
Breaking cybersecurity news, news analysis, commentary, and other content from around the world, with an initial focus on the Middle East & Africa and the Asia Pacific
Amateurish 'CosmicBeetle' Ransomware Stings SMBs in Turkey
With an immature codebase and a "rather chaotic encryption scheme" prone to failure, the group targets small businesses with custom malware.
September 12, 2024

A cybercriminal group — or individual — known as "CosmicBeetle" is exploiting vulnerabilities in technologies used by small businesses in Turkey, as well as Spain, India, and South Africa. The goal is to install ransomware that — unfortunately for victims — sometimes has glitches.
Likely based in Turkey, the ransomware attacker operates at a fairly "low level of sophistication" and is currently developing ransomware that demonstrates a "rather chaotic encryption scheme," according to analysis by Slovakian cybersecurity firm ESET. CosmicBeetle often deploys custom ransomware, dubbed ScRansom by ESET, that appears to be under active development with frequent updates and changes.
Because CosmicBeetle demonstrates immature skills as a malware developers, a variety of problems have affected victims of the threat actor's ransomware, says Jakub Souček, a senior malware researcher at ESET, who analyzed CosmicBeetle. In one case, ESET worked with a victim organization and found that the encryption routines executed multiple times on some of the infected machines, resulting in some data recovery failing.
"Seasoned gangs prefer to have their decryption process as easy as possible to increase the chances of correct decryption, which boosts their reputation and increases the likelihood that victims will pay," the report stated.
But for CosmicBeetle, "while we were able to verify that the decryptor — in its most recent state — works from the technical point of view, a lot of factors still come to play, and the more you need [for decryption] from the threat actor, the more unsure the situation," he says. "The fact that the ScRansom ransomware is still changing quite rapidly doesn't help."
Density of CosmicBeetle attacks over the past year. Source: ESET
The relative immaturity of the CosmicBeetle threat actor has led the group to embark on two interesting strategies, according to the ESET report. First, the group has attempted to imply connections with the infamous LockBit cybercriminal group as a way to, ironically, inspire trust in their ability to help victims recover their data. Second, the group has also joined the RansomHub affiliate program, and now often installs that ransomware rather than its own custom malware.
Opportunistically Targeting SMBs
To kick off its compromises, the CosmicBeetle group scans for and attempts to exploit a variety of older vulnerabilities in software typically used by small and midsize businesses, such as issues in Veeam Backup & Replication (CVE-2023-27532), which can allow unauthenticated attackers to access the backup infrastructure, or two privilege escalation vulnerabilities in Microsoft Active Directory (CVE-2021-42278 and CVE-2021-42287), which together allow a user to "effectively become a domain admin."
The group is likely not specifically targeting SMBs, but because of the software it targets for exploitation, smaller businesses make up the majority of its victims, Souček says.
"CosmicBeetle abuses quite old known vulnerabilities, which we expect more likely to be patched in larger companies with better patch management in place," he says, adding: "Victims outside of the EU and US, especially SMBs, are typically the result of immature, non-seasoned ransomware gangs going for the low-hanging fruit."
The targets include companies in the manufacturing, pharmaceuticals, legal, education, and healthcare industries, among others, according to ESET's report published on September 10.
"SMBs from all sorts of verticals all over the world are the most common victims of this threat actor because that is the segment most likely to use the affected software and to not have robust patch management processes in place," the report stated.
Turkish Delight? Not So Much
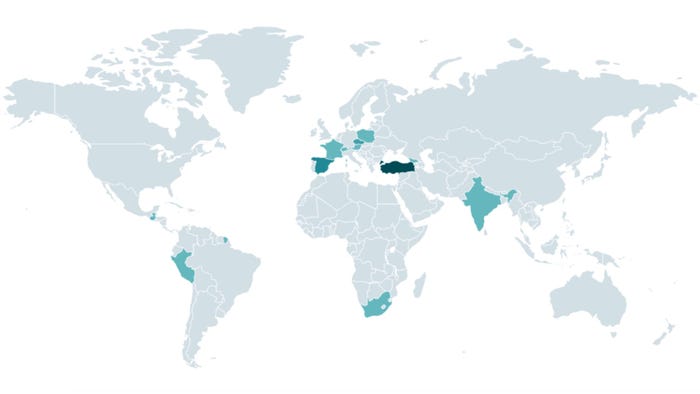
Turkey accounts for the most victimized organizations, but a significant number also come from Spain, India, South Africa, and a handful of other countries, according to data collected by ESET from the CosmicBeetle leak site.
While one firm has connected the threat actor to an actual person — a Turkish software developer — ESET cast doubt on the connection. Yet, with Turkey accounting for a larger share of infections, the group is probably from the nation or the region, Souček acknowledges.
"We could speculate that CosmicBeetle has more knowledge of Turkey and feels more confident choosing their targets there," he says. "As for the remaining targets, it is purely opportunistic — a combination of vulnerability of the target and it being 'sufficiently interesting' as a ransomware target."
Read more about:
DR Global Middle East & AfricaAbout the Author
You May Also Like




