What Are You Doing During The Golden Hour After An Attack?What Are You Doing During The Golden Hour After An Attack?
Take the time to detect the attack, isolate the infected machines, and restore them to a known state.

Are you one of the lucky 12%? That is how few companies we surveyed did not experience a successful targeted cyberattack in 2014. If you are one of the few, and think your luck is going to hold in 2015, you can skip to the next article. Otherwise, please read on.
We recently concluded a research study with Vanson Bourne of security professionals at large and mid-size companies around the world (see chart below). According to the study, most of you are very busy analyzing large volumes of data as you try to find actionable issues amidst the noise. On average, you are responding to an attack every five to 10 days. Half of these attacks are generic malware or adware, annoying to users but not an especially large threat to your company. However, whether you are dealing with some generic malware or a targeted attack, it takes time to detect the attack, isolate the infected machines, and restore them to a known state.
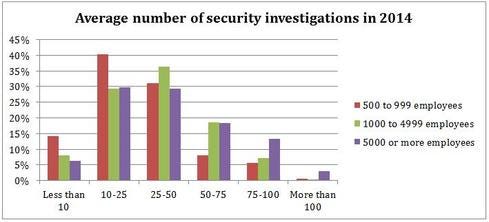
Almost 30% of the attacks are finely tuned and targeted at a specific company, department, or even a few individuals. Why do the survey respondents think these attacks are having increased success? You told us that the attacks are often socially engineered to appeal to the target, and are leveraging multiple channels such as social networks, non-PC devices, and external cloud-based tools. As a result, they are more difficult to detect, and even security-savvy users are having a more difficult time telling which communications are malicious.
When fighting a targeted attack, security professionals surveyed reported that, on average, it took six days to move from discovery to remediation. Financial services, insurance, construction, business or consumer services, and energy and utility companies took the longest time -- eight to 10 days. Government, IT, transportation, and healthcare took the shortest time, at three to four days. Once discovered, things moved more quickly, taking on average nine hours to contain the infected systems, 19 hours to restore them to their normal state, and 30 hours to identify the attack vector and ensure that the security defenses were ready to handle a repeat occurrence.
What is taking up the most time? The top three are at the intersection of human expertise and security data: scoping out the size of an incident, containing it, and working to detect the next one. All of these can be improved through faster interpretation of relevant data and appropriate automation. If so much time is spent trying to determine the scope of an attack, doing that faster means containing it and getting back to normal sooner.
Next, we asked “What is inhibiting your ability to quickly understand what is happening in the organization?” Two of the top issues were an inadequate understanding of user behavior and network behavior. These are not requests for more data, but more comprehension. Like many of the respondents, you are probably already flooded with data, collecting firewall logs, networking events, rule sets, and even data packets. These are requests for better tools and more effective ways to interpret the data.
Fighting The Good Fight
The survey respondents also told us that they are in a fight that is sometimes biased against them. Incident detection and response is a mix of disparate tasks, manual processes, and inefficiencies that slow down response time and cleanup. Respondents asked for monitoring tools that can generate a better understanding of normal behavior, whether it is users, network traffic, servers, or applications. This is critical to being able to quickly identify anomalous activity and separate critical alerts from the cacophony of security noise. And 80% of respondents believe that lack of security technology integration is an obstacle. According to the study, security professionals would like a higher level of tool integration, both between tools and from the security operations center to endpoint.
Finally, we asked what help was wanted to boost efficiency and effectiveness of incident response efforts. The top two requests, obviously related to that number one time sink, were better detection tools and better analysis tools. The next two asked for more training and more people. Surprising to me, only 15% asked for more automation. When I look overall at these responses, I see a need for better analytics and more automation.
Analytics will help improve detection accuracy based on deeper inspection and better threat intelligence. Automation is a necessity because we all know there are not enough people to deal with the volume of attack we face. Historically, the reasons not to automate have been fear of false positives and loss of control. However, in order to scale staff and skills to the volume of events, we need to harness intelligent analytics to identify incidents from the mountains of event data.
To gather information for the survey, we spoke with 700 IT security decision makers during February and March 2015, at mid-market companies (500-999 employees), large companies (1,000-4,999 employees), and large enterprises (5,000 or more employees). These people were located in Australia, Brazil, France, Germany, the United Kingdom, and the United States. They represented more than 10 different industries, including information technology, manufacturing, financial services, government, retail, and transportation. You can read the full report at http://www.mcafee.com/us/resources/reports/rp-esg-tackling-attack-detection-incident-response.pdf.
About the Author
You May Also Like




