The Future Of Web Authentication
After years of relying on passwords, technology vendors -- and enterprises -- are ready for new methods of proving user identity.
May 16, 2013


Download the Dark Reading May 2013 Supplemental issue
Download Dark Reading's May 2013 Supplemental issueIt may have been drawn two decades ago, but the old New Yorker cartoon still rings true: "On the Internet, nobody knows you're a dog."
"It's really easy to be whoever you want to be on the Internet," says Paul Simmonds, a board member of the Jericho Forum, a group of security thought leaders dedicated to advancing secure business in open network architectures. "We've known about it as an industry for 20 years. We've done almost nothing about it. So shame on us."
The process of authenticating users online -- that is, verifying that you are who you say you are -- has remained largely unchanged for years. When Internet users register to get access to a website, they provide an online service, called a "relying party," with personal information to prove their identity. They create user names and passwords, and forever after use that combo to prove their identity to the relying party when logging in. It's simple, it's intuitive -- and it's highly insecure.
The user name-password approach is "the lowest common denominator for authenticating," says Clain Anderson, director of software at Lenovo. It's "like using sticks and rocks versus a rocket launcher," he says.
In the near term, vendors and researchers are supplanting or augmenting passwords with easier and cheaper authentication factors, such as fingerprints, mobile phone tokens and digital certificates based on asymmetrical cryptography. Along the way, a number of industry coalitions are working on replacing passwords altogether.
The Password Problem
Shared secrets like passwords have been around for thousands of years. In computing, pioneers at MIT set up a password system in the 1960s to help meter users' time on the school's time-share computer system. Even then people gamed the system. The story goes that one of the scientists got hold of a master password from the password repository and handed it around to his friends so they could get more than the four hours per week allotted.
That early hack highlights the inherent problem with passwords: To remain effective, they have to remain secret. And to break the system, a hacker need only get into the main password repository.
It's a "brittle" system, says Phil Dunkelberger, CEO of authentication vendor Nok Nok Labs, that can't adequately protect today's scale of users and nodes connected through cloud- and grid-based computing.
Passwords are particularly problematic for Internet security as frequent hacks and breaches show. Just last month, a breach at LivingSocial, an online coupon company, exposed 50 million user passwords. Such break-ins give hackers the power to masquerade as any number of Internet users online. And when they aren't stealing credentials, cyber thieves use password guessing and cracking tools to compromise authentication systems.
Users themselves frequently assist the thieves, falling for phishing scams and reusing passwords across different sites. "Breaking into the system and stealing the passwords isn't even the biggest problem," says John Bradley, senior technical architect for authentication vendor Ping Identity and an evangelist for open identity standards like OAuth and OpenID. "The biggest problem is that people give them away all the time."
Security leaders for years have said that passwords must be abolished, but the alternatives have fallen flat because they're built on flawed assumptions, Jericho Forum's Simmonds says. For example, challenge-and-response systems assume that attackers can't find the answers to users' established questions. And hardware token systems assume that attackers couldn't steal the tokens or the algorithmic information that powers them.
So far, no one has found an intuitive, affordable way for users to sign in to accounts with the same kind of uniform acceptance as passwords. Even passwords aren't necessarily that easy to use. According to a Ponemon Institute survey sponsored by Nok Nok Labs, 69% of 754 U.S. respondents say they've forgotten a too-long or too-complex Internet password, and 67% have been locked out of a site because of password problems.
Since Web authentication isn't secure or easy, says Emilio Martinez, CEO of Agnitio, a voice-recognition biometrics firm, "we have the worst of both worlds."
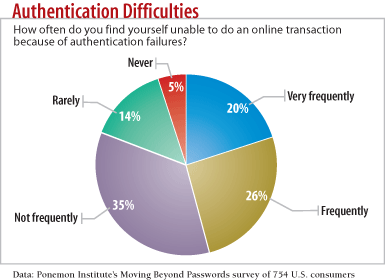
chart: Authentication Difficulties: How often do you find yourself unable to do an online transaction because of authentication failures?
The Limits Of Multifactor Authentication
The security industry has developed a number of workable, if imperfect, supplemental authentication factors to tack onto the user name-password schema.
The most basic is a challenge question system that requires users to answer questions that strangers wouldn't likely know, such as "What is your mother's maiden name?" and "What street did you grow up on?" While this approach increases the barrier to entry into a site or a system, the answers are possible to steal or find out with Internet searches.
More secure are biometric readers that tie in fingerprints, retinal images or voice prints with a user's identity. There also are hardware-based one-time-password tokens, such as those RSA sells. A user gets a key-chain-sized hardware fob that generates a multiple-number PIN created by an algorithm using some variable like the time of day combined with an additional value stored on the device called the seed. That seed is tied to the user's identity on the back-end system that controls access to whatever software or online site needs protecting. Each time the user logs in, he presses a button on the fob to get a PIN that's created on the spot using the algorithm, the variable and the seed value. The person then enters a user name, password and PIN into the system, which crunches the PIN algorithm based on that user's mutually shared seed with an additional variable that can be tied to that user's identity.
Hardware tokens and biometrics have worked reasonably well in business environments that require people to sign on to an internal network, hardware device or software system. However, they haven't translated well online, because the cost of providing tens of thousands of people with the hardware is prohibitive. Two-factor systems based on tokens are difficult to use since people must have the PIN-generating device any time they log on. For online authentication to be widely used, people would have to carry numerous fobs to authenticate into multiple websites. It's an unwieldy process and still based on shared secrets -- though admittedly more complicated ones.
Crooks can't steal the shared secret directly, but they can steal a person's hardware token and log on as that user. In 2011, thieves attacked RSA and gained access to the token seed data for many customers in one fell swoop, forcing the company to reissue tokens with new shared secrets.
Multifactor Authentication Within Reach
The financial industry has been a proving ground for two-factor authentication. That push came from the Federal Financial Institutions Examination Council, a government auditing body that works on behalf of several financial regulatory agencies, including the Board of Governors of the Federal Reserve System, the Federal Deposit Insurance Corp., the Office of the Comptroller of the Currency and the Office of Thrift Supervision. The FFIEC released its "Authentication In An Electronic Banking Environment" guidance in 2005, requiring banks to augment passwords with additional risk-mitigation mechanisms. The group started auditing banks for compliance at the end of 2006.
The mandate spurred banks to experiment with various forms of second-factor authentication. Many banks instituted question-and-response systems. They also set up fraud-prevention systems that trigger an additional form of authentication if a high-risk event occurs, such as if someone logs in from an unfamiliar computer. That form could be asking a person to enter a code sent via email, text or phone call for an address or number the bank has on file. For high-net-worth customers, some banks invested in hardware tokens. The FFIEC guidance pumped money into development of new forms of authentication, as vendors chased the financial industry's burgeoning compliance market.
But other industries haven't faced these sorts of regulatory requirements, and the costs and inconvenience, along with complacency, have kept them from embracing multifactor authentication. It doesn't make business sense for companies to buy expensive authentication if the accounts they're protecting aren't worth as much as the protections themselves.
Larger online companies, like Google, Twitter and PayPal, see risks to their brands if people get hacked. So all three Internet giants are working on two-factor authenticators. They've each hired authentication experts and are sharing their research on bolstering Web authentication techniques.
Advancements in mobile technology are helping drive multifactor authentication. Putting software tokens on mobile phones could eliminate the need for people to carry around many hardware-based token devices. But this approach continues to use shared secrets -- algorithmic code shared between the user's phone and the relying party's server. Plus, often people are using smartphones to access a website, so they're receiving their tokens on the same devices they're using to log in -- referred to as "in-band" authentication. The in-band approach is only secure as long as the device itself isn't compromised.
An alternative to shared-secrets approaches to authentication is to use mobile devices and asymmetric cryptography. This approach relies on digital signatures signed by encryption keys that are held on a person's devices. The user's identity information is encrypted and stored on her computer using public key cryptography. The keys to unlock that system sit on the computer browser, the mobile device and the identity service provider's cloud server. When the user signs in to a site enabled with the identity provider's software, she must use digital signatures from at least two of these keys to log in. From the user's point of view, it's simple -- done with a click, says Steve Kirsch, founder and CTO of OneID, an identity provider. Another positive is that the relying parties aren't maintaining central repositories for the bad guys to steal from, Kirsch says.

factoid: 6 in 10 computer users reuse passwords across the Web
This system doesn't pose an in-band problem because it uses encryption and because all of the key information isn't located on the same device that the user is using to login. And if attackers were to steal the key information held in the server-side repository, they wouldn't be able to commit a mass breach because they wouldn't have the key information that each individual user holds. This model doesn't stop a motivated attacker from potentially breaking it on a case-by-case basis, but it's the difference between "retail hacking and wholesale hacking," says Jon Callas, co-founder of encrypted mobile communications vendor Silent Circle.Biometric applications incorporated into mobile devices also have potential as authentication mechanisms of the future. Online companies could find ways to use smartphones equipped with cameras, microphones and even built-in fingerprint readers to authenticate accounts. It will depend on how well these methods are deployed within a wider authentication framework, because consumer device providers will have to enable federated authentication protocols, says Darren Platt, CTO of cloud identity provider Symplified. Done right, this would let carriers provide authentication to third-party apps and services, including e-commerce websites and financial services providers, he says.
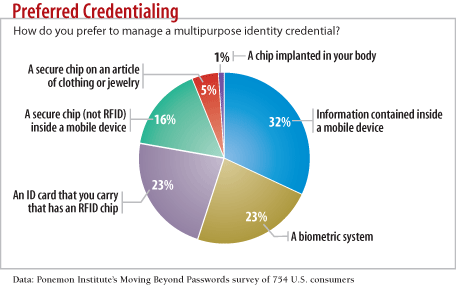
chart: Preferred Credentialing: How do you prefer to manage a multipurpose identity credential?
Federation To Solve Inconvenience Issues
Federation protocols and other single sign-on back-end standards could provide a missing piece to the authentication puzzle. These standards offer the technical framework to let people use a single set of credentials to log in to numerous sites without sharing their login credentials with all those sites.
Leading the way on this front is OAuth, the open standard that powers Facebook's third-party single sign-on service that lets a user log in to a huge number of consumer Internet sites using a Facebook login. It's also the protocol behind similar efforts at Twitter and Yahoo.
"The reason we created OAuth was so that you don't give your user name and password to a third party," says Bradley of Ping. If you're logging in by giving an application access to your Twitter account through OAuth, "the third-party site gets a token for accessing that user's authenticated identity but never actually gets your user name and password."
So while it doesn't solve the problem of strong authentication at the relying party that provides the initial authentication, it does allow for a much simpler user experience and shields the user's identity. People deal with fewer passwords and are less likely to reuse them. And it also gives you an HTML plane where you could insert a federated identity that depends on a stronger authentication factor, Bradley says.
Bradley is seeing a movement among the large providers he works with via the Open ID foundation to start accepting each other's federated logins to reduce the amount of fraud. Federated credentials let people choose strong credentials through a federated identity provider. This approach could sidestep concerns of users who want strong authentication and the convenience of a single sign-on process, without having to trust a social media provider such as Facebook with even more details about their lives.
Tie It All Together With A Long Leash
The approaches vying to replace user names and passwords aren't mutually exclusive. With some integration work, multiple forms of authentication, such as mobile biometrics and a federated identity, could be tied in with a framework like OAuth to make it easy for people to sign on to all their online accounts.
But there are so many pieces to Web authentication that some sort of pattern is needed to keep things from snarling. It will be tough to do, but a number of coalitions and nonprofit brain trusts are working on it.
Jericho Forum's Simmonds and a consortium of U.K. security colleagues are trying to create technology that's similar to OneID through anonprofit called the Global Identity Foundation.
This group maintains that there's no good way for people to assert their identities online. It supports building a stronger identity foundation by identifying and enrolling a user's core identity in a system on his computer, and then breaking up user attributes into contained personas. So, for example, one persona might be related to a person's login information to a social media site, and it would only contain attribute information around the user's online handle and email address. The same person's "citizen" persona would handle login information for government sites and might have attributes such as Social Security number and voter registration information. A retail account may have attributes such as credit card information.
The ideas is that core identity information is encrypted on the user's system, and something like biometrics technology must be used to unlock the appropriate encrypted information. When a person wants to make a transaction, that system would connect with the online server and only offer information within the personas that are relevant to that online system -- so an online purchase may be able to pull from the citizen and retail personas, but posting on a social site could only pull from the less-risky social persona.
"The bad guys can't spoof it," Simmonds says of this type of distributed system. "So even if they take the identity, they can't assert it because they don't have the crypto components that go with it, because you hold those yourself."
On another front, a newly formed group called the Fast IDentity Online, or FIDO, Alliance is trying to tackle Web authentication by creating a comprehensive open architecture specification designed to act as the glue between technology built into devices, strong-authentication devices and software, and the relying parties' server infrastructure. This group wants to create a platform for FIDO-enabled devices to provide interoperability between all the products that make up the authentication ecosystem.
"It's standard plumbing," says Dunkelberger of Nok Nok, a founding member FIDO. The alliance hopes to standardize the way relying parties enroll users and their devices, and provide a standard way to inventory devices to find out what FIDO-enabled authentication elements -- such as software tokens, fingerprint readers, cameras and microphones -- they contain.
Such a spec tells the back-end system, "Here's all of the elements you can use to establish a multifactor connection to this person and device," Dunkelberger says. Then it enrolls the user and provisions the encryption keys on both sides for the challenge-response. "And it does it in a standard way, regardless of authentication, regardless of single sign-on, regardless of any of those things," he says. "Everybody wins because we're not out there goring anybody's ox. We don't pick winners on any of those things in the stack."
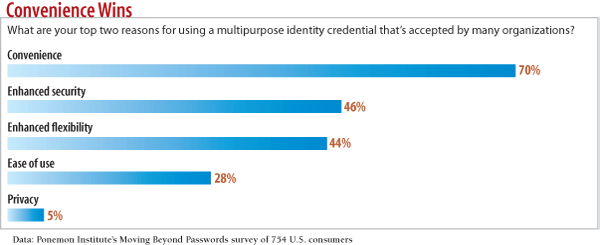
chart: Convenience: Wins What are your top two reasons for using a multipurpose identity credential that's accepted by many organizations?
FIDO solves the problem of relying parties being unable to trust users' endpoint devices because they don't really know whether there's malware on them or other issues, says Anderson of Lenovo, which is also a founding member of the group. The open architecture provides a trusted authentication method that can work with assurance on any device, so fingerprint readers, for instance, can be tied in to verify that the right person is accessing the right machine and the right process, he says.
Most important, the open architecture can be adopted across the industry and not just by those with deep pockets, says Michael Barrett, CISO of PayPal, who's also FIDO's president.
PayPal can manage quite well using advanced risk-based authentication systems, Barrett says, but most companies aren't able to develop highly sophisticated options. "The clear mandate for the FIDO Alliance is to make the Internet a safer place for everyone by enabling the development of an ecosystem," he says, "which fosters authentication that's simultaneously easier to use than user IDs and passwords and stronger for relying parties."
Whether it's FIDO or something else, this is the combination necessary to attain the Web authentication holy grail. Tomorrow's authentication option must be more effective than today's passwords -- and as easy, and hopefully easier, to use.
About the Author
You May Also Like




