M2M Protocols Expose IoT Data, Trend Micro Finds
The MQTT and CoAP protocols that are crucial to IoT and IIoT operations have significant vulnerabilities that puts devices at risk, according to analysis from Trend Micro.

Two of the key machine-to-machine (M2M) protocols that form the underpinnings of the Internet of Things are replete with vulnerabilities, design flaws and implementation issues that can leave enterprises and other organizations open to attacks and data breaches, according to a report by researchers at cybersecurity vendor Trend Micro.
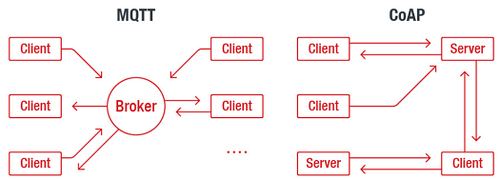
The analysts looked at the Message Queuing Telemetry Transport (MQTT) protocol and Constrained Application Protocol (CoAP), both of which enable the rapidly growing number of intelligent connected devices that make up the IoT and Industrial Internet of Things (IIoT) and are part of expanding operational technology (OT) environments to communicate with each other and quickly exchange data.
Neither of the protocols have security built into them, which exposes massive amounts of data exposed to threats, they wrote in the report, "MQTT and CoAP: Security and Privacy Issues in IoT and IIoT Communication Protocols."

(Source: iStock)
What researchers found was that over a four-month period, more than 200 million MQTT messages and more than 19 million CoAP messages were leaked by vulnerable servers. The risks ranged from hackers remotely controlling IoT endpoints to attackers being able to deny services.
"Hundreds of thousands of MQTT and CoAP hosts combined are reachable via public-facing IP addresses," the researchers wrote. "Overall, this provides attackers with millions of exposed records. Finding exposed endpoints in virtually every country is feasible due to the inherent openness of the protocols and publicly searchable deployments. … Unsecure endpoints, moreover, can expose records and leak information, some of which we found to be related to critical sectors, for any casual attacker to see. Vulnerable endpoints can also run the risk of denial-of-service (DoS) attacks or even be taken advantage of to gain full control."
Exacerbating the issue is that the vulnerabilities are tied to protocols rather than the applications that site on top of them, which in the past have been the target of many cyber attacks.
"This is a big deal," Greg Young, vice president of cybersecurity at Trend Micro, told Security Now in an email. "Individual application vulnerabilities have dominated most security conversation, but as this report details, flaws in the protocol themselves are very uncommon. So even if your application doesn't have flaws, if the protocol does, it is bad news. It is the equivalent of a brand of door lock having a flaw -- even if you lock up your house, a burglar with knowledge of that flaw can defeat the lock without trouble.”
The number of IoT devices worldwide continues to skyrocket, with some industry players predicting more than 50 billion worldwide by 2020. Such numbers significantly expand the threat landscape, which is driving a greater focus on security around IoT. However, not all enterprises are putting enough emphasis on the issue, DigiCert researchers noted in a report released in November. That can cost them a lot of money. According to a survey conducted by the cybersecurity vendor, 25% of companies surveyed said they had lost at least $34 million over the last two years due to IoT security-related issues. (See IoT Security Problems Can Cost Enterprises Millions.)
In the report, the researchers looked at large implementations such as smart cities and smart factories, where M2M communications play key roles.
As the number of such massive environments grow, so do the challenges around managing and securing the data generated by the connected devices. They noted that in one instance they found records for a smart city program that contained email addresses and location names related to taxi or car-sharing rides booked by employees going to or from their offices. The precise timing in the records could show hackers who was going where, they said.
(Source: Trend Micro)\r\n
"Smart cities are a security and privacy 'all your eggs in one basket,' so we really need to watch that basket," Trend Micro's Young said. "With so much technology brushing against smart cities' citizens and their data, protocol and other infrastructure vulnerabilities mean potentially that all digital interactions are more easily attackable and snoopable. A single ride-share event has a considerable amount of private and important data. When that event is then linked to other machine-to-machine (M2M) events such as the wearables of the passengers, the bank accounts they pay for the ride with, etc., the weight of data instantly becomes enormous. … Encryption is helpful for protocol or M2M vulnerabilities, but it isn't the whole solution."
He said the protocol issue is new to most organization, with few sectors -- in auto manufacturers and smart city planners -- aware of the threats.
"Overall the playing field is very unlevel," Young said. "Most IoT, manufacturing and others are new to security, whereas the threats they face have decades of experience. Much of the IT and security experience across the world has been immersed in the web, so non-TCP/IP protocols aren't something they're used to defending. IoT manufacturers with some exceptions are not very interested in security since most buying is all about the lowest price and security is always a cost. Machine-to-machine comms is growing at the same rate as IoT, and so too are the vulnerabilities with it."
Trend Micro is not the first firm to look at MQTT endpoint vulnerabilities. The researchers noted work by IOActive and Avast to expose issues around the protocol. Trend Micro looked at the same problem and added CoAP to its efforts.
Related posts:
Unknown Document 748160
— Jeffrey Burt is a long-time tech journalist whose work has appeared in such publications as eWEEK, The Next Platform and Channelnomics.
Read more about:
Security NowAbout the Author
You May Also Like




