Ransomware Groups Weathered Raids, Profited in 2024Ransomware Groups Weathered Raids, Profited in 2024
Cybercriminals posted nearly 6,000 breaches to data-leak sites last year — and despite significant takedowns, they continued to thrive in a record-breaking year for ransomware.
February 3, 2025

A surge in ransomware groups in 2024 left companies facing increased attacks, even as law enforcement ramped up investigations against well-known groups such as LockBit, and dismantled popular cybercriminal services, such as phishing-as-a-service provider LabHost and the encrypted messaging platform Ghost.
A pair of new studies outlines the state of play. Overall, more than 75 ransomware groups were actively compromising targets in 2024, compared to only 43 the prior year, according to a recent Rapid7 analysis. As a result, more than half of organizations suffered a successful attack, and the majority of those impacted shut down some operations leading to significant revenue loss, according to a large survey of IT and cybersecurity practitioners conducted by the Ponemon Institute.
As long as extortion continues to be profitable, organizations will have to contend with significant threats, says Trevor Dearing, director of critical infrastructure solutions at Illumio, a zero-trust security firm and sponsor of the Ponemon report.
"When some of those gangs were taken down, there was a dip in activity, but they get very quickly replaced, and that's the challenge," he says. "It's a battle that is is worth fighting and it does slow them down, but this is only part of the response we have to have."
The pace of compromises appears to be only accelerating, with about 15% more ransomware attacks in 2024, compared to the previous year, according to data collected by both NCC Group and Rapid7. Their tallies differed slightly, but trended in the same direction. And last month, the number of successful attacks claimed by ransomware groups averaged 18 per day, up from less than 15 in December, according to Rapid7's data.
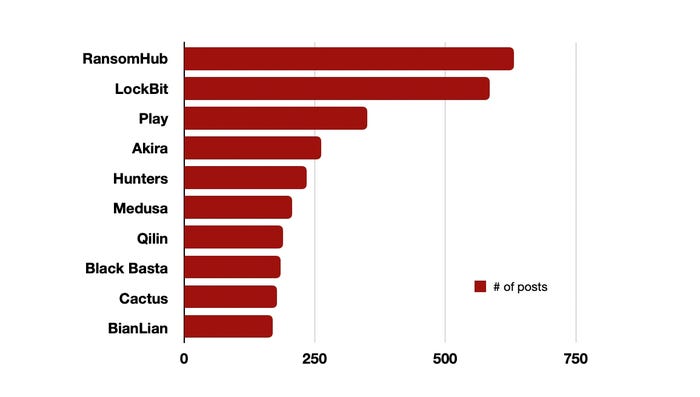
RansomHub, LockBit, and Play were the most prolific ransomware groups in 2024, as measured by the number of breach posts. Source: Author based on Rapid7 data
Overall, cybercriminals compromised nearly 6,000 victims, posting their information to public data-leak sites, with well-known ransomware groups — such as RansomHub, LockBit, and Play — making tens of millions of dollars each in ransom payments from victims, even as fewer victims paid lower average ransoms, the company found.
Laying Down the Law on Cybercrime
The ransomware gains came despite increased law enforcement activity. In September, European law enforcement disrupted the Ghost encrypted communications platform used by organized crime groups. In November, Canadian authorities arrested the hacker behind the compromise of 165 firms' Snowflake instances, who had demanded ransoms ranging from $300,000 to $5 million. And, in December, Israeli law enforcement arrested a 51-year-old LockBit developer in Israel.
While law enforcement efforts are having an impact on cybercriminal operations, their efforts appear to be fracturing the ecosystem, as more groups and a greater number of providers offer cybercriminal services, says Christiaan Beek, senior director of threat analytics for Rapid7.
"Law enforcement is really fighting hard to take on the biggest groups [that are causing businesses] a lot of problems, and we highly applaud those initiatives," he says. "But the money is really attracting people, and especially if you are in certain countries where you're hard to catch or protected by the government ... then [becoming a ransomware operator] almost feels like a safe option."
Paying Ransoms Is No Guarantee of Cyber Safety
Estimates of the ransom amounts paid by companies varied significantly, with ransomware specialist Coveware estimating that the victims paid a median of $200,000 in Q3 2024, while a survey of more than 2,500 companies conducted by the Ponemon Institute estimated the average ransom demanded to be $1.2 million.
And those figures do not include investigation and clean up costs, Illumio's Dearing says.
"There was almost a doubling in the [share of companies] that lost significant revenue, and that reflects something that we're seeing across the board — both from financially motivated ransomware attackers, nation-states, or hacktivists — they are just trying to disrupt things," he says, adding, "Organizations need to think a lot more about incident response, about containing attacks, about trying to make sure that they actually stay in business if there's an attack."
The survey also found that paying a ransom rarely solves the problem of lost data nor ends the targeting by attackers. Half of all companies (51%) suffered a ransomware attack in 2024, but less than half received a decryption key, and the attacker demanded more money in a third of cases. In the end, only 13% of companies eventually recovered all of their data, according the Ponemon Institute report.
Plan for Alternate Operations for Business Continuity
Early detection and a plan to continue operations in the face of disruption matter most when it comes to minimizing the impact of a cyberattack. Of the companies that did not pay a ransom, nearly half had backups from which they could recover data, while a similar number deemed the data not important enough to pay the ransom.
In the best case scenario, companies can quickly move to cloud operations — or another plan for business continuity — giving them the best chance of recovering without drastic impacts, Rapid7's Beek says.
"We saw one company flip the switch, and suddenly the whole business was running on cloud resources while they were restoring the day-to-day operations," he says. "So the ransomware incident hardly impacted the business."
Companies that have a lack of visibility into — and a lack of security controls protecting — their networks face the most damaging disruption, says Illumio's Dearing.
"Things that allow lateral movement within organizations — like unpatched systems and weak passwords and open RDP ports — help attackers," he says. "So there's an amount of basics that companies need to take."
About the Author
You May Also Like
Shifting Left: DevSecOps in the Cloud
Feb 4, 2025Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025




