‘Golden Hour’ Incident Response Agility‘Golden Hour’ Incident Response Agility
Security leaders must encourage and integrate data, processes, and controls to facilitate comprehension and investment of precious human capital in higher-level tasks.

Do you really need to worry about targeted attacks? In our new Tackling Incident Detection and Response survey, we found that, depending on the size of your business, you are probably responding to one to three incidents per week. That’s a big change from 10 years ago, when I did incident response for a living. As a large organization, we were investigating only one or two incidents per month.
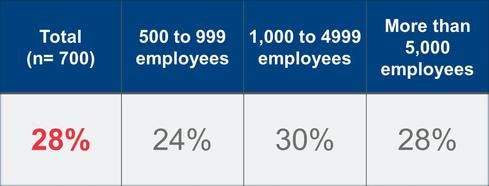
Today these are not just generic malware events sprinkled with insider threats and external attackers. More than a quarter -- 28% -- of investigations were related to targeted attacks, and that is true across all company sizes. This is important to internalize: The situation is no longer a question of “they won’t come after me, I’m not big enough.” Being “small” no longer offers protection (see chart below).
What does that mean for incident responders? You have to get agile, think about where you can move more quickly, save time, and harness technology such as analytics and automation to help you out.
To dig deeper into what we can do differently, three data findings captured the cry for help by security operations teams.
First, the chart below shows where practicing incident responders spend their time today. As we look at the responses, most of these efforts combine human expertise with tools and data. All of these time commitments can be improved through better interpretation of more relevant data, policy-based workflows, and facilitated automation.
Which processes are the most time-consuming incident detection/response tasks? 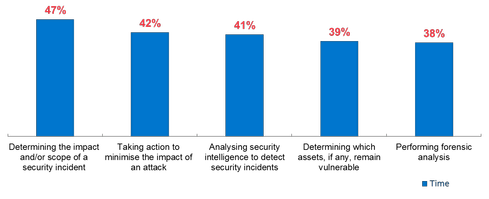 Let’s just look at the No. 1 response: determining the impact and scope of the incident. If half your time is spent just trying to figure out how big the impact crater is, how valuable would it be to have that assessment done 20% more quickly? Say you had four more hours in your week to spend on something else. You would be able to shift into taking action (the second most time-consuming task) more quickly. And if these two steps were part of one command and control environment, with drilldown actions, your world could be transformed. Or you could handle another incident that week.
Let’s just look at the No. 1 response: determining the impact and scope of the incident. If half your time is spent just trying to figure out how big the impact crater is, how valuable would it be to have that assessment done 20% more quickly? Say you had four more hours in your week to spend on something else. You would be able to shift into taking action (the second most time-consuming task) more quickly. And if these two steps were part of one command and control environment, with drilldown actions, your world could be transformed. Or you could handle another incident that week.
The same report asked for insights into what is holding responders back from real-time understanding of what is happening in their organizations. The top gap focused on understanding user behavior -- not just getting user data, but making it meaningful (see chart below).
Which are the biggest inhibitors to having real-time and comprehensive security visibility at your organization?
The second gap highlights a challenge Intel Security has been targeting for several years with our Security Connected story approach: Responders need tighter integration between security data and the systems that operate IT infrastructure so they can figure problems out more quickly, then act more quickly once they’ve figured them out.
The third inhibitor reflects a need for more understanding of network behavior. This one is especially interesting because despite the wealth of network data many respondents already collect, there is still a gap in understanding what that data means. In another data set from the same survey, the top four data sets collected are network related, yet our survey said responders aren’t getting enough insight into network behavior.
Which of the following data types does your organization collect in support of its information security analytics strategy (i.e., for risk management, incident detection, incident response, forensic investigations, etc.)? (Top 10 shown.)

The fourth need -- baselining behavior -- is actually key to comprehension of user and network behavior; once you chart what is normal, you can identify what is abnormal.
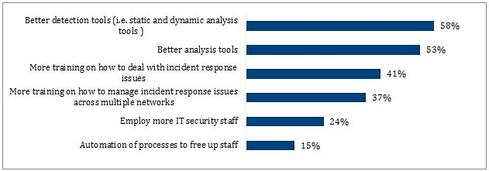
Finally, the survey validated that incident responders know that they can use help. For starters, they need better tools. They asked for both better detection tools and better analytics (see chart below).
In your opinion, which of the following items would do the most to improve the efficiency and effectiveness of your staff?
After those technology enablers, they want training, more staff, and automation to free up those human resources. This takes us back to the finding at the beginning: Incident responders are spending a great deal of time on tasks that are ripe for change. Scoping, containment, remediation, and root cause analysis -- these are all susceptible to acceleration and automation using integrated and more powerful tools and scripted workflows.
From Clutter to Comprehension
The call to action for security leaders is clear: Incident responders are spending high proportions of time doing low-level data collection, synthesis, and analysis. This won’t be sustainable as they shift more time to investigations of increasingly complex targeted attacks. It’s the leader’s job to encourage and integrate data, processes, and controls to facilitate comprehension and investment of precious human capital in higher-level tasks.
About the Author
You May Also Like