How To Prevent Data Leaks From Happening To Your OrganizationHow To Prevent Data Leaks From Happening To Your Organization
Data can find its way out through accidents or malice. Here are some tips for keeping your essential information from walking out the door.

 Download the entire Dark Reading April 2012 Digital Issue
Download the entire Dark Reading April 2012 Digital Issue
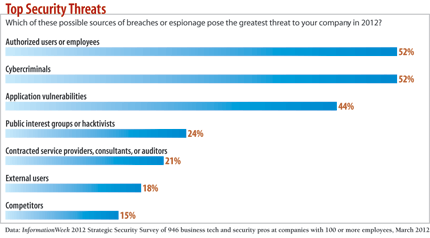
What worries IT: a hacker lurking in the Internet's dark corners or Bob in accounting? Turns out it's both. Company employees pose just as much of a threat as cyberthieves, according to InformationWeek's 2012 Strategic Security Survey of business technology pros.
And yet, insider threats represent only a fraction of all attacks--just 4%, according to Verizon's 2012 Data Breach Investigations Report. So why the fuss? Because insiders have access to critical company information, and there are dozens of ways for them to steal it. And these attacks can have significant impact. Last year, a Bank of America employee sent account information on hundreds of customers to identity thieves, who used the information to steal money from those accounts. Losses totaled $10 million, not to mention the public relations fallout from the incident.
The threat insiders pose is compounded by the fact that IT tends to focus on securing the perimeter of the network from external attacks and pays little attention to malicious activity inside the network. The increasing mobility of corporate data and devices is making it even easier for insiders to steal data. Clearly, it's time companies rethink their security strategies to cover both the malicious hackers and Bob in cubicle 3B.
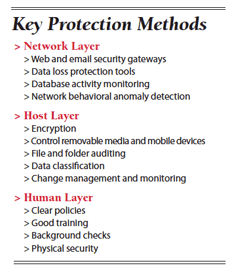
Insider threats can be either intentional or accidental, and you often can use one set of controls to mitigate both of these. You'll want to target three layers to address the insider threat: the network; the host device; and the people who generate, manipulate, and move data from one place to another.
At the network layer, controls must be capable of analyzing network traffic to detect and, when possible, prevent the transmission of sensitive data. Host-based protections include anti-malware, encryption, change management, and other security controls. The most difficult element of defense is the human factor--implementing policies and training to educate employees on proper handling of sensitive data. Here are steps you can take to secure all three layers.
Lock Down The Network
The two most common avenues for insiders to move data out of the enterprise are email and the Web. Both come into play with malicious and unintentional data breaches, and the intent may not always be clear at first glance. Employees using corporate email accounts may inadvertently send sensitive files to the wrong address. Meanwhile, someone who wants to steal sensitive information may use a personal Web mail account or upload information to a Web-based file-sharing site.
Therefore, email and Web security gateways are an important first line of defense against accidental and malicious breaches. These gateways are commonly used to inspect inbound traffic for spam and malware, but they can also be deployed to monitor outbound traffic. An internal security gateway sits in- line and acts as a relay, or proxy, to Web and email traffic that employees generate.
Gateway offerings from vendors such as Barracuda Networks, Cisco IronPort, McAfee, and WebSense have data loss protection features. As the traffic passes through the gateway, the DLP module inspects it for terms that are known to be sensitive within a company. It also looks for patterns involving specific data types, such as credit card and Social Security numbers, or specific classification labels on files that shouldn't leave the corporate network. If this sort of data is found to be moving out of the network, that could raise red flags. The traffic would then be blocked and the user notified. Alerts about a potential policy violation can be sent to a variety of recipients, including the security team, human resources, and the user's supervisor.
In addition to analyzing Web and email traffic, network-based DLP products can monitor protocols and services, including instant messaging, social networking sites, peer-to-peer file sharing, and File Transfer Protocol.
However, encryption can blind DLP and other gateway security products. If users are savvy enough to encrypt the data before sending it or use an encrypted network transmission method such as SSH/SCP or Tor, the data will bypass network-based DLP. To help address this limitation, DLP products typically include options for host- and storage-based DLP, which we'll discuss later.
Another network-level option is a behavioral anomaly detection system, from companies like Lancope and Riverbed Technologies. These products create a baseline of normal network activity and then send alerts when activity deviates from the baseline. For example, say a computer on the network typically touches about 12 other computers and servers, and transfers about 100 to 200 MB a day. If one day that computer touches 20 or more other systems or transfers 500 MB from a file server or a database, the behavioral anomaly system alerts an administrator.
Carnegie Mellon University's CERT Insider Threat Center has identified several insider attacker behaviors, one of which shows that insider attackers usually act within 30 days prior to leaving their employers. They download data from a company server to their workstation, then email it out, burn it to a CD, or copy it to a flash drive. The bulk data download is where a network anomaly detection system could detect the user's activity and flag it.
However, behavioral anomaly detection systems have drawbacks. For one, they can't send you an alert saying, "Looks like Bob is trying to steal a bunch of records." Instead, IT gets reports on odd application and network behavior, and it's up to security staff to investigate. That means digging into logs, reviewing network activity, and talking to people. Investigations may turn up harmless, though unusual, activity. IT and security teams must be prepared to invest time and effort in properly tuning a behavioral anomaly system, parsing reports, and investigating alerts to get value from such a system.
IT can also use tools designed to watch for anomalies in databases. They're prime targets for insiders because they contain valuable corporate information. Database activity monitoring products from vendors such as Imperva and IBM can provide insight into the activities between users and the database server. DAM products operating at the network or host layer and can detect unusual behavior, such as a user accessing 1,000 records when that person typically only views 30 or 40 a day.
Protect The Host
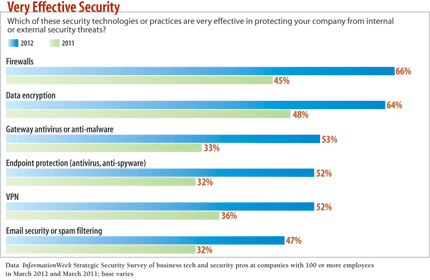
Host systems, such as user laptops and tablets, must also be protected against intentional and accidental breaches. Encryption is an effective way to do this; 64% of respondents to the our Strategic Security Survey rated encryption as very effective at protecting companies from security threats. Encrypting laptops, removable media, and mobile devices can prevent a significant portion of breaches caused by the loss or theft of a computer or mobile device. Policies must be configured and controls put in place to enforce encryption, along with strong password policies and the ability to remotely wipe lost devices.
Encryption can also be applied based on the content of files that are being copied to removable media, smartphones, and email messages. Products such as Credant's Mobile Guardian and McAfee's Total Protection for Data can proactively encrypt data as it's written to mobile devices and removable media. As a bonus, some state data breach laws will exempt companies from having to notify customers if the data was encrypted when it was lost or stolen.
Companies with stringent security requirements can block outright the use of removable media such as flash drives. Many endpoint protection suites, like Symantec Endpoint Protection and McAfee's DLP, can block all USB flash drives or only allow certain ones to be used.
Putting proper access and auditing controls around sensitive data sources, such as file servers, can also thwart insiders. One option is to enable basic file- and folder-level auditing, which will track user attempts to elevate access privileges and install software. While that sounds easy, the challenge is that many companies don't fully understand where their sensitive data lives. Without knowing that, file and folder auditing has limited value.
The first step is to identify exactly where sensitive data is stored. DLP products have added data enumeration capabilities to help IT identify where content such as Social Security numbers, health records, and credit card data is stored. Once that data has been identified, consolidated, and secured with the appropriate user permissions, then file and folder auditing needs to be enabled and logged via a central logging or security information and event management (SIEM) tool. Alerts can be configured when access failures occur and when a user outside a privileged group gains access to a server storing sensitive information.
Monitoring configuration changes to workstations and servers and sending alerts about them is another important step. These sorts of changes can indicate that malicious insiders are in the midst of or preparing for an attack by elevating their workstation privileges to administrator level, adding new hardware to copy data, or attempting to cover their tracks by clearing or disabling logs.
SIEM and specialized change management software that can alert you to changes as they occur include Tripwire Policy Manager and NetIQ Secure Configuration Manager. An added benefit to using change and configuration management tools is that they typically include workflow management to address, approve, and remediate changes that have been made.
Finally, IT must remember to log security information, review the logs, and act upon the data found there. Consider this conclusion from the 2011 Verizon Data Breach Investigation Report: "All too often, evidence of events leading to breaches was available to the victim but this information was neither noticed nor acted upon." In Verizon's 2012 report, the trend continues: 84% of victims in the study unknowingly possessed evidence of a breach in their logs. That stat reflects a failure to properly monitor and act upon existing logs that could detect insider attacks, which is why one of Verizon's top recommendations this year for large organizations is to "monitor and mine event logs."
The Human Factor
Research has shown that the majority of malicious insider attacks are caused by disgruntled employees and employees who plan to leave the company because of expected layoffs or to take a new job. And even if there isn't an employee with a grudge, users fall prey to phishing attacks and click on malicious links on social networking sites that lead to breaches. The human element is truly the most difficult to secure.
The first step when it comes to securing people is to establish well-defined, easy-to-understand policies. Unfortunately, from my experience with numerous security architecture and policy reviews, many companies fail at this. Policies tend to be long, complicated, and difficult for the average employee to read and understand. The result is that employees either read the policy and don't follow it because they didn't get it, or they just don't bother to read it.
Don't create policies simply to check off an item on an audit or compliance list. Instead, give your employees direction on expected behaviors and requirements, and explicitly define prohibited activities. Make sure your policies address hiring practices, such as background checks; data handling and classification; acceptable use of company resources; security awareness; and training.
Put in place data classification policies and practices that define what systems are allowed to store particular types of data, how that data can be transmitted over the network, any requirement for encryption, and if it can be stored on mobile devices and removable media. Employees who work with sensitive data and systems that store this data should be updated regularly on data classification policies.
Training is critical if you want employees to adhere to policies. Resources available to help companies create training programs include the SANS Institute's Securing The Human Program and the Offensive Security team's Corporate Security Awareness Training. And InformationWeek's "Security: Get Users To Care" report has practical tips on getting employees to buy in to corporate security policies.
Physical security is often overlooked when considering how to prevent insider attacks, but theft is a crime of opportunity. You want to monitor sensitive locations and limit employees' access to them to reduce that opportunity.
Shut The Door
Preventing insider threats requires that you watch out for technological exploits and also constantly monitor human behavior. That's a tough combination, particularly when insiders have access to sensitive data. The key is understanding the attacks, the possible motivations, and the primary areas where controls can be most effective. Start by identifying and prioritizing the information you need to protect and then add or expand technological controls where appropriate on your network and host systems.
And don't forget the human factor. Write policies that people can understand and follow. Train employees in safe computing habits. And be vigilant in monitoring user activity.
A layered approach using security controls at the network, host, and human levels will go a long way toward mitigating insider threats. As the 2012 Verizon report says that for the third year in a row, nearly all internal breaches were a result of "deliberate and malicious actions." To truly close the door on insider threats, your security efforts must be just as deliberate.
About the Author
You May Also Like




