We Are the PerimeterWe Are the Perimeter
End users, not technology, define the boundaries of the enterprise. Security strategies must protect this new perimeter.

You and I, engineers and software developers, every single employee in your company are part of the collective “we,” and as such each of us has a critical role to play in fortifying our security perimeter and preserving privacy. That perimeter surrounds our direct enterprise and our data, as well as the products, services, and solutions we deliver to our customers.
The world of computing is rapidly evolving. The traditional model, where desktop computers were essentially fixed in place and security and privacy efforts were primarily focused on protecting the network perimeter, is obsolete. So what replaces this model?
With corporate laptops and tablets, and employees bringing their own devices, the security perimeter has shifted, and it is now swayed by the choices of each employee. This shift brings tremendous benefits, but not without a significant potential for risk. In today’s fast moving environment, the question becomes: Have you, and every employee within your company, stayed abreast of what it takes to protect your security perimeter?
Are you prepared to secure your company’s perimeter as the Internet of Things (IoT) expands at an accelerating rate?
This chart from Daily Infographic*, prepared by Xively.com*, shows the projected trajectory for the IoT, and underscores the need to ensure each and every one of us is prepared to embrace these advances with proper security and privacy precautions.
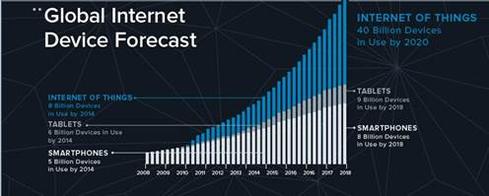
http://dailyinfographic.com/wp-content/uploads/2014/03/Xively_Infographic-2-1.jpg
To be clear, the Internet of Things should make our professional and personal lives easier; but it will not necessarily make them simpler – at least in the short term.
In conjunction with the incredible growth and opportunities ahead, we must identify early on the implications that emerging technologies will have on how data is collected, handled, stored, shared, managed, respected, and deleted.
When one careless choice can threaten an entire company’s security perimeter, what steps do each of us need to take?
The answer is as simple as it is daunting. Each of us needs to increase our knowledge of potential risks and apply it consistently as we make security choices.
It means fundamentally changing company culture. It is not enough to understand how technology works and connects; we must internalize the privacy and security implications of those tools and connections and create an environment that proactively and automatically takes the right actions.
It means educating others within our companies and communities about the opportunities and risks each person’s security choices entail, in a way that is easily understandable and compelling so people are both empowered and motivated to make the right choices.
It means watching out for each other so when one person’s actions open a potential security or privacy gap, another person is right there to help prevent the risk. It’s the “if you see something, say something” concept, applied to security and privacy.
It means recognizing that technical controls alone cannot protect us from rapidly changing attack structures or the complexity of new technologies. It’s time to step up to the expanded role and be part of the solution — we are all a vital part of the security and privacy perimeter.
*Other names and brands may be claimed as the property of others.
About the Author
You May Also Like



_Nils_Ackermann_Alamy_Stock_Vector_.jpg?width=700&auto=webp&quality=80&disable=upscale)
