Enemy At The Loading Dock: Defending Your Enterprise From Threats In The Supply Chain
The suppliers, contractors, and other outside parties with which you do business can create a serious security risk. Here's how to keep this threat in check


In mid-May, Lockheed Martin notified law enforcement and government authorities that one of its systems had been breached. The defense contractor later confirmed that attackers used information stolen from RSA, Lockheed's security technology provider, to gain access to Lockheed's system.
RSA wasn't the only third party involved. The attackers first compromised the systems of an unnamed contractor with which Lockheed works and that had access to Lockheed systems, according to The New York Times. Then they used information obtained from the RSA breach--data on RSA's SecurID one-time password technology--to enter Lockheed's network via the compromised contractor's systems.
Like Lockheed, which declined to comment on the RSA incident, many businesses are tying themselves closer together with contractors, partners, cloud service providers, and other third parties, giving attackers new entry points to those businesses' networks and data. Attackers aren't just on the prowl for vulnerable servers; they're also hunting for vulnerable contractors and suppliers. And their victims often know little about the security arrangements of those suppliers.
If you think the Lockheed incident is an exception, consider the case of email marketing firm Epsilon, which in March revealed a breach involving the data of more than 100 major companies, including Citibank, JPMorgan Chase, Kraft, supermarket chain Kroger, Marriott International, and Visa. Those companies ended up having to warn their customers that their names and email addresses might be compromised.
"What happened at Epsilon is an issue where having your data in somebody else's network or freely available to another network can have all sorts of dire consequences, if they don't play to a reasonably high level of skill," says Mike Lloyd, chief scientist from security analysis firm RedSeal.
Know Your Suppliers
Security threats posed by suppliers are more difficult to deal with and prevent, in part because suppliers aren't easy to identify. Suppliers today don't just provide raw materials and products--they include outsourcers and technology service providers. Some suppliers provide cloud services that let companies store data outside their network firewalls. Others provide deliverables, such as software programs and technology. A number of suppliers provide expertise for specific projects and have internal access to systems.
There are three categories of supplier threats. First are dangers from compromised products in the supply chain, such as software that contains back-door access and compromised point-of-sale terminals. Second are risks introduced when insecure suppliers access a customer's network and data; they can bring malware and compromised hardware into your network. A third risk is when customers export sensitive data into cloud providers' systems, in which case security hinges on the providers' practices and policies. Moreover, cloud providers could increase the threat to companies' data because a single service provider--such as Epsilon--ends up storing a great deal of its customers' data.
Don't Let Thieves In Through Your Web Apps Become an InformationWeek Analytics subscriber and get our full report on protecting against SQL injection, free for a limited time.
Become an InformationWeek Analytics subscriber and get our full report on protecting against SQL injection, free for a limited time.
What you'll find:
The methods attackers use to take advantages of SQL injection vulnerabilities
Secure coding techniques that eliminate vulnerabilities
Top 25 most dangerous software errors
The Ease Of Outsourcing
While big companies, such as auto manufacturers and global consumer products companies, have always had a large number of suppliers, the Internet makes it possible for even small companies to outsource a range of infrastructure and business services. More outsourcing means more companies are vulnerable to weaknesses in their supply chain's security, says John Dasher, senior director of data protection product marketing for security vendor McAfee. Those partners' security policies may not be as stringent as their clients'. "But just because you have a certain view on security doesn't mean that you have the muscle to dictate that your partners have the same policies," Dasher says.
Driven by project demands, companies often grant suppliers and partners access to their networks without fully analyzing the security impact and ensuring that third parties have proper authentication and authorization. Says RedSeal's Lloyd, "It's been about: I need to connect to this business partner, then that business partner, then that business partner, and then all the sudden, your great castle of defenses has a whole wall missing, because you have this wide path out to all these extranet partners."
3 Supplier Security Gaps
1. Suppliers and contractors can inadvertently or maliciously bring malware or compromised hardware into a network 2. Compromised supply chain products, such as counterfeit hardware, can end up in finished goods, including military planes 3. A breach at a cloud service provider can result in stolen or exposed data
The extranet edge, where you connect to business partners, has become a particular pain point, Lloyd says. "There's been so much growth, so much change there," he says, and companies are "under intense business pressure to try and get as open as possible."
The Long Way Around
Recent attacks suggest that suppliers are likely to be used by nation states as routes into otherwise well-defended corporate and government targets. Suppliers are likely to have less-secure networks than government agencies and large government contractors.
That was the case with the Stuxnet worm aimed at the Iranian nuclear processing facility. A Symantec analysis of 3,280 samples of the Stuxnet program found that more than 12,000 infections were tied to less than a dozen infections at five companies, each with a presence in Iran. In short, the Stuxnet attackers couldn't get direct access to Iran's nuclear processing facility, so they targeted the facility's suppliers. "There are always going to be ways in," RedSeal's Lloyd says. "Stuxnet is a very good example of how the interrelated nature of the supplier and client can impact security."
While such anecdotes underscore the dangers of supply-side attacks, it remains hard to find a trend in research data.
Verizon's Data Breach Investigations report documents only three breaches out of 761 that involved partners, a significant decrease from last decade, when suppliers accounted for 40% or more of breached records. Yet other data in the report suggests that partners contributed in significant ways to 22% of the breaches. The report describes these contributions as "conditional events"--such as failing to change the default password on point-of-sale terminals and misconfiguring a server--that could be addressed by corporate policies. In addition, the report says a "good number" of assets stolen across all the breach data it examined were managed by partners.
Furthermore, even if the number of supply-side attacks was down last year, 2011 doesn't appear to be continuing that trend. "This year, there seem to be more breaches that can be tied to someone in the supply chain," says Alex Hutton, principal of research and intelligence at Verizon Business. The RSA breach on its own may make for a significant number of supply-side breaches this year.
RSA's SecurID one-time password technology, the technology stolen by attackers earlier this year, affects nearly 40 million SecurID tokens. A number of corporate customers, reported to include Northrop Grumman and L3 Communications, have subsequently warned that attackers have attempted to use the SecurID information to bypass their security. (For more on the data on breaches, see the sidebar: Supplier Attacks Underreported)
What follows are steps companies can take to shore up the security in their supply chains.
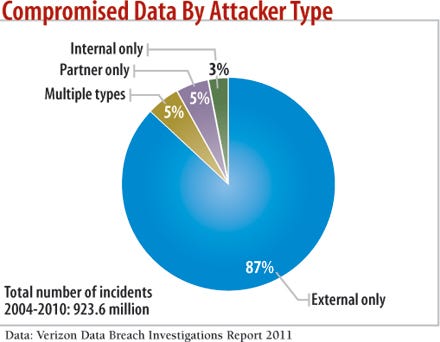
chart: Compromised data by Attacker type
1) Document Vendors And Their Policies
The first step is to create a program under which you ask the right questions of suppliers and make sure they get answered, says Verizon Business' Hutton. "You want to get an idea of the situation of their security department," he says. "Anything from what sort of log management do they do to whether they have earthquake sensors in their data centers."
Once you understand your supplier's security procedures and policies, your IT staff can gauge what sort of impact a breach could have. However, understanding the differences isn't always enough.
"The challenge that many organizations face is they're unable to extend the reach of many of their policies toward business partners or contractors, because those staff are beholden to a different set of policies and standards," says Joji Montelibano, a lead researcher for the Insider Threat Lab at CERT.
Before giving a supplier business or data, don't hesitate to ask for an audit of its security practices and ask for changes. Many suppliers have started compliance programs to offer customers reasonable assurances of their security posture.
Still, with many suppliers, getting policy and contract changes is difficult. The situation gets even more complicated if your suppliers have their own suppliers that also may have security vulnerabilities.
5 Questions To Ask Suppliers
1. What processes and technology do you have in place to detect security breaches and rogue employees? 2. Do you regularly validate your security measures and can you demonstrate your compliance? 3. What contractual obligation do you have to protect my company's data? 4. What's the minimum amount of access to my network and data that you need to do your job? 5. For cloud service providers, what measures can my company take, such as encryption, to protect my data?
2) Minimize Access And Permissions
Companies need to implement role-based authentication technology, which gives suppliers access only to the capabilities and data they need. "You have to treat them as outsiders," says Johannes Ullrich, director of the SANS Institute's Internet Storm Center.
The Payment Card Industry's Data Security Standard is a good starting point, says RedSeal's Lloyd. PCI-DSS requires card data to be stored in a protected digital vault, a system that can be applied to other types of confidential data as well, he says. A network segment or a demilitarized zone can be put inside the vault to limit the contractor's access to the company data.
Creating areas of the network for specific suppliers and using authentication to limit their access is key, says Ken Ammon, chief strategy officer of Xceedium, a maker of identity and access systems. "Binding the identity of the user that's coming in from the partner network with the role they have in your network is very important," he says.
Such limitations can prevent a supplier from easily using its access to one system to compromise other parts of a customer's network. That happened in one case where an auditor came into a client's network with an infected laptop, compromising the network, says Nick Arvanitis, a consultant with Dimension Data America. "They were burnt pretty badly, because they had a flat network at the time, so the infection spread like wildfire," he says.
Dimension Data tracked the infection to the auditor, but the client didn't have a contract that would let it pursue damages--an expensive lesson.
Companies shouldn't use technology just to protect their data; they should also use it to validate that security is configured properly, RedSeal's Lloyd says. One RedSeal client granted a Chinese supplier access to a specific system but misconfigured its firewall, giving the supplier access to the entire network. "They made a classic error, and when they were trying to configure their edge router, they let anything in," Lloyd says. "Their entire infrastructure was completely open if the attack came from this one outsourcer." RedSeal, whose products model and analyze a network's security, finds on average 10 policy violations per network device at its clients.
Technology can provision and deprovision suppliers for specific projects, but that supplier access needs to have an expiration date. "We are all really good about raising our hands and saying, 'Hey, we have a new project. Can you give us access to SharePoint?' But the converse isn't true," McAfee's Dasher says. "We don't ask for less access when the project is done."
Companies must manage the physical access of their suppliers as well. "Letting people wander about freely isn't a good idea," Dasher says.
3) Trust Nothing And No One
Companies typically don't trust devices beyond their firewalls. Neither should they trust any device inside their firewalls.
Inadvertent compromises frequently occur when a contractor or supplier brings in an infected laptop. "The security boundary is becoming weaker and weaker," says Xceedium's Ammon. "And there are so many weak links that you're only as secure as the least secure partner you have."
Companies differ on what they'll allow. Some let partners use their own devices but put them on an external DMZ or extranet. Others won't let suppliers bring in any hardware, instead provisioning them with a machine that has very limited access.
Many clients won't let security consultant Arvanitis plug in a USB stick to copy data or upload anything. Regulated industries and government contractors are the most stringent, he says. Lockheed Martin, for instance, continuously monitors its network for unusual or unauthorized activity--that's how it caught the intruder on its network, a company spokesman says. "If unusual activity is identified, we use a disciplined process to track the adversary, understand their motivation, and secure our customer, program, and employee personal data," he says.
4) Protect The Data
Finally, companies should focus on what's most important to them: the data. But that's become more difficult as more data is exported to the cloud, mobile devices proliferate, and USB drives are so easy to sneak into just about anywhere.
Companies need to come to terms with the fact that suppliers, like employees, are bringing mobile devices inside the firewall and accessing corporate data from just about anywhere. Given this reality, the focus must be on protecting data from insecure and malicious insiders, including suppliers with inside access.
"Your people have become the perimeter. Wherever they are, they're the perimeter," says McAfee's Dasher. "The result is that new views of data protection have come into being over the past five or six years."
Today's data loss prevention products aren't likely to stop technically adept attackers bent on doing harm. So companies should look to employ encryption more extensively, even on data put into the cloud.CipherCloud, for instance, sells encryption for data in software-as-a-service environments.
Without proper access to their customers' systems, suppliers may not be able to do their jobs; with too much access, they're a security risk. There's no easy solution--"buy this product, check the box, and all your problems go away," Dasher says.
Take a multipronged approach to supply chain security, including policies, technology, and education.
Sidebar: Supplier Attacks Underreported
The dangers posed by compromised contractors and other suppliers aren't well documented across all industries. Studies like the Verizon Data Breach Investigations Report are typically skewed toward the retail and financial sectors, because they must report breaches that involve consumer data. Other industries aren't required to report incidences and often don't.
Attacks by insiders and suppliers are notoriously underreported. More than 75% of all insider attacks, which include contractors with insider access, weren't reported, according to the 2011 CyberSecurity Watch Survey, conducted by CSO Magazine, Deloitte, the Software Engineering Institute's CERT program at Carnegie Mellon University, and the U.S. Secret Service. The most common reasons survey respondents say they decided not to prosecute: Provable damages didn't meet the threshold required for law enforcement action, there wasn't enough evidence, and they feared damage to their company's reputation.
More than half of the companies surveyed say their biggest supply chain security concern is with vendors; their second biggest concern is with contractors.
The threat from the supply chain isn't new. "We have seen this problem from day one," says Joji Montelibano, a lead researcher for the Insider Threat Lab at CERT. "It has always been there, and it's always been big."
In one case documented by CERT, a power company contractor was dissatisfied with his employer. The employer revoked his credentials but didn't notify the power company. The contractor used his credentials with the power company to shut down its systems in retaliation against his former employer, Montelibano says. --Robert Lemos
About the Author
You May Also Like




