
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Time to Get Strict With DMARCTime to Get Strict With DMARC
Adoption of the email authentication and policy specification remains low, and only about a tenth of DMARC-enabled domains enforce policies. Everyone is waiting for major email providers to get strict.
October 18, 2024

The state of DMARC email authentication and security standards looked so promising at the beginning of 2024.
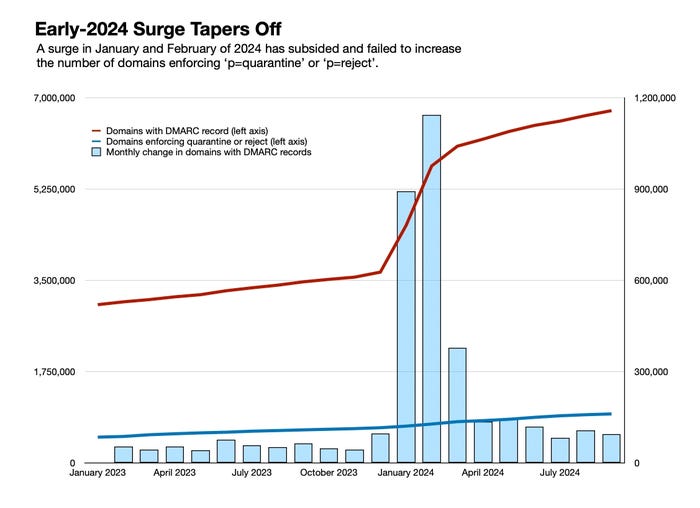
Google and Yahoo had set a deadline of February for bulk email senders to adopt a Domain-based Message Authentication, Reporting and Conformance (DMARC) policy. As companies scrambled to meet the deadline, the number of email domains with a valid DMARC record jumped 60% in two months. As of September, nearly 6.8 million domains had email sender authentication configured.
Even with that surge earlier in the year, the reality is that businesses continue to be slow in setting up email authentication on their domains. The adoption lag is especially pronounced in making the switch from DMARC's minimum-baseline policy of "p=none" to more stringent policies. Enforcement means nonauthenticated emails get quarantined or rejected. The share of DMARC-enabled domains with an enforced policy has actually gone down from a high of 18% a year ago to less than 14% today.
While Google's and Yahoo's actions forced many companies to adopt DMARC, most of them — spurred by concerns about blocking legitimate messages — haven't adopted the quarantine or reject policies, says Seth Blank, chief technology officer at Valimail, a provider of email security services.
"Google and Yahoo put the requirements out, the ecosystem got a shot in the arm, and the message was heavily about security — so the people who cared about security did something," Blank says. "There's still a large part of this market that has not moved, hasn't taken any steps, even this bare minimum that we're seeing here."
The DMARC protocol aims to add authentication to the Internet's email infrastructure, requiring that email senders adopt two verification technologies — Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) — and specify a policy for how other servers should handle mail from a sender not part of an authorized domain. In October 2023, Google and Yahoo required that email marketers — anyone sending more than 5,000 emails daily through the services — set up DMARC. The move resulted in a significant reduction in nonauthenticated emails, with Google seeing two-thirds less (65%) unauthenticated messages sent to Gmail users and 265 billion fewer unauthenticated messages sent so far this year, according to company data released last week.
Fear, Uncertainty, and DMARC
The adoption rate of DMARC has roughly doubled over the past year — from about 55,000 domains adding new DMARC records each month in 2023 to 110,000 domains per month in Q3 2024, according to Valimail data. Yet, even at that rate, it would still take nearly 15 more years for the top 25 million domains to get on board.
Source: Author, with data from Valimail
Moreover, DMARC adoption has been spotty. While more than 60% of the organizations in some industries, such as manufacturing and healthcare, have adopted DMARC, only one in five have actually moved from the lowest security policy ("p=none") to the highest ("p=reject"), according to data from EasyDMARC, an email-authentication services firm. Some sectors, such as nonprofits and charity organizations, have increased adoption over the year, but fewer than 8% of domains are using DMARC.
Because email is critical to business operations, organizations worry that stricter enforcement will result in lost messages, especially because DMARC is not necessarily an easy technology to implement and maintain, says Kelly Molloy, director of network development for DomainTools, an Internet intelligence firm.
"The fear is, especially if you are a company who depends on leads via email, that you're going to miss messages from interested parties — from customers and potential customers — if you start doing [strict enforcement]," she says. "A lot of companies are being conservative and are not going further than they really need to ... because it does take resources."
Waiting for the Other Shoe to Drop
The stalled adoption cycle will likely attract another major move by Google, Yahoo, and other large consumer email services, says Hagop Khatchoian, technical services team lead at EasyDMARC.
"They [Google and Yahoo] are just forcing everyone to have at least 'p=none' ... to just have a basic policy without any enforcement — we foresee that will be changed in the next few years," he says. "But you can't just go on and tell everyone, 'Hey, you need 'p=reject' ... because if you have a small misconfiguration in your email ecosystem, and you have an enforced policy, then your own legitimate emails will be blocked as well."
Valimail's Blank agrees, noting that the major email services — Google, Microsoft, and Yahoo, as well as major providers in other countries — are unlikely to wait long before again turning the screws on unauthenticated email.
"The sending community or the receiving community will mandate the next steps because they know [authentication] is the single most important input into their system — being able to know who sent an email with far more certainty," he says. "We're going to see more action there ... and it will take years, but it's not going to be five to 10 years. It's probably two, three, maybe four."
None's Not Nothing, But Close to It
With another DMARC push in the cards from major email services, organizations should plan to shift their DMARC policies from "none" to a higher level of enforcement.
The three levels of enforcement are:
p=none: Mail that fails authentication checks are still delivered.
p=quarantine: Authentication failure results in email being quarantined, possibly delivered to a user's spam folder or to an organization's quarantine storage.
p=reject: Authentication failure leads to the email being discarded, although some service providers may instead quarantine the email in a separate folder.
Every enforcement level can produce reports, and companies should monitor the reports to check for issues and anomalies, says Valimail's Blank.
"DMARC at 'p=none' with no reporting is syntactically equivalent to not having DMARC at all," he says. "The value of DMARC comes from reporting and working toward a policy that is not 'none.' If you have 'p=none' and you're not getting reports, there is nothing you can do, there is nothing you can see, there is nothing you can fix."
Getting reports from the DMARC infrastructure is an important level of visibility for companies as they pursue better email security. Large companies are not the only organizations to see significant abuse of email, so any firm that sends email should monitor their DMARC reports, he says.
About the Author
You May Also Like

