Cybercrime Ecosystem Spawns Lucrative Underground Gig Economy
The complex nature of cyberattacks has increased demand for software developers, reverse engineers, and offensive specialists — attracting workers facing financial insecurity.
January 30, 2023

Over a 30-month period, cybercriminal gangs and threat groups posted more than 200,000 advertisements seeking workers with skills in software development, maintaining IT infrastructure, and designing fraudulent sites and email campaigns.
The demand for technically skilled individuals continues, but it peaked during the coronavirus pandemic, with double the average job advertisements coming during March 2020, the first month of the pandemic, according to a new report from cybersecurity firm Kaspersky. The analysis collected messages from 155 Dark Web forums posted between January 2020 and June 2022, selecting those that mentioned employment — either posted by a cybercriminals groups or sent by individuals seeking work.
The lion's share (83%) of employment-related posts were threat groups seeking highly skilled workers, including developers (61%), attack specialists (16%), and fraudulent website designers (10%).
Improving defenses have forced attackers to improve their tools and techniques, driving the need for more technical specialists, explains Polina Bochkareva, a security services analyst at Kaspersky.
"Business related to illegal activities is growing on underground markets, and technologies are developing along with it," she says. "All this leads to the fact that attacks are also developing, which requires more skilled workers."
The underground jobs data highlights the surge in activity in cybercriminal services and the professionalization of the cybercrime ecosystem. Ransomware groups have become much more efficient as they have turned specific facets of operations into services, such as offering ransomware-as-a-service (RaaS), running bug bounties, and creating sales teams, according to a December report. In addition, initial access brokers have productized the opportunistic compromise of enterprise networks and systems, often selling that access to ransomware groups.
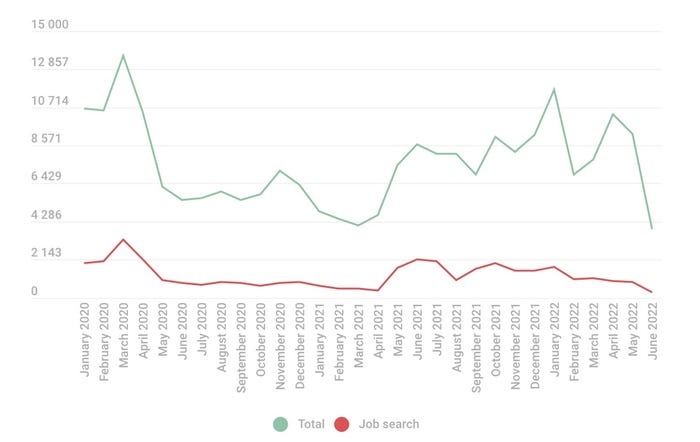
Posts both advertising jobs and searching for jobs increased on the Dark Web. Source: Kaspersky
Such division of labor requires technically skilled people to develop and support the complex features, the Kaspersky report stated.
"The ads we analyzed also suggest that a substantial number of people are willing to engage in illicit or semilegal activities despite the accompanying risks," the report stated. "In particular, many turn to the shadow market for extra income in a crisis."
Pandemic Caused a Spike
In early 2020, such a crisis caused a surge in activity on Dark Web forums.
The pandemic — with its sudden layoffs and work-from-home mandates — drove significant activity in the cybercrime underground, and the highest number of employment-related posts appeared in 2020. Overall, the year accounted for 41% of advertisements and job-seeking inquiries that were posted on the Dark Web — about average. March 2020, however, was the first month of worldwide lockdowns and saw about 6% of all postings, about double the average rate.
"Some ... living in the region suffered from reduction of income, took a mandatory furlough, or lost their jobs altogether, which subsequently resulted in rising unemployment levels," Kaspersky stated in the report. "Some jobseekers lost all hope to find steady, legitimate employment and began to search on Dark Web forums, spawning a surge of resumes there. As a result, we observed the highest ad numbers, both from prospective employers and jobseekers."
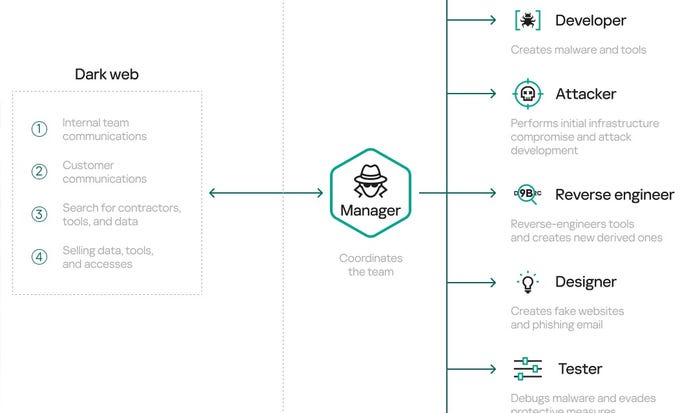
Dark Web flow chart. Source: Kaspersky
Personal crises also appeared to cause some technically inclined workers to seek employment from cybercriminals groups. A common refrain among the job advertisements is that applicants should not have substance addictions.
"Teamwork skills, stable connection, no alcohol or drug addictions," read the translated requirements for one job posting included in the Kaspersky report.
"Dirty Jobs"
In many cases, the Dark Web jobs offered terms similar to those for legitimate jobs, such as full-time employment, paid time off, and regular pay increases, with salaries starting from $1,300 to $4,000 per month. Yet most also did not have an employment contract, and only 10% included a pledge to promptly pay salaries.
The report dubbed the underground employment opportunities as "dirty jobs."
"Many are drawn by expectations of easy money and large financial gain," the report stated. "Most times, this is only an illusion. Salaries offered on the Dark Web are seldom significantly higher than those you can earn legally."
Reverse engineers had the highest potential median salaries at $4,000 a month, with attack specialists and developers having the No. 2 and No. 3 most lucrative salaries, with promises of $2,500 and $2,000. However, the majority of offers (61%) focused on developers.
Those workers are the key to the cybercriminal underground, Kaspersky's Bochkareva says.
"The most sought-after professionals were developers and attack specialists, particularly for coding malicious programs, phishing websites, and planning and implementing attacks," she says.
About the Author
You May Also Like




