
News, news analysis, and commentary on the latest trends in cybersecurity technology.
How to Protect Your Phone from Pegasus and Other APTsHow to Protect Your Phone from Pegasus and Other APTs
The good news is that you can take steps to avoid advanced persistent threats. The bad news is that it might cost you iMessage. And FaceTime.

Amnesty International reports that Pegasus, the "legal surveillance software" from Israeli company NSO Group which has been used to surveil human rights activists, journalists, and lawyers around the world, has been found on 37 devices belonging to 35 journalists in El Salvador as late as last November.
Over the past few months, I received a lot of questions from concerned users worldwide about how to protect their mobile devices from Pegasus and other similar tools and malware. First, let me warn you that no list of defense techniques can ever be exhaustive. Additionally, as attackers change their modus operandi, defense techniques need to adapt.
We should start by saying that Pegasus is a toolkit sold to nation-states at relatively high prices. The cost of a full deployment may easily reach millions of dollars. Similarly, other advanced persistent threat (APT) mobile malware may be deployed through zero-click zero-day exploits. These are also extremely expensive — as an example, Zerodium, an exploit brokerage firm, pays up to $2.5 million USD for an Android zero-click infection chain with persistence.
From the start, we come to an important conclusion — nation-state sponsored cyberespionage is a vastly resource-intensive endeavor. When a threat actor can afford to spend millions, tens of millions, or even hundreds of millions of dollars on their offensive programs, it is very unlikely that a target will be able to avoid getting infected. To put it bluntly: It’s not a question of whether you get infected, it’s just a matter of time and resources before you get infected.
Now for the good news — exploit development and offensive cyberwarfare are often more of an art than an exact science. Exploits need to be tuned for specific OS versions and hardware, and they can be easily thwarted by new OSes, new mitigation techniques, or even small random events.
With that in mind, avoiding infection also comes down to making things more expensive and difficult for the attackers. Although we may not always be able to prevent the successful exploitation and infection of our mobile device, we can try to make it as hard as possible for the attackers. How do we do this in practice? Here’s a simple checklist:
On Apple iOS Devices
Reboot daily. According to research from Amnesty and CitizenLab, the Pegasus infection chain often relies on zero-click zero days with no persistence, so regular reboot helps clean the device. If the device is rebooted daily, the attackers will have to reinfect it over and over again. Over time, this increases the chances of detection; a crash or artifacts could be logged that give away the nature of the stealthy infection.
This is not just theory, it’s practice — we analyzed a case in which a mobile device was targeted through a zero-click exploit (likely FORCEDENTRY). The device owner rebooted their device regularly and did so in the 24 hours following the attack. The attackers tried to target them a few more times but eventually gave up after getting kicked a few times through reboots.
Disable iMessage. iMessage is built into iOS and is enabled by default, making it an attractive exploitation vector. Because it’s enabled by default, it is a top delivery mechanism for zero-click chains. For many years, iMessage exploits were in high demand, with top payouts at exploit brokerage companies.
"During the last few months, we have observed an increase in the number of iOS exploits, mostly Safari and iMessage chains, being developed and sold by researchers from all around the world. The zero-day market is so flooded by iOS exploits that we've recently started refusing some (of) them," Zerodium's founder Chaouki Bekrar wrote back in 2019 to Wired.
We realize this may be very difficult for some (more later), but if Pegasus and other high-end APT mobile malware is in your threat model, this is a tradeoff worth taking.
Disable FaceTime. Same as above.
Keep the mobile device up to date. Install the latest iOS patches as soon as they come out. Not all attackers can afford zero-click zero days; many of the iOS exploit kits we are seeing target already patched vulnerabilities. Nevertheless, many people run older phones and postpone updates for various reasons. If you want to be ahead of (some) nation-state hackers, update as soon as possible and teach yourself not to need emojis to install the patches.
Don't ever click on links received via SMS messages. This is simple advice, yet effective. To save the cost of zero-click chains, many hackers rely on one-click exploits. These arrive in the form of a message — sometimes by SMS, but also via other messengers or even email. If you receive an interesting SMS (or any other message) with a link, open it on a desktop computer, preferably using TOR Browser or a secure non-persistent OS such as Tails.
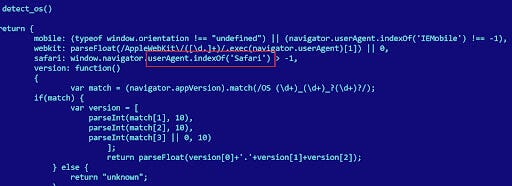
Browse the Internet with an alternate browser such as Firefox Focus. Despite the fact that all browsers on iOS pretty much use the same WebKit rendering engine, some exploits do not work well (see LightRighter / TwoSailJunk) on some alternate browsers.
Source: Costin Raiu, Kaspersky GReAT
User agent strings on iOS from Chrome: Mozilla/5.0 (iPhone; CPU iPhone OS 15_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) CriOS/96.0.4664.53 Mobile/15E148 Safari/604.1
User agent strings on iOS from Firefox Focus: Mozilla/5.0 (iPhone; CPU iPhone OS 15_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) FxiOS/39 Mobile/15E148 Version/15.0
Always use a VPN that masks your traffic. Some exploits are delivered through GSM operator MitM attacks, when browsing HTTP sites or by DNS hijack. Using a VPN to mask the traffic makes it difficult for your GSM operator to target you directly over the Internet. It also complicates the targeting process if the attackers have control over your data stream, such as while in roaming.
Do note that not all VPNs are the same, and not every VPN is fine to use. Without favoring any specific VPN, here’s a few things to consider when purchasing a VPN subscription:
“Purchasing” means just that — no “free” VPNs.
Look for services that accept payment with cryptocurrencies.
Look for services that do not require you to provide any registration info.
Try to avoid VPN apps — instead, use open source tools, such as WireGuard and OpenVPN and VPN profiles.
Avoid new VPN services and look for established services that have been around for some time.
Install a security application that checks and warns if the device is jailbroken. Frustrated from getting kicked over and over, the attackers will eventually deploy a persistence mechanism and jailbreak your device in the process. This is where the chance of catching them increases tenfold, and we can take advantage of the fact that the device is jailbroken.
Make iTunes backups once per month. This allows you to diagnose and find infections later, through the use of the wonderful MVT package from Amnesty.
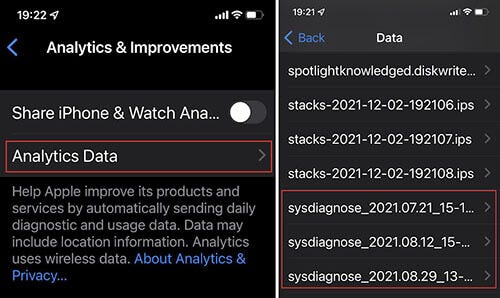
Trigger sysdiags often and save them to external backups. Forensics artifacts can help you determine at a later time if you have been targeted. Triggering a sysdiag depends on the phone model — for instance, on some iPhones, you do this by pressing VOL Up + Down + Power at the same time. You may need to play with this a couple of times until the phone buzzes. Once the sysdiag is created, it will appear in diagnostics:
Source: Costin Raiu, Kaspersky GReAT
On Android Devices
Reboot daily. Persistence on latest Android versions is difficult; many APTs and exploit sellers avoid any persistence whatsoever!
Keep your phone up to date. Install all the latest patches.
Don't ever click on links received in SMS messages.
Browse the Internet with an alternate browser. Again, try using Firefox Focus instead of Chrome.
Always use a VPN that masks your traffic. Some exploits are delivered through GSM operator MitM attacks, when browsing HTTP sites or by DNS hijack.
Install a security suite that scans for malware and checks and warns if the device is jailbroken.
At a more sophisticated level, always check your network traffic using live IOCs. A good setup might include a Wireguard always-on VPN to a server under your control that uses pi-hole to filter out bad stuff and logs all the traffic for further inspection.
Bro, This Makes No Sense! Life Without iMessage Is Green and Emoji-less.
Source: Costin Raiu, Kaspersky GReAT
Ah, yes, I hear you — been there myself. Talking to my friend Ryan Naraine yesterday, he said, “iMessage and FaceTime — these are the reasons why people use iPhones!” and for sure, he’s right. I myself have been an iPhone user since 2008, and I think iMessage and FaceTime were two of the greatest things Apple added to this ecosystem. When I realized that these are also some of the most exploited features that let nation-states spy on your phone, I tried to escape the iMessage Hotel California. The hardest thing? Getting the family to stop using it too. Surprising as it may sound, this was one of the most difficult things in this whole security saga.
At first, I tried to switch everyone to Telegram. This didn’t go too well. Then, Signal got better, implementing video calls and group calling. In time, more and more friends started moving onto Signal. And this worked well with my family, too.
I’m not saying you should do the same. Perhaps you can keep those apps enabled and live happily and malware free — truth be told, Apple greatly improved the security sandbox around iMessage with BlastDoor in iOS 14. Nevertheless, the FORCEDENTRY exploit NSO used to deliver Pegasus bypassed BlastDoor, and, of course, no security feature is ever 100% hack-proof.
So what is the best of both worlds, you may ask? Some people, including myself, have multiple iPhones — one where iMessage is disabled, and a “honeypot” iPhone where iMessage is enabled. Both are associated with the same Apple ID and phone number. If someone decides to target me this way, there’s a good chance they will end up in the honeypot phone.
Keep in mind that I weighed the costs and benefits for my own situation. I have experienced these kinds of attacks and therefore know I could be a target again. To avoid this higher level of risk, I will take more effort and make more sacrifices of features I find both useful and fun. If you are taking actions that might make a nation-state notice you and consider you an enemy, you might want to lock down your phone as much as possible.
Otherwise, maybe just set up a honeypot.
About the Author
You May Also Like

