Next-Generation Threats: The Inside Story
Cutting-edge attacks like Stuxnet and Zeus will be the everyday security challenges of tomorrow. Here's what you need to know.

 Wicked Innovation
Wicked Innovation
When Iranian President Mahmoud Ahmadinejad announced in November that the nation's nuclear program had been hit by a software attack, he confirmed what many security researchers suspected: that Stuxnet had struck, modifying key systems that controlled the motors of the centrifuges used to process uranium.
Ahmadinejad downplayed the attack's impact, but security researchers think the damage is far more extensive than he let on. A steady increase in Iranian traffic to Web sites dealing with securing industrial control systems indicates that the country's IT experts are searching for an answer to a persistent threat, says Eric Byres, CTO and co-founder of Tofino Industrial Solutions, which secures manufacturing and control systems.
There's no way that the Iranians cleaned it up, says Byres. Wiping Stuxnet from one machine is easy, he says, but "on a network, it's a living hell, because it's aggressive and it spreads in so many different ways."
Stuxnet, which was first identified in July, exploits four previously unknown vulnerabilities, spreading via USB memory sticks and network shares. It infects Windows systems used to manage industrial control systems, overwriting embedded controllers to sabotage those systems.
Welcome to the future of network security, where today's most sophisticated and successful attacks will be everyday challenges. Cybercriminals are likely to try to duplicate Stuxnet's ability to persist in a network and hide in embedded devices. And it's inevitable that they'll try to copy techniques used in other attacks--Zeus' skill at manipulating browser sessions and Conficker's resistance to being shut down, for example.
Attackers also are changing how they operate, adopting new ways to develop and disseminate attacks. Cyberespionage operations increasingly leverage social networks to find easy targets. With Operation Aurora, for instance, attackers suspected of being from China used social networks to identify employees at Google and other companies and then sent them targeted e-mails aimed at infecting key computers at those companies.
In addition, software developer communities are supporting sophisticated plug-and-play malware like the Zeus banking Trojan. Dynamically generated domains, à la Conficker, will make it even more difficult to take down botnet command-and-control networks.
How to Choose Multifactor Authentication 
Become an InformationWeek Analytics subscriber and get our full report on how to choose multifactor authentication. This 17 page report will help you weigh authentication cost vs. risk for your high-risk apps. What you'll find:
It compares various two-factor authentication approaches
Assesses different authentication methods' effectiveness
Looks at how malware can defeat two-factor authentication
Stuxnet's Legacy
In the end, Stuxnet's impact on the Iranian nuclear program may be far less than its long-term impact on the type of cyberattacks we'll have to deal with in the future. With Stuxnet, it's become less about attacks on industries like financial and power, and more about "in-the-weeds attacks," says Dean Turner, director of Symantec's Global Intelligence Network. "Stuxnet was targeted at the details--the frequency component of a motor."
Security experts have long warned that embedded control systems are vulnerable. In 2007, Department of Energy tests showed that embedded systems attacks could take control of a power company's generator and cause it to self-destruct. Most factories are also controlled by embedded systems and programmable logic controllers.
Until Stuxnet, the danger was theoretical. Now anyone who gets their hands on the code has a blueprint for attacking embedded systems. And the code has spread widely, infecting computers worldwide. Stuxnet has provided a "crash course" in writing programmable logic controllers code, says Tofino's Byres. It's only a matter of time before we start seeing all sorts of "specialty worms" going after control systems.
Lock Down For Coming Threats DON'T JUST COMPLY Security controls required by law are seldom sufficient GO BROAD Technology isn't the whole story; pay attention to policy and implementation SECURE MOBILE USERS All those new devices are putting your data at risk PARSE YOUR DATA Identify your most valuable information and focus your efforts there SCRUTINIZE EVERYTHING All components of your digital and physical systems are now at risk
Embedded systems typically link physical and digital systems, so when attackers take control of them, they also get control of critical systems. In addition, code can be hidden in embedded systems, allowing attacks to persist and making it difficult to clean them up.
Private companies aren't likely to remain unscathed by Stuxnet for long, says Jon Ramsey, CTO of managed security provider SecureWorks. He points to Operation Aurora as the first of the most sophisticated attacks to hit a private company. With Aurora, the attackers are saying, "Why not go after the industrial base … large corporations that have a lot of intellectual property, that are highly competitive in global markets," Ramsey says.
Attacker Specialization
Knowledge about these advanced attacks and the techniques they use is spreading rapidly. A major reason is that attackers have created an infrastructure of chat rooms, forums, drop boxes, and technical publications that support and expand their operations. There, they share ideas and develop areas of expertise. One group helps members hone their skills in attacking popular software. Another develops exploits to plug into popular malware. Others focus on growing and maintaining botnets to steal data.
Zeus is a prime example of this specialization. The banking Trojan, which spreads via phishing and drive-by download attacks from legitimate sites, has an ecosystem of underground programmers who create spam campaign templates that plug into Zeus and exploit kits that capitalize on specific vulnerabilities. Criminals can buy one exploit kit to attack computers running Mozilla's Firefox and another to attack Adobe Acrobat vulnerabilities. Zeus' openness has driven its popularity and dramatic increases in functionality. More than 90,000 variants of it now exist, according to Symantec.
Zeus' development infrastructure lets users do more for less money, says Symantec's Turner. That's part of a trend whereby cybercriminals are becoming more efficient, optimizing their operations to get the maximum value from each compromise. Some advanced malware will remove competing and inefficient programs from the systems they infect, and even go so far as to patch those systems in order to get the most out of infected machines, says Brian Contos, director of global security strategy and risk management at McAfee. The malware uses a single computer for multiple crimes, such as stealing data and capturing log-on credentials. Unsuspecting victims end up benefiting, too, since their machines--albeit infected--run better, Contos says.
Attackers also are using automation to increase efficiency. Rather than attack every Internet address in the world, they focus on ones known to belong to computers that use specific vulnerable software, such as WordPress and other popular blogging platforms. Spammers buy out-of-the-box spam campaigns. And bot operators use Web interfaces to monitor and control their networks of compromised systems.
Driving all this innovation in cyberattack software development, support, and infrastructure is money. Rather than sharing techniques, many cybercriminals are becoming more secretive, treating their code and approaches as intellectual property.
It used to be you could go to a conference like DEF CON and people would share tools, Contos says. Not any more. Instead, they're busy developing zero-day threats, he says, "because they want to make money."
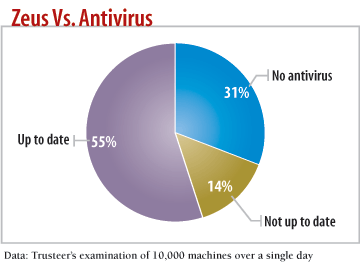
Tomorrow's Attacks In The Making
INCIDENT | NEXT-GEN ATTRIBUTE | DESCRIPTION |
|---|---|---|
Aurora | Social network reconnaissance | Attackers use social networks and Web sites to go after key personnel inside target organizations. They targeted Google and other companies last year. |
Conficker | Dynamic domains | Computer worm uses calculated domain names to make it hard to eliminate. Conficker.C used a randomly selected subset of 50,000 calculated domains to connect with command-and-control servers. |
Stuxnet | Malware targeting embedded controllers | Attacks compromise embedded controllers to take control of physical devices. Stuxnet has compromised programmable logic controllers in manufacturing processes and the Iranian nuclear program. |
WikiLeaks | Distributed denial-of-service mob action | Attackers carry out coordinated cyberprotests. After WikiLeaks' site was attacked, 2,000 supporters quickly organized to attack MasterCard, Visa, and other sites using a voluntary botnet. |
Zeus | Man-in-the-X attack | Attack incorporates itself into the browser, mobile device, or other communications stream to capture and modify traffic. Zeus compromises browser communications to modify bank transaction pages on the fly, allowing funds to be stolen. |
Just-In-Time Attacks
Changes in how cybercriminals operate have made another type of attack--cyberprotests--easier to organize and execute. Recent denial-of-service attacks against MasterCard's, Visa's, and Amazon.com's sites, in retaliation for their refusals to do business with WikiLeaks, also offer a look at the future of cybercrime.
While cyberprotests and denial-of-service attacks aren't new, the technology to support them is getting better and the tools more sophisticated--a trend that will continue. For example, the WikiLeaks attacks, conducted by a group known as Anonymous, used a program called the Low Orbital Ion Cannon, or LOIC. It lets any protester input an IP address and join an attack against the targeted network or system.
Three factors are contributing to the effectiveness of distributed denial-of-service attacks, say Earl Zmijewski, VP and general manager of Internet security firm Renesys. First, the systems being attacked have more bandwidth than ever before, so attackers need to compromise fewer of them to have significant impact on a target. Second, many users continue to run old software, making it easier for attackers to take over their computers and make them part of a botnet. Third, there's still no easy fix for DoS attacks. Content distribution networks can help, but the most effective defense is to use a specialized network that filters out malicious traffic before it gets to the target's servers.
Because of those three factors, botnet operators wield enormous power. Conficker, for example, compromised 6.4 million systems, giving it an aggregate bandwidth of 28 TB per second, says McAfee's Contos. "That's more than Amazon and Google combined--that's massive,"he says.
Threats are inserting themselves between the user and the Internet. These "man-in-the-browser" attacks--widely used by the Zeus banking Trojan--let attackers control what users see. A user banking on a Zeus-infected computer is led to believe he's sending his utility company $100 but, instead, $7,000 is being sent to an account in another state owned by a member of a cybercriminal network. When the user confirms the transaction, he sees only a $100 debit, while the bank receives a request to transfer the $7,000.
"You never know you're defrauded until you look at it from a physical branch," says Amit Klein, CTO at banking security firm Trusteer. "Other malware used this technique first, but with Zeus, it's becoming much more widespread."
Zeus and other threats are circumventing protections aimed at eliminating bank fraud, such as two-factor authentication. Because the attack is done in real time and from the victim's PC, conventional protection fails.
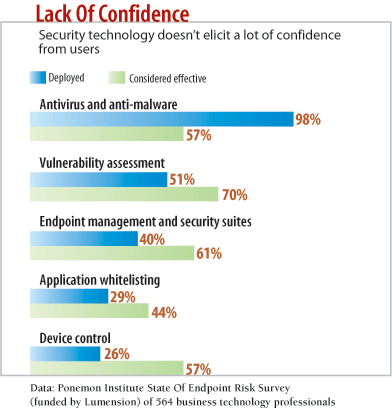
Better Defenses
Many companies assume it's enough just to comply with the security controls required by law. But compliance doesn't cut it. Advanced threats will circumvent well-known security requirements, SecureWorks' Ramsey says. If everybody has the same technology and controls, "then the criminals are going to modify their attacks to subvert those types of defenses," he says.
It was the Federal Deposit Insurance Corp.'s mandate that banks use two-factor authentication and encryption that spurred criminals to develop Zeus to circumvent those protections. Malvertising--online ads that send users who click on them to malicious sites--is another example of attackers circumventing defenses. These attacks avoid firewalls by coming in over the Web. It's the No. 1 attack vector that companies see, according to SecureWorks.
Conventional defenses, such as antivirus software, haven't fared well against sophisticated attacks, says Trusteer's Klein. Stuxnet may have circulated for more than a year before it was detected. Zeus regularly dodges signature-based defenses.
Companies need well-rounded defenses, not just technology, says Symantec's Turner. "We have to start talking about how we share information online, and how we use things," he says. "Policy and implementation are as critical as the technology itself."
Protecting the perimeter is key, but even that's getting more complicated as mobile consumer devices like iPads and iPhones find their way into businesses. As the line between personal and business devices blurs, Turner says, "we've increased the number of touch points that our confidential or business data has."
Companies must identify their most valuable assets as well as potential threats. They need to understand the threats, what they're going to target, and how they're going to target it, SecureWorks' Ramsey says.
Companies also must determine how many users and systems can access critical information, and what's worth protecting. They must implement a data classification system to identify their most valuable intellectual property and focus security dollars and people on that data, Turner says. Businesses have a much better chance of protecting a small subset of their data than trying to protect all of it equally.
IT managers also can no longer ignore components on their networks that aren't computers and routers. Security researchers have shown that printers, which increasingly resemble small servers, can be used as a beachhead into corporate networks, and Stuxnet is weaseling its way in via embedded controllers.
"We have to start thinking about different pieces of technology," Turner says. "Valves are an engineer's purview, and networks are the domain of an IT guy," and we have to get them speaking the same language.
Companies also must focus on better detection and response. Network anomaly detection as well as intelligence services can identify attacks that have successfully found a beachhead in the corporate network, says Ramsey. But detection isn't a good defense against these attacks. "It's cheaper to keep them out than it is to clean them up, and the longer they're in, the more expensive it becomes to take control back of your IT systems," he says.
And that's even more important when looking at the sophisticated attacks that will be everyday fare in the future. As Stuxnet has taught us, these programs persist longer and do more damage than ever. Ultimately, defenders must evolve their defenses to stay a step ahead of the bad guys.
Write to us at [email protected].

InformationWeek: Mon. dd, 2011 Issue
Download a free PDF of Dark Reading January Digital Issue
(registration required)
Sidebar: Is 2011 The Year Of The Mac Attack?
This year may be the one when cybercriminals turn their attention to the Mac, a platform they've pretty much left untouched. Several articles in the Russian hacker magazine Xakep have focused on attacking Mac OS X, suggesting that eastern European hackers may be developing attacks, says Steve Santorelli, a former Scotland Yard detective and director of global outreach for security research group Team Cymru Research.
Because of the dearth of threats, most Mac users don't run anti-malware programs. "If someone comes out with a browser exploit pack next year, we're going to see a lot of people get infected," Santorelli says. "So you may end up having a Zeus for OS X."
Apple's strict control of the Mac, simpler code, and better security model make it more secure than Windows. But OS X isn't fundamentally a more secure operating system than Windows 7, according to Santorelli. The reason there's only a small amount of OS X malware is because the application base is so much smaller.
In 2008, computer scientist Adam O'Donnell used game theory to calculate that malware would start to be a problem for OS X when Macs accounted for about 17% of the computer installed base. Macs now comprise about 11.5% of the U.S. installed base and about 5% worldwide, according to NetMarketshare.com.
Signs of interest from the criminal underground suggest that Apple users should beware. In October, a version of the Koobface virus, which spreads among Facebook users, targeted OS X users. The attack exploits vulnerabilities in Java software on the Mac to turn it into a command-and-control server for a botnet. --Robert Lemos
About the Author
You May Also Like




_santoelia_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)