Recruit, Reward & Retain Cybersecurity ExpertsRecruit, Reward & Retain Cybersecurity Experts
How to create a better working environment for security professionals.

January is a good time to get strategic and think about the bigger picture. The glut of security breaches in 2014 has increased the pressure to hire and retain cybersecurity experts, in a market that was already experiencing an acute shortage. Ranging from 50,000 to 500,000 or more depending on whom you ask, the gap between supply and demand is large and growing.
At the same time, I still hear from many clients who perceive security as an annoyance and a sunk cost, not a proactive and positive force for their company. This opinion varies by role – our research shows CISOs and senior IT managers are less prone to this mindset than the teams with more operational roles.
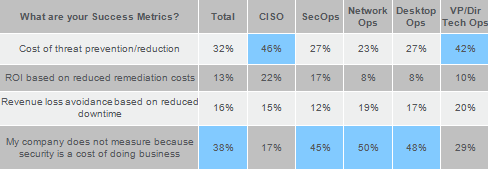
Greenberg Survey sponsored by Intel Security, November 2014, N=700.
Perception is important because it translates into attitude to the team, communicated in body language, nicknames, and reluctance to comply with rules. Security staff may play along and participate in the jokes, but internally being treated this way in your job is slowly soul-destroying.
When asked about what keeps them enthusiastic about their jobs, security professionals will often mention meaningful and challenging work, opportunities for professional development, and a belief that their skills are being put to good use. When asked about the challenges in their jobs, top of mind are lack of understanding from senior management and lack of adequate investment.
Here are three ideas for creating a better work environment for your security team:
1) Reaffirm that the threat is real. People are trying to get into your network to steal your data. This is not meant to be a scare tactic, but an awareness campaign. Show the company why your security team matters and that it’s not just a necessary evil. Talk about public breaches or internal incidents. Demo how to hack an online account. How did it happen and what can you do about it? Communicate that your team does more than make security rules, they are also the people who work long hours in the event of a breach.
2) Make it personal. What aspects of the job does your staff dislike? Try to reduce or eliminate those tasks through automation, education, or managing up. Then give them challenging tasks and more of what they like doing. Use words that indicate support and positive reinforcement. Make each member feel respected and rewarded, that they are making a difference, and are an important part of the Security Battleground.
3) Have fun. Send them to conferences and give them time to learn new things and participate in local security events and hackerspaces. Invite consultants or experts that have experienced a breach to share war stories. Interacting with smart, like-minded people in similar situations helps to build team spirit and a sense of value beyond the cubicle.
Banks do not view vaults, cameras, or safety deposit boxes as an annoyance, but as an important part of minimizing their risks. Customers would not deal with a bank that reduced expenses by keeping cash in cardboard boxes in a back room with only a simple door lock for security. Your enterprise information security should not be viewed as an impediment to the business, but as a critical part of making the Internet a valuable and secure business tool.
About the Author
You May Also Like




