
Cybersecurity In-Depth: Feature articles on security strategy, latest trends, and people to know.
Is It OK to Take Your CEO Offline to Protect the Network?Is It OK to Take Your CEO Offline to Protect the Network?
Are you asking the right questions when developing your incident response playbook? What security tasks are you willing to automate?

Let’s say there’s a ransomware attack exploiting a known vulnerability, and you know that vulnerability is present on your CEO’s laptop. Should your CEO be taken offline automatically? Do you wait for the laptop to be compromised first? Do you quarantine the laptop before the vulnerability is exploited to save the network?
These are all questions to take into account when developing a playbook for your company. And you'd better be sure that the data you are relying on to make those decisions is accurate.
The way to address this nuanced issue starts by answering a broad question: What level of risk are you willing to assume? No matter how you choose to respond, there will be ripple effects in both security and operations.
Security teams have two levers available to them to deal with the millions of vulnerabilities in a typical company. The first is prioritization: Which vulnerabilities pose the greatest risk to your organization? The second is automation, which lets you get more done faster.
In some cases, like patching Microsoft vulnerabilities, automation should be a no-brainer because the overall impact on security and operations aren’t very high. On the other hand, deactivating your e-commerce storefront in order to apply updates, especially if it’s your company’s top money-maker, should probably require a human decision.
What will it take to actually automate security? Even a stressful situation like disconnecting your CEO can be automated and taken off your security team’s plate if you have convincing data. Let’s look at a few factors to assess when deciding whether to automate or manually prioritize the vulnerabilities your company may face.
Business Risk vs. Security Risk
If you take your CEO offline, surely you risk a phone call or text message littered with four-letter words when access suddenly vanishes. But there’s a business risk to not having the CEO available to lead the company, too. The point at which you automate is when the security risk the CEO’s device poses is larger than the business risk of cutting off their access.
You need to have the utmost confidence in the data measuring both sides of the risk equation to make the right call. That data should also inform how aggressively you want to act.
It’s also important to consider the standards you’re holding yourself to based on your risk tolerance. If you’re trying to stay ahead of attackers in that small percentage of dangerous breaches, automation is your friend for patching, remediation, and other preventative measures. In that case, it’s faster to not even have a human involved.
Of course, it’s also important to ensure that these are rare events. If your CEO is taken offline every week, the conversation may end with a pink slip instead of an angry text.
What Are the Odds?
Data drives all these decisions, but it needs to be convincing material for companies to trust letting go of manual actions. We crunched the numbers to see what the probability is of a CEO actually getting locked out of a network due to an attack.
At baseline, we know that about 2% of all Common Vulnerabilities and Exposures (CVEs) are ever exploited. Within that 2%, only about 6% of the exploits are seen at more than 1% of organizations. The likelihood, then, of one employee – in this case the CEO – becoming compromised as a target of opportunity is very small. Of course, if you have evidence that the CEO is being targeted, you should be taking extreme preventative measures, and these “target of opportunity” statistics don’t apply.
To put that into perspective: The chances of your CEO being hit by any single target of opportunity vulnerability is about 0.0012%.
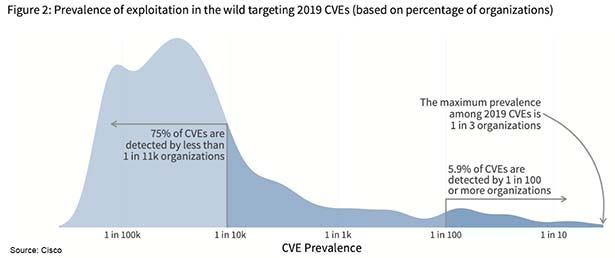
Prevalence of exploitation in the wild targeting 2019 CVEs (Source: Cisco)
Getting Comfortable With Automated Security
When the numbers are this clear, it becomes easier to turn over the keys on manual security activities. If you have the proper analysis correlation and large sets of data, you can be satisfied that any security decision is meticulously calculated. Incontestable data not only unlocks the confidence to automate, it also frees up IT and security teams to do things more important to their day-to-day operations.
Of course, this process does take some legwork up front. You first need to identify what business operations are associated with an asset, like a CEO’s laptop, and how critical those operations are. Then you can begin making your assessment about where the sweet spot is between business and security risk.
If the integrity of your data is strong enough, you can start automating procedures instead of losing valuable time acting on things that may never even happen.
About the Author
You May Also Like

