
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Can Zero-Knowledge Cryptography Solve Our Password Problems?Can Zero-Knowledge Cryptography Solve Our Password Problems?
Creating temporary keys that are not stored in central repositories and time out automatically could improve security for even small businesses.
June 28, 2022

While multifactor authentication, single-sign-on infrastructure, and stronger password requirements have improved the security of most enterprise identity and access management (IAM) environments, the longevity of passwords continues to pose problems for businesses, especially in granting temporary access to contractors and third-party partners.
A variety of vendors are trying to solve this problem. Last week, for example, data-security firm Keeper Security announced one-time shared passwords that allow companies to grant third-party partners temporary access to data and resources without adding them to the company's overall IT environment. The approach allows specific types of documents to be shared to a single user device, automatically removing access when the time expires.
The business case is all about securing access granted to contractors, says Craig Lurey, chief technology officer and co-founder of Keeper Security.
"We get asked constantly to allow short term, temporary access to third parties without requiring them to onboard as a licensed user," he says. "With this new feature, there is not 20 steps anymore. It is just instant, but preserving that encryption, simplifying the secure-sharing process, and eliminating the need to send private information over text messages."
Credential Theft Is Big Business
Supply chain breaches, stolen credentials, and the proliferation of software keys and secrets continue to undermine IT and data security. In March, secrets-detection firm GitGuardian found that developers leaked 50% more credentials, access tokens, and API keys in 2021, compared to 2020. Overall, 3 out of every 1,000 commits exposed a sensitive password, key, or credential, the company said at the time.
Failing to protect software secrets, user passwords, and machine credentials can lead to compromises of application infrastructure and development environments. Attackers have increasingly targeted identities and credentials as a way to gain initial access to corporate networks. Last week, for example, software security firm Sonatype discovered that at least five malicious Python packages attempt to exfiltrate secrets and environment variables for Amazon environments.
"It remains yet to be known who the actors behind these packages are and what is their ultimate goal," Sonatype stated in an advisory on the issue. "Were the stolen credentials being intentionally exposed on the web or a consequence of poor OpSec practices?"
How Zero-Knowledge Encryption Protects Credentials
Managing the access credentials for data means avoiding centralized storage of sensitive keys — a security advantage of zero-knowledge encryption (ZKE) — and regularly expiring keys so that former contractors, partners, and employees no longer have access to data. ZKE breaks up keys in specific ways, using both cryptography and tokenization, to prevent any device or database from having all the necessary information to reconstitute the master keys to unlock data.
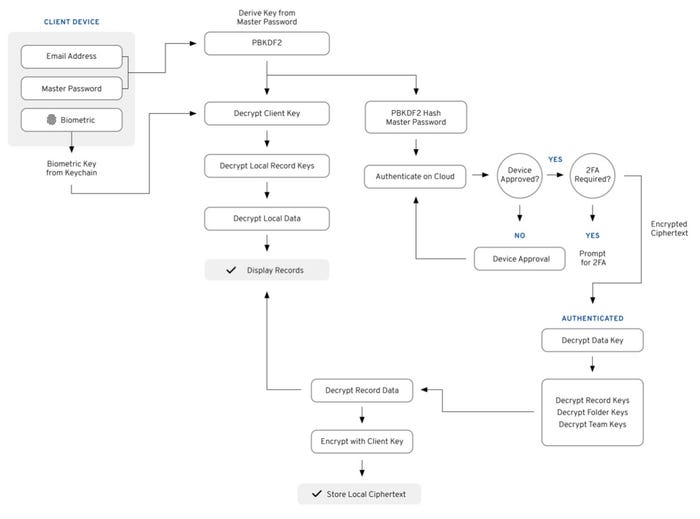
Source: Keeper Security
The move to de-emphasize master passwords and keys is part of the cybersecurity industry's effort to create a passwordless security infrastructure. Yet, in the end, most enterprises rely on some sort of password to secure massive stores of keys or unlock cloud IAM services, says Lurey.
"Every year, the platforms try to come up with new schemes to bury the password, [but] at the end of the day, those platforms still rely on passwords, especially for account recovery," he says. "There is a growing number of passwords and secrets that everyone has to deal with, whether you are on the tech side and you have to deal with API keys and software secrets, or on the personal side and the growing number of sites that require personal or private information."
Creating a zero-knowledge way of managing secrets and offering one-use, temporary passwords requires significant design effort and a move away from the consolidation among large brands that are assuming the mantles of identity providers, Lurey says.
"The reason why the password continues to be popular is because it is something that you have that can be used to encrypt and decrypt data at the end of the day," he says. "The passkeys, which are just passwords, are being stored by Apple, Google, and Microsoft, so those are being synched with other devices and onboard devices, but how do you sync those secrets — it is basically a rabbit hole of authentication issues."
The Passwordless Path Ahead
The focus on ZKE is relatively new, and the vast majority of companies protect their secrets using key management systems, says Andras Cser, vice president and principal analyst for security and risk at Forrester Research. The focus on passwordless technologies typically involves biometrics, QR-code-based authentication, pushing authentication tokens to mobile devices, and sending one-time passwords via e-mail or text message, he says.
"Because of phishing issues, OTP and passwordless is slowly replacing the static password for authentication. Identity management and governance (IMG) to onboard, review, and off-board contractors and third parties for access is very important in this flow," Cser says.
Whether ZKE takes off will likely depend on whether third-party identity services using de facto standards, such as the FIDO2 and WebAuthn passwordless standards, gain popularity. In a white paper acknowledging the slow adoption of FIDO and the future integration with WebAuthn, the FIDO Alliance outlined what its passwordless future would look like, using mobile devices as standardized authenticators and allowing credentials to be synced across devices.
The changes will make "FIDO the first authentication technology that can match the ubiquity of passwords, without the inherent risks and phishability," the white paper stated.
About the Author
You May Also Like

