'Operation Sharpshooter': Lazarus Revived or False Flag Operation?
McAfee Labs has homed in on a new attack targeting critical infrastructure that they call 'Operation Sharpshooter.' However, while there is technical overlap with the Lazarus Group, there's also the possibility of a false flag operation.

McAfee Labs researchers have zeroed in on a new cyber campaign targeting critical infrastructure, including nuclear, defense, energy, and financial facilities in multiple countries including the US, which they are calling "Operation Sharpshooter."
This cyber attack leverages an in-memory implant, which can download and retrieve a second-stage implant -- dubbed Rising Sun -- that gives the ability for additional exploitation and reconnaissance within the victim's network. This particular campaign seems to target individual or organizations that have access to critical data.
However, the most intriguing part of Operation Sharpshooter is some of the technical ties between this organization and the North Korea-backed Lazarus Group, specifically, code that was used to create the Trojan Duuzer backdoor in 2015. Some of the same code now appears in Rising Sun.
Lazarus is thought to be responsible for a string of cyber attacks dating back several years, including the Sony Pictures hack and the WannaCry ransomware. (See WannaCry Continues Rampage 18 Months After First Outbreak.)
Still, McAfee researcher warn that this could very well be false flag operations designed to confuse victims and investigators, or cast blame elsewhere.
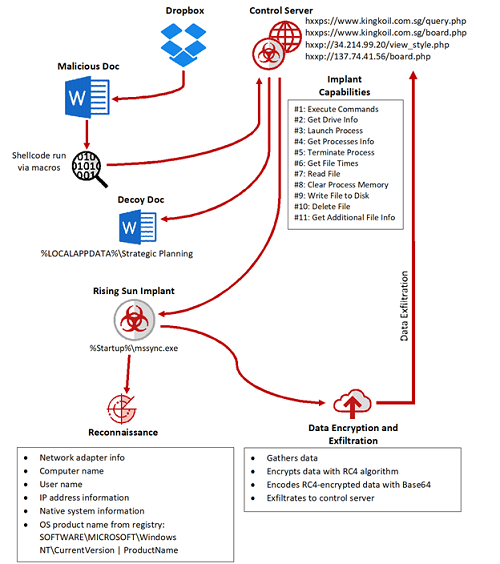
Infection flow of the Rising Sun implant, which eventually sends data to the attacker's control servers.
\r\n(Source: McAfee)\r\n
Either way, these malicious tools are now in wider circulation.
"To our knowledge, this code has not been discovered on the Dark Web or other forums and was last used by Lazarus group in 2015," Ryan Sherstobitoff, a senior analyst for Major Campaigns at McAfee, wrote in an email to Security Now. He added:
"In our research, we were not able to find any evidence of its existence on the Dark Web and forums, but that still doesn't rule out that it is out there somewhere. What we do know that if it is, it's extremely difficult to find the source code. However, another possibility is that Lazarus may have shared this code with another actor or provided access to others in a more secretive setting. At this point we can't draw the conclusion that Lazarus is responsible, but what we do know is that tools from Lazarus are being used in this global campaign."
In its December 12 report, the McAfee team noted that Operation Sharpshooter, and specifically the Rising Sun implant, has been found in 87 different organizations throughout the globe, mainly infecting English-speaking facilities or regional offices.
Beginning on October 25, researchers began seeing a series of malicious documents carrying the name "Richard." These were created using a Korean-language version of Microsoft Word and delivered through either an IP address or Dropbox.
The documents appeared to be a job description, but actually carried a malicious micro that used shellcode to inject the Sharpshooter downloader into the memory of Word. Once planted, the downloader retrieves Rising Sun.
Once downloaded, Rising Sun creates a backdoor that allows the attacker or attackers to conduct a large-scale reconnaissance scheme within the network through a control server, with the ability to capture information including: network adapter info, computer name, username, IP address, native system information and operation system product name from registry.
"The Rising Sun implant has the capabilities of taking machine level information, running arbitrary code/commands which can give the attacker additional access to the system," Sherstobitoff wrote in the email. "This information can be used to further infiltrate systems and gather more sensitive information. This is likely the beginnings of a larger attack, given the number of victims around the globe and the potential for countless more that may have not yet been discovered. Given the victimology, the actor potentially had access to a wide range of very sensitive information from governments, energy companies, etc."
In his email, Sherstobitoff noted three unique parts of this attack:
The initial part of the attack that used an in-memory implant with the embedded shellcode is unusual and different from typical malicious documents used in other campaigns.
The decoy documents are dynamically hosted and are retrieved once the infection is successful, which enables the attacker to quickly switch out the lures and adapt them to different targets.
Finally, the attackers managed to enhance the Duuzer backdoor with Rising Sun's framework by adding features such as RC4 encryption. Addition, Rising Sun only has two variants, making it unique to this attack.
Sherstobitoff added that even though McAfee is warning about the attack, Sharpshooter and Rising Sun continue to appear, targeting new victims.
"The Rising Sun implant is still active and there could potentially be more targets uncovered," Sherstobitoff added. "We had discovered additional IOCs [indicators of compromise] after the initial collection period that indicated that they continued to target additional victims and create infrastructure."
Related posts:
— Scott Ferguson is the managing editor of Light Reading and the editor of Security Now. Follow him on Twitter @sferguson_LR.
Read more about:
Security NowAbout the Author
You May Also Like




