Ransomware's Favorite Target: Critical Infrastructure and Its Industrial Control Systems
The health, manufacturing, and energy sectors are the most vulnerable to ransomware.

National defense and security experts long predicted that future warfare would not be waged by firearms but with code designed to disable services people depend on for daily life.
In May 2021, security experts' worst fears came true, when a ransomware attack struck the Colonial Pipeline. Gas delivery to most of the US Northeast halted almost overnight. Although systems were eventually restored, the event still lives in infamy today and reminds us of the destructive potential cyberattacks can have when levied against critical infrastructure. Since then, similar infrastructure attacks have dominated headlines across most of the world and are increasingly carried out by non-state-sponsored actors.
In our "Q2/Q3 Ransomware Index Update," Securin (formerly Cyber Security Works) researchers mapped out the impact of ransomware on industrial control systems (ICS) deployed in critical infrastructure establishments. They identified the three most at-risk sectors: healthcare, energy, and manufacturing. Our researchers also examined 16 ransomware vulnerabilities and the bad actors who exploit them, such as Ryuk, Conti, WannaCry, and Petya. We have included a table at the end of the article with the full list of vulnerabilities and impacted vendors.
With each successful attack, ransomware groups grow bolder and target industries that can cause the most pain to exploit the crises for maximum extortion. Understanding the threat actors and their methods is the key to protecting critical industries and maintaining smooth operations.
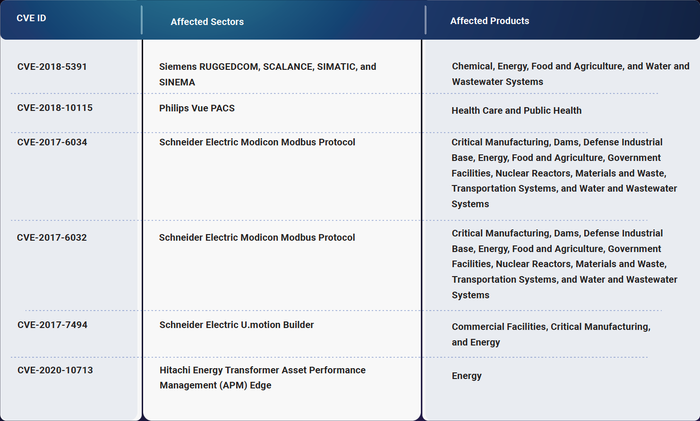
Ransomware CVEs affecting ICS products yet to be included in the CISA KEVs (as on date of publishing the report).
Healthcare
Cybersecurity and Infrastructure Security Agency (CISA) advisories to healthcare providers come in the aftermath of ongoing attacks by ransomware groups such as Black Basta, Quantum, and MountLocker. The impact of unpatched critical vulnerabilities in this sector could be potentially life threatening.
Public health and healthcare systems are affected by the majority of vulnerabilities — nine out of the 16 identified — because they are dependent on other sectors for the continuity of their service delivery and operations. Philips Healthcare, a technology-based company that develops advanced visualization software for crucial imaging equipment, is the most affected vendor, clocking in eight vulnerabilities found in its IntelliSpace Portal 9.0. Vulnerabilities CVE-2017-0144 and CVE-2017-0147 should be patched immediately for their high ransomware family associations used in real-world attacks.
Energy
An attack on an energy provider can result in grid failure or inconsistent energy output to homes, commercial buildings, or other critical service providers. The energy sector is plagued by six vulnerabilities that organizations must watch, particularly those found in Schneider Electric's products.
CVE-2017-6032 and CVE-2017-6034 affect Schneider Electric's Modicon Modbus Protocol, an open communications standard that is used across critical infrastructure, which can lead to chain reaction attacks. However, vulnerabilities CVE-2019-18935 and CVE-2020-10713 found in Hitachi ABB Power Grid systems and Hitachi Energy Transformer Asset Performance Management (APM) Edge, respectively, pose just as much risk. They should be treated as serious by network security administrators.
Manufacturing
The critical manufacturing sector can be divided into four core subindustries: transportation equipment; machinery manufacturing; electrical equipment, appliance and component manufacturing; and primary metals manufacturing.
A quarter of the vulnerabilities included in our analysis affect vendors in the manufacturing sector, including Exacq Technologies, Sensormatic Electronics, and Schneider Electric.
How to Stay Protected
We encourage organizations to stay aware of vendor advisories of the products they utilize and take steps to organize vulnerability enumeration according to severity. Most of the vulnerabilities in this article take advantage of legacy setups comprising out-of-date software and, sometimes, unsupported end-of-life components. Here are key insights to keep your system and industry safe:
Improper input validation is the most prevalent weakness powering ICS ransomware CVEs. Proper input screening can prevent bad actors from infiltrating databases and locking admins out of the system.
Six vulnerabilities are missing from the CISA Known Exploited Vulnerability (KEV) catalog and should be patched: CVE-2018-5391, CVE-2018-10115, CVE-2017-6034, CVE-2017-6032, CVE-2017-7494, and CVE-2020-10713.
Performing simulated penetration tests of your systems can identify hidden entry points that criminals would otherwise use. Finding where you are most exposed can help set patch priorities and build defenses before attackers can leverage them.
The US economy depends on an interconnected infrastructure of energy, health, and manufacturing. Hospitals need the energy to function and render life-saving services, and oil and natural gas refineries deliver necessary fuel to power domestic manufacturing — it's a marvelous system to appreciate, but a rather precious one as well, and we should take steps to protect it.
CVE ID | Impacted Vendors | CVSS v3 Score | Action |
|---|---|---|---|
CVE-2021-44228 | Exacq Technologies, a subsidiary of Johnson Controls, Inc.; Sensormatic Electronics, LLC, a subsidiary of Johnson Controls Inc. | 10 | |
CVE-2020-10713 | Hitachi Energy | 8.2 | |
CVE-2019-18935 | Hitachi ABB Power Grids | 9.8 | |
CVE-2019-0708 | Spacelabs | 9.8 | |
CVE-2018-5391 | Siemens | 7.5 | |
CVE-2018-10115 | Philips | 7.8 | |
CVE-2017-7494 | Schneider Electric | 9.8 | |
CVE-2017-6034 | Schneider Electric | 9.8 | |
CVE-2017-6032 | Schneider Electric | 5.3 | |
CVE-2017-0199 | Philips | 7.8 | |
CVE-2017-0148 | Philips | 8.1 | |
CVE-2017-0147 | Philips | 5.9 | |
CVE-2017-0146 | Philips | 8.1 | |
CVE-2017-0145 | Philips | 8.1 | |
CVE-2017-0144 | Philips | 8.1 | |
CVE-2017-0143 | Baxter, Philips | 8.1 |
About the Author
You May Also Like




