The Evolution of Business Email CompromiseThe Evolution of Business Email Compromise
The simplicity and profitability of these attacks continue to appeal to threat actors a decade later.

In 2012, the US Federal Bureau of Investigation (FBI) began investigating an influx of reported fraud incidents involving threat actors rerouting payments to attacker-controlled accounts. In these incidents, victims received seemingly legitimate emails containing requests to alter scheduled payments. The threat actors typically impersonated executives or finance and payroll personnel and convinced victims to reroute payments to a different bank account. These first instances of business email compromise (BEC) kicked off a decade of attacks that use this simple yet highly effective scheme. While the threat has evolved, threat actors continue to use phishing attacks to steal credentials and then send fraudulent invoices soliciting payment. Thousands of organizations have lost billions of dollars.
What Have We Learned in the Past Decade?
When BEC was first discovered, law enforcement referred to it as "man in the email" fraud. Because much of the money at the time was sent to China, Japan, and South Korea, law enforcement believed that the threat actors could be Asia-based organized crime groups. Multiple investigations confirmed that these schemes were connected and that the money eventually ended up with threat actors located in Nigeria.
BEC fraud emerged from Nigerian organized crime groups that conducted operations such as romance scams, advance-fee schemes (also known as "Nigerian prince" or "419" scams), and elder fraud. The low barrier to entry and potential for high payouts attracted more threat groups. Because the technical aspects of these schemes are relatively simple, threat actors with little to no technical capabilities could launch successful attacks.
By 2014, cooperation between law enforcement and financial institutions revealed a clearer understanding of BEC schemes. As BEC tactics, techniques, and procedures (TTPs) matured, the financial losses and number of impacted organizations increased. In 2014, the US Internet Crime Complaint Center (IC3) received 2,417 BEC complaints, with losses totaling $226 million. The numbers grew steadily until a decrease in reported incidents in 2020. However, that decline was likely due to the COVID-19 pandemic disrupting normal business processes. Momentum resumed in 2021, with 19,954 complaints and adjusted losses of almost $2.4 billion.
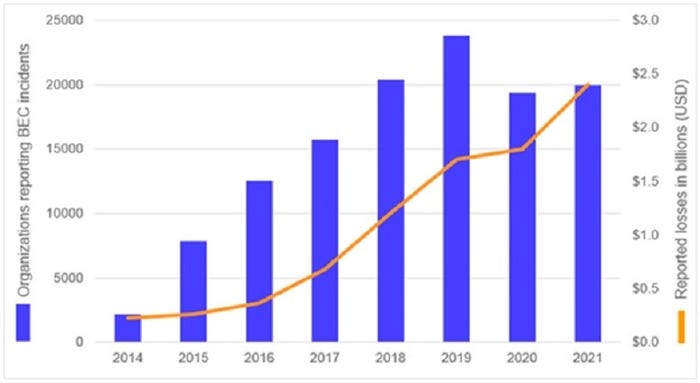
Number of organizations reporting BEC incidents and reported losses between 2014 and 2021. Source: Secureworks, based on data from the Internet Crime Complaint Center (IC3).
Who Is Connducting BEC Attacks?
To this day, the vast majority of BEC operations still originate in Nigeria. Many Nigerian fraud groups incorporated BEC into their existing criminal activities and taught other threat actors how to operate the schemes. Each group determined its own targeting, focusing on specific geographic regions, organizational roles (e.g., CFO, finance manager, accountant), and industries. In 2016, Secureworks researchers estimated that the GOLD SKYLINE threat group (also known as Wire-Wire Group 1) stole approximately $3 million per year. By 2018, Secureworks research indicated that the GOLD GALLEON threat group attempted to steal an average of $6.7 million per year.
Due to the profitability of these schemes, cybercriminals in other regions began adopting BEC. Eastern European groups have shown particular sophistication. For example, Russian cybercrime group Cosmic Lynx has successfully targeted senior-level executives at multinational corporations using a dual impersonation scheme. The threat actors impersonate a company's CEO and then assume the identity of a legitimate attorney who is responsible for facilitating an acquisition. They prompt victims to send money to attacker-controlled accounts.
Despite the expansion of BEC attacks to other regions, none match the volume from Nigeria. The Nigerian fraud ecosystem has grown and flourished over the past decade. Hundreds of social media profiles flaunt wealth obtained from these attacks to recruit participants in Nigeria, where the average monthly salary is less than $800.
Why Is BEC Still Prevalent?
Despite thousands of BEC arrests, the schemes are still popular among cybercriminals. Business-to-business payments are the most frequent targets, but BEC actors also attack other payment methods. Payroll systems have been manipulated to add fictitious employees and send money to the associated accounts. BEC actors have also attacked real estate transactions and rerouted house payments.
While security controls can detect the compromise of an email account, technology can only go so far. As the threat actor continues to use the victim's account or pivots to attacker-controlled infrastructure, detection becomes more challenging. Organizations should implement technical proactive security defenses such as multifactor authentication and conditional access, along with human processes such as verifying requests via trusted contact details before performing high-risk actions and training employees to adopt a "trust but verify" approach to email.
Coordination among financial institutions, government agencies, private industry, and law enforcement across the globe has started to mitigate the impact of BEC attacks. In 2021, the IC3 Recovery Asset Team helped financial institutions recover approximately 74% of the stolen funds it pursued. Reducing the profitability of these attacks could lessen the appeal for threat actors and result in a decrease of BEC fraud.
About the Author
You May Also Like


_marcos_alvarado_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)

