Credentials, a digital-signature technology and infrastructure for verifying and authenticating media.
In the past year, Content Credentials and the C2PA gained significant steam, with the addition of Amazon, Google, Meta, and OpenAI to the steering committee and the adoption of the technology by several camera makers — including Canon, Leica, and Sony — and smartphone makers, such as Samsung.
Yet the ecosystem is still in its infancy, Christian Paquin, a principal research software engineer at Microsoft, told attendees at last month's ShmooCon 2025.
"You can imagine the situation in five to 10 years when this technology is baked in a lot of the trusted news and a hardware ecosystem that can produce these signatures and can be validated by the social media themselves or the browsers, so that we can really have trust signals to differentiate what's real and what's not," he said.
Manifest Destiny
Content Credentials have three main components: the media data, a manifest describing the data and any actions transforming the data, and a digital signature binding the two pieces of information together in a tamper-evident way. The manifest includes typical metadata, as well as some additional C2PA-accepted fields — attestations — that can describe additional attributes of the photo, its source, and the software actions used to process the data.
Based on public-key encryption and digital signatures, Content Credentials act as an audit log of every action performed on a piece of media. A photo could be captured with a smartphone, cropped and lightened with photo-editing software, and then compressed by a content delivery network. Each of those steps would be an attestation in the manifest of the signed content credential.
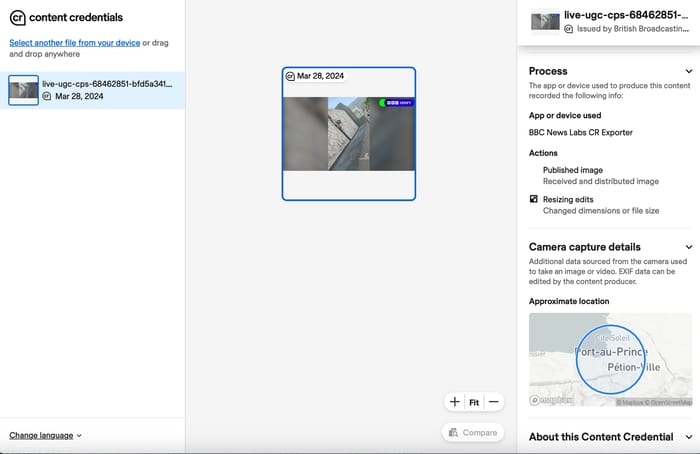
A video signed with a Content Credential shows that it originated with the BBC News Lab. Source: https://contentcredentials.org/verify
The result is providing an audit trail with each piece of authenticated content, which could help citizens and users better know what is fake and what is arguably real, Adobe's Parsons says.
"All the companies involved — and I would lump in civil society and some governments as well — have a real urgency to solve this problem," he says. "And while C2PA is not a silver bullet at solving misinformation, it does put in place a fundamental foundational layer that the Internet probably should always have had around trust, and this is a really nice clean way to do it."
Already, most makers of foundational artificial intelligence (AI) models — such as Open AI, Meta, and Microsoft — digitally sign all images created by their image-generation models with a Content Credential, indicating that it was AI generated or manipulated.
An Evolving Standard
The technology is not done, either. The C2PA specification has quickly evolved over the past three years, reaching version 2.1 in September. Among the new features are efforts to make the credentials more "durable" — in other words, adopting techniques, such as digital fingerprinting and watermarking, to indicate the provenance of images, even if they are manipulated after publication or captured from a screenshot.
The combination of signed metadata with fingerprinting and watermarking is powerful, Adobe's Purdy wrote in a 2024 analysis of the techniques.
"[N]one of these techniques is durable enough in isolation to be effective on its own," he said. "But combined into a single approach, the three form a unified solution that is robust and secure enough to ensure that reliable provenance information is available no matter where a piece of content goes."
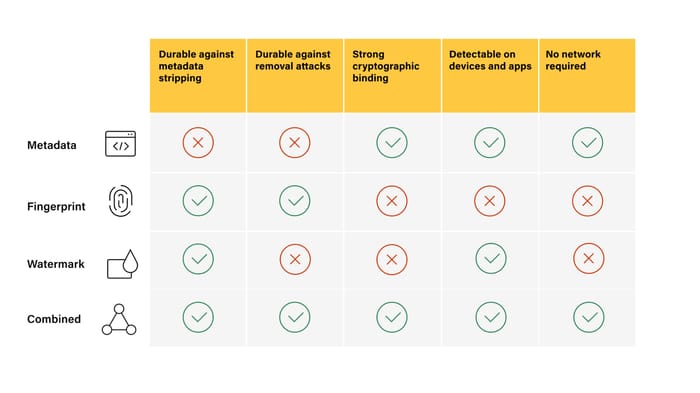
Watermarks, fingerprinting, and Content Credentials can be a powerful combination. Source: "Durable Content Credentials," CAI blog
A number of technical problems remain to be solved. Journalists reporting on an authoritarian regime, for example, may want to remain anonymous and mask their location. Zero-knowledge proofs can help, allowing a name to be redacted and only the organization — BBC News, for example — to be shown or to generalize the location. ZK proofs allow an attribute to be signed, so a photo's GPS coordinates could instead be reduced to New York City or Kiev to provide a general location that hides the photographer's identity, and verified with a digital signature.
"This is an evolving set of certifications," Microsoft's Paquin told the audience at ShmooCon. "The main challenge is establishing who can sign certificates ... establishing PKI that is worldwide is a big problem."
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025

