Gallmaker Attackers Living Off the Land, Symantec Finds
Gallmaker, a new state-sponsored threat group, eschews custom malware for legitimate hacking tools and techniques to run under the radar while attacking government and military organizations in eastern Europe and the Middle East, according to recent research from Symantec.

A previously unknown cybercriminal group is opting for known hacking tools and tactics rather than custom malware to evade detection by cybersecurity solutions as it targets government and military institutions in eastern Europe and the Middle East, according to researchers with Symantec.
The group, which the researchers have dubbed Gallmaker, uses what are known as living-off-the-land (LotL) tactics and publicly available hacking tools in its cyber-espionage campaigns, making it difficult to be detected once it's gained access to a victim's device mostly likely through an email spear-phishing effort.
Gallmaker has been operating since December 2017, with the activity continuing into this year, with a particular spike in April, the Symantec researchers wrote in a report earlier this month. Among the targets have been several embassies of a particular eastern European country located in different regions around the world. In addition, the apparent state-sponsored campaign also has taken aim at a Middle Eastern defense contractor and a military organization.
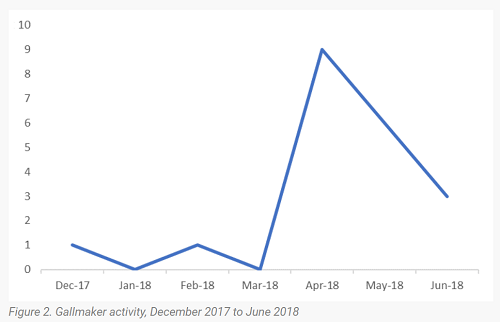
(Source: Symantec)
Given the targets, it doesn't appear that the campaign efforts are random or accidental, according to researchers. Instead, the victims are specifically chosen.
The Gallmaker attackers gain access to the victims' systems through spear-phishing emails that deliver malicious Office documents that use titles with government, military and diplomatic themes, according to Symantec. The emails are written in English or Cyrillic and while not sophisticated, "evidence of infections shows that they're effective. The attackers use filenames that would be of interest to a variety of targets in Eastern Europe," the researchers wrote. (See Kaspersky: Spear-Phishing Attacks Target 400 Industrial Companies.)
The malicious documents exploit the Microsoft Office Dynamic Data Exchange (DDE), which can legitimately be used to send messages between Microsoft applications to share data between Excel and Word, for example. Security researchers last year found it could be used by attackers to execute code on victims' machines and was exploited in several malware campaigns later in the year.
In December Microsoft issued an update disabling DDE in Word and Excel, but the victims in the Gallmaker campaign had not installed the patch, the Symantec analysts note.
After gaining access to a system, the attackers use such available tools as WindowsRoamingToolsTask aimed at PowerShell, a "reverse tco" payload from Metasploit that also leverages PowerShell and a legitimate version of the WinZip console.
Researchers also have found the Rex PowerShell library, which is available on GitHub, on victims' systems. The library can be used to create and manipulate PowerShell scripts so they can be used with Metasploit exploits. Gallmaker is using three IP addresses for its command-and-control (C&C) infrastructure and in an effort to avoid detection deletes some of its tools from those systems once the group is finished.
Jon DiMaggio, senior threat intelligence analyst at Symantec Security Response, told Security Now in an email that the use of LotL techniques is increasingly popular among cybercriminal groups in targeted attacks because "it makes it harder for defenders to identify and mitigate the activity."
"Often this activity will blend in with legitimate operational activity conducted by administrators," DiMaggio wrote. "In addition to having a multi-tiered defensive solution such as the use of firewalls, intrusion prevention systems and endpoint protection, defenders need to monitor and restrict the use of administrative tools on their networks. It is no longer enough to monitor nefarious traffic or wait for an alert based on malicious activity."
Symantec researchers were able to detect Gallmaker through the vendor's Targeted Attack Analytics (TAA) technology, which leverages artificial intelligence capabilities, to identify specific PowerShell commands used by the group as being suspicious, convincing them to further investigate, DiMaggio added. Otherwise, Gallmaker may have remained undetected.
"The use of LotL tactics on its own is not unique to only state-sponsored threats," DiMaggio said. "However, there has been a definite change in tactics and we are seeing an increase in adversaries using LotL as part of their attack. Since this makes it harder to defend against and identify, we anticipate this trend will continue. If defenders begin to identify and prevent this type of activity quicker and more efficiently, it would likely curve the trend, but at this stage it does not appear to be the case."
Security analysts need to also look at legitimate activity using administrative tools along with investigating malicious activity. Until then, bad actors will continue using LotL tactics, he added.
Related posts:
— Jeffrey Burt is a long-time tech journalist whose work has appeared in such publications as eWEEK, The Next Platform and Channelnomics.
Read more about:
Security NowAbout the Author
You May Also Like




