Corporations With Cyber Governance Create Almost 4X More ValueCorporations With Cyber Governance Create Almost 4X More Value
Those with special committees that include a cyber expert rather than relying on the full board are more likely to improve security and financial performance.

While the US Securities and Exchange Commission has published guidelines for better cybersecurity governance for years, public corporations have mostly ignored them. And while the requirements can be difficult to satisfy, companies that have made the effort created nearly four times their shareholder value compared to those that haven't.
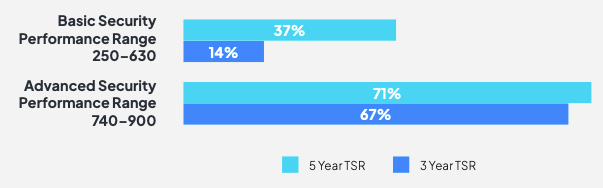
Bitsight and Diligent surveyed thousands of public companies, finding a correlation between cybersecurity experience and the average total shareholder return over three and five years. (Source: Bitsight)
That's the conclusion of a new survey jointly conducted by Bitsight and Diligent Institute, entitled "Cybersecurity, Audit, and the Board." The survey took a deep dive into more than 4,000 midsized-to-large companies around the world, investigating the expertise of directors along with the backgrounds of audit and specialized risk committee members. They measured cybersecurity expertise across 23 different risk factors, such as the presence of botnet infections, servers hosting malware, outdated encryption certificates for Web and email communications, and open network ports on public-facing servers.
"Boards that exercise cyber oversight through specialized committees with a cyber expert member as opposed to relying on the full board are more likely to improve their overall security postures and financial performance," says Ladi Adefala, a cybersecurity consultant and CEO of Omega315, who agrees with the report's conclusions. He worked for a Fortune 500 company on this issue and found that "the board didn't have a focused committee to spend the time to dig into cyber topics. They also didn't have enough members and therefore can't afford to have specialized committees for cyber," he says. Part of his consulting practice is helping to set up such committees, what he calls providing cyber civics lessons.
People resources aside, poor cybersecurity governance isn't really news: Public companies have been giving cybersecurity short shrift for years. For example, security expert David Froud has been writing about this topic since at least 2017. But what is new is seeing how hard it is to assess cyber knowledge and to build enduring governance.
According to the Bitsight report, having separate board committees focused on specialized risk and audit compliance produces the best outcomes. The authors wrote, "These committees are better positioned to dive deep into specific cybersecurity issues and they can develop stronger relationships with the executives charged with the day-to-day cybersecurity operations. This, in turn, can lead to better cybersecurity-related policy, budget and other decisions being made at the board level."
The survey found a wide range of cyber experience among healthcare and financial services-related companies — which ranked the highest — compared with industrial companies, which ranked lowest.
What is telling is that the vast majority of companies have done a poor job at integrating such specialists on their boards of directors and committees. The report found that 5% of those surveyed (and 12% of the S&P 500 companies) had these specialists on their boards. But just having a CISO or CTO on the board isn't any guarantee of cybersecurity performance. "These experts need to be integrated into existing structures" and protective measures, Bitsight noted.
Not mentioned in the report was another governance weak spot: building lasting cyber resilience. This was the subject of another survey, conducted by the Cybersecurity at MIT Sloan Research Consortium and published in the Harvard Business Review last year. The MIT team surveyed 600 board members and found their interactions with CISOs are lacking. Fewer than half the respondents have any regular contact with their CISOs, mostly limited to presentations made at board meetings and not much else.
In many cases, these presentations are limited to the mechanics of protective measures, such as how often they conduct red team exercises or phishing awareness training. Keri Pearlson, executive director of the MIT consortium and co-author (with Lucia Milică, Global Resident CISO at Proofpoint) of the HBR article, draws an analogy with the medical world: "When we are exposed to an infection, we either don't get sick, or if we do get sick, we have things in our bodies that automatically go to work to get us back to being better."
What's needed, she adds, is for "boards to discuss their organization's cybersecurity-induced risks and evaluate plans to manage those risks."
As Adefala sums it up, "The most compelling way is to leverage cybersecurity as a strategic asset for revenue creation or operational agility, rather than as an operational necessity."
About the Author
You May Also Like
Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025Shift Left: Integrating Security into the Software Development Lifecycle
Mar 5, 2025




_vska_Alamy_.jpg?width=700&auto=webp&quality=80&disable=upscale)