How To Protect Your Commercial Web Server
Public Internet servers are among criminals’ favorite targets. Is your security strategy up to the challenge?
August 20, 2012

In February, a hacker placed a malicious program on shoe and clothing retailer Opening Ceremony's website. For more than a month, the malware collected the names, addresses, and credit card information of customers who purchased items from the site.
"We discovered the malware on March 21, 2012, immediately removed it, and implemented increased security controls to prevent this from happening in the future," Carol Lim, CEO and co-founder, wrote in a letter to customers in May.
The company offered scant details of the attacks, however, and failed to respond to our request for comment. In her letter, Lim told customers that Opening Ceremony had removed the program and hired breach-response and identity-protection firm ID Experts but only offered a terse statement, promising: "We take the privacy and security of your information very seriously and sincerely apologize for any inconvenience this may cause you."
Online retailers must do better. Criminals and hackers have taken aim at e-commerce sites, targeting them with attacks ranging from extortion attempts threatening denial-of-service attacks to the theft of credit card information to hacktivism.
For an online business, such attacks are a real problem. Many online shops aren't able to afford the basics of security. Even baseline security measures can be so expensive and cumbersome that spending on them can cut into already slim retail profits, says Joshua Corman, director of security intelligence for content-distribution network Akamai Technologies. "Even though they know what the basics are," Corman says, "they can't afford them and so they are living below the security poverty line."
For retailers facing this conundrum, here are some ways to improve security while keeping costs down.
Keep your security effort simple. Companies make different choices for how to operate their e-commerce sites. Amazon can afford to pour a foundation, build a data center, develop its own online retail site, and secure it. Most other companies do much less, using at the very least a hosting provider for their servers, if not their entire e-commerce platform.
Companies face the same range of choices for security and must craft a program that works for their business. An online shop that depends on technical features to attract customers should teach its developers secure programming. A retailer that's focusing less on features and more on its products would likely want to use an e-commerce service since adding whiz-bang widgets to its site is less important.
Focus on technologies that you can not only manage but also secure, says Bill Pennington, chief strategy officer at WhiteHat Security, a Web application security firm. E-commerce platforms can make security easier essentially by outsourcing it to the provider.
"They aren't necessarily more secure, but they are highly focused," Pennington says. "Their reputation, and thus their business, lives and breathes on their ability to make a secure platform."
Businesses also should tackle the simple problems first, such as securing communications and not leaving administration consoles open to the Internet.
In its Global Security Report, security consultancy Trustwave found that 43% of retailers used insecure protocols and 22% used insecure remote access and administration products. Among other top risks that sites face: using a default or no password, failing to use encryption, and storing information in a poorly secured database.
Plan and practice incident response. From day one, consider what types of attacks may hit your site and develop a "runbook" of scenarios and how to respond to each. Knowing who to contact and having existing relationships can dramatically speed response time to an attack and reduce the overall cost, says Paul Sop, technology evangelist with Prolexic Technologies, provider of distributed denial-of-service protection services.
"Detecting a [DDoS] attack isn't hard," Sop says. "Coming to grips with what exactly the attacker's strategy is--Are they going broad? Are they randomizing? What resources are they going after?--doing that quickly is the biggest factor in reducing downtime."
If you don't have internal expertise, a managed security provider can guide the incident response process. Just don't wait until an attack happens to contact specialists. Instead, make them part of monthly development and change-control meetings to get feedback on the security implications of any site modifications, says Dave Marcus, director of advanced research and threat intelligence at security firm McAfee, a subsidiary of Intel.
"On a per-incident basis, it can be expensive," says Marcus. "But doing it on a regular basis and collecting recommendations and advice can help prevent attacks."
Validate third-party security. Most companies deal with third-party providers. Using a service provider--whether for marketing, an e-commerce infrastructure, or payment processing--means relying on that company's security as well.
To protect your company, make sure your provider's contract spells out how the service should be used, how its software is built, and that you can test the e-commerce site at any time. In addition, go over its development process, and request code audits, or at least reports on the most recent code audit, says WhiteHat's Pennington.
If the third party pushes back vehemently against security testing, you're more likely to end up with a company that has insecure software, Pennington says. If it welcomes an audit, it "by and large, [has] far fewer vulnerabilities," he says.
An audit can also be a good way to start a conversation about security and tighten a partnership, says Wolfgang Kandek, CTO at cloud security firm Qualys. The company, which scans sites for vulnerabilities, frequently fields questions from the third-party providers who own the infrastructure, he says.
"Nobody likes to get audited," Kandek says. "But if you make the results available and are there for discussions, it can help customers become more successful."
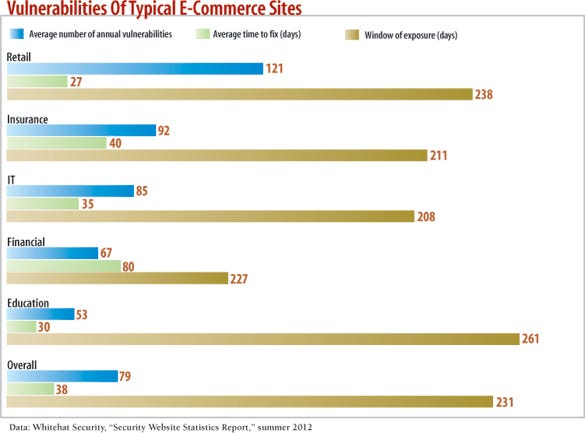
Scan your website often. Increasingly, security-conscious companies are moving toward scanning often to keep up with threats. Moreover, the code driving an e-commerce site can change on a daily basis. Without a good process in place to detect the introduction of new vulnerabilities, online retailers can be in trouble, says Pennington.
But scanning for vulnerabilities can give a false sense of security, because many companies will only do what the regulations demand and use the least-onerous scanning available. Instead, you or your security contractor must think like an attacker, figure out what's valuable that could be attacked, and then attempt to compromise the site or data to see where the vulnerabilities are.
In addition, make sure you know about all the applications through which your site could be attacked. The first step is to scan, or have a provider scan, your external network to identify potential services that could be attacked.
"We have seen in many breaches that a site of minor value was used to get into the main website," Kandek says. "Knowing all your sites is very important."
Adopt secure development methods. If you're developing your own e-commerce site, modifying a third-party application, or otherwise adding code to your websites, you must follow a secure development process. Developers should educate themselves on secure programming techniques with static code-analysis tools to help them catch potentially insecure snippets, says Ryan O'Boyle, a senior researcher with application security firm Veracode.
"Looking for problems after the fact isn't enough," O'Boyle says. "You need to be proactive in developing your applications from the beginning."
Two major classes of vulnerabilities are cross-site scripting and database injection (typically, SQL injection). For companies that don't have large development teams, focusing on a single class of vulnerabilities and eliminating them is an acceptable way of securing software, says Akamai's Corman. Pulling a major class of vulnerabilities from the Open Web Application Security Project Top 10 list and fixing that single risk across all applications may be a better way to get things done, he says.
"Many times, people say 'Fix the OWASP Top 10,'" Corman says. "But screw the Top 10, lets fix the OWASP Top 1. Pick an issue and tackle it."
"Clean" your Web traffic. Web application firewalls, or WAFs, are one way for companies to block known vulnerabilities before they can be used to compromise an e-commerce site. Seventy-one percent of the vulnerabilities WhiteHat Security found in its scans of customer websites could be mitigated by a Web application firewall, according to the company's Website Security Statistics report issued this summer.
Web application firewalls aren't perfect, however. Not only are three out of 10 attacks not stopped by WAFs, but companies often don't have the expertise to use them. Businesses tend to turn on only the most elementary WAF features in order to prevent service disruptions, and many don't tune the devices, says Sop, of Prolexic Technologies.
Attackers are also adopting techniques designed to get around the firewalls, such as overwhelming them with traffic and creating a denial-of-service attack. They may also get around WAFs by making legitimate requests from a large botnet at a low rate, or finding flaws in the way the WAF handles protocols so as to evade the firewall's detections. Ivan Ristic, director of engineering at Qualys, in a recent Black Hat presentation released a catalog of 150 possible ways to get around Web application firewalls.
WAFs are useful, but not a solution, Ristic says. "Users in general should make it clear to the vendors that they care about the quality in WAFs," he says. "I've been involved in WAF development for 10 years, but I'm disappointed by the current state of the market."
Then there are denial-of-service attacks. Extortionists are targeting retailers, threatening to take down their sites unless they pay protection money. In May, small clothing retailer Endless Wardrobe received a threat demanding $3,500 that it refused to pay. Soon, a flood of fake requests overwhelmed the site. The company had to bring in an anti-DDoS service--another way of "cleaning" Web traffic--to stay online.
"If you don't have a DDoS defense of some type and someone launches a DDoS against you, it's almost 100% you'll go down, regardless of what your infrastructure is," Sop says.
Leverage compliance requirements. Most larger e-commerce sites will need to abide by the Payment Card Industry's Data Security Standard. While PCI DSS requirements are a good first step toward security, you can easily check off boxes and do little to actually protect the network.
To comply with the PCI DSS, a company only needs to statically test website code as part of a secure development methodology, dynamically scan its website, or deploy a Web application firewall to block attacks against known vulnerabilities. The standards aren't very clear on the details, so many companies skimp on security, satisfied with meeting paper requirements.
Security teams need to go beyond that, and PCI compliance is a way for them to get money for real security measures. "The organizations that are good at security do budgetary jujitsu with their PCI budget," says Akamai's Corman.
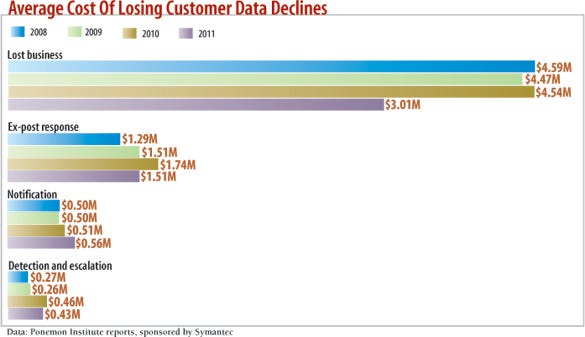
Monitor like crazy. If you want to detect breaches, look to your logs. Collecting and correlating security- and network-event data can help your company detect attacks early. A consistent finding of Verizon's annual Data Breach Investigations Report is that log data is important. The vast majority of breaches are reported by law enforcement, third parties, customers, and partners, but evidence of the attack could have been found in log data in 84% of breaches, according to the 2012 report.
Even if you don't have the technology or expertise to look at the data, you should still collect the information, says McAfee's Marcus.
"There's nothing like too much logging," he says. "At the end of the day, it's just hard drive space."
If you don't know what to log, contact your incident response team, especially if you use consultants. Getting an outside opinion is beneficial, and knowing what data those responders will need is crucial. "If you have the tools in place, and it's already set up, it's less expensive to do when the incident happens," Marcus says. "If, however, all you have is a pile of logs, and you have to pay someone to analyze them, it's going to get expensive."
One important component of website traffic to track is the number of nonhuman visitors. These visitors often are beneficial Web crawlers, but the majority of them are malicious and nonbeneficial (see story, p. 6). They may not be standard hacking attempts but instead could be a competitor looking for price changes on a rival's site.
"Think of the business challenge for your company if you issue a promotion and within minutes, your competitors know," says Marc Gaffan, co-founder and VP of Incapsula.
Reduce scope. If you don't have the security capabilities or the money to secure all your data, getting rid of unnecessary data is an option. In the compliance world, reducing the amount of data that's within scope of standards such as PCI DSS is a well-known strategy.
"The best way to secure data is to not have it," says Akamai's Corman. Getting rid of data can be as easy at outsourcing a business function, like using a payment processor to handle your credit card data, he says.
Encryption is the most obvious way to secure data. Even if stolen, encrypted data isn't considered lost. But there are other methods as well.
Tokenization, replacing sensitive data with a token unrelated to the content, lets a third party, presumably one that focuses on security, hold sensitive data and removes a client retailer from any responsibility for the information. In many cases, payment gateways offer tokenization services.
Turn on additional security. A range of choices of security controls can be activated in the services online retailers use. Online e-commerce services should let your administrators use two-factor authentication, not just an easily hackable user name and password combination.
Payment processors offer additional security controls to help fight credit-card fraud. Merchants that don't detect fraudulent transactions could face a high rate of chargebacks and risk losing their ability to take credit cards, says Matthew Prince, CEO of Web security service CloudFlare.
"It is very difficult for businesses to mitigate the risk by themselves," Prince says. "They need to work with all the people in the payment process to tighten security controls."
Another area where additional security is warranted is the administrative controls for any public-facing sites, along with the back-end database. In Trustwave's Global Security Report, 22% of breaches were caused by insecure remote management systems and, of the attacks where cause was known, 27% were due to an attacker exploiting a SQL-injection vulnerability.
To minimize these sorts of attacks, turn off all potentially insecure features, says Qualys's Kandek. "Databases tend to be managed by a different team, but they still need to minimize the possible opportunity for attack."
Overall, it's possible to secure online retail websites and systems without shaving too much more off the already razor-thin margins. Plan and educate your IT management team, invest in the tools they need, and think like an attacker. All of these approaches will go a long way toward keeping your sites and customers safe.
Sidebar
The Nonhuman threat: Web Bots, Auto Scanners Everywhere
Almost half of all traffic to e-commerce sites is generated by humans--legitimate customers trying to browse and buy products.
The rest is machine generated, and much of it is malicious, or at the very least, not meant to benefit the site. About two in every 10 Web requests are search engines or other good bots crawling the site. But the other 31% are market intelligence firms, hacking tools, website scrapers, and comment spammers, says Web security firm Incapsula.
"The number of nonhuman entities that are crawling your website and the level of sophistication they use has increased significantly," says Marc Gaffan, Incapsula's VP of business development.
Website owners must pay more attention to the traffic hitting their site, say Incapsula and other Web security companies. Automated attackers are targeting website credentials, developer APIs, and product rankings, says Sumit Agarwal, VP of product management at startup Shape Security. Filtering out these noncritical, but still significant, attacks will be increasingly necessary, he says.
"Being able to control your website while being open and accessible is going to be the biggest challenge in the future," Agarwal says.
Just like spammers ramped up the volume of junk email following the widespread adoption of anti-spam technology, malicious attackers and mercenary Web users will likely make their automated software more effective. Recently, Incapsula found that bad bots have impersonated Google's bot traffic nearly 16% of the time as a way to bypass traffic filters put in place by Incapsula and other Web security companies such as Akamai and CloudFlare.
Weeding out the bad traffic can be difficult because Google's page ranking system depends on its bots being treated like humans.
"You dare not block Googlebot because if you do, your search ranking will drop," Gaffan says. "But it takes a deep level of expertise to determine if it is Google, because they don't want you to know if it's them." --Robert Lemos
About the Author
You May Also Like




