Trigona Ransomware Trolling for 'Poorly Managed' MS-SQL Servers
Vulnerable MS-SQL database servers have external connections and weak account credentials, researchers warn.

The Trigona ransomware threat actors are waging a campaign against Microsoft SQL database servers because many of them have external connections and weak passwords, leaving them open targets for brute force or dictionary attacks.
These vulnerable MS-SQL servers were designated as "poorly managed" by AhnLab Security's new alert about Trigona's nefarious activities.
"If a threat actor manages to log in, control over the system will be passed to them, allowing them to install malware or execute malicious commands," the report said.
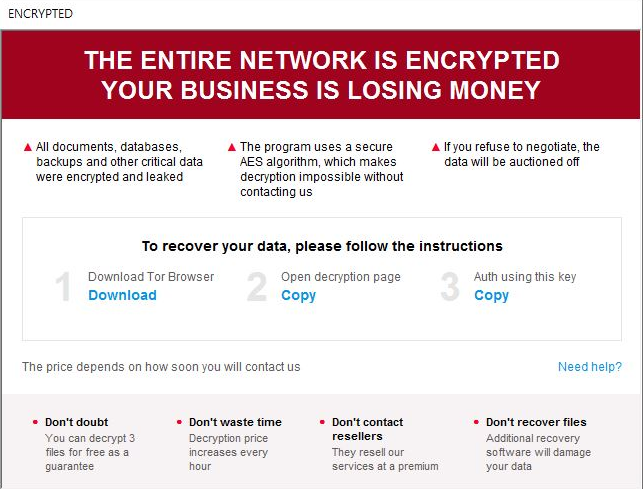
The Trigona ransom note. Source: AhnLabs
They're popular repeat targets too, and not just for Trigona: In one instance observed by AhnLab researchers, credentials for a breached MS-SQL server were compromised by several threat actors, leaving traces of various ransomware strains, Remcos RAT, and coinminers, the report said.Additionally, MS-SQL can be installed on both Windows SQL servers and desktop environments.
"For example, there are cases where MS-SQL is installed alongside certain enterprise resource planning (ERP) and work-purpose solutions during their installation process," the Trigona ransomware report added. "Because of this, Windows servers and Windows desktop environments can both be targeted for MS-SQL server attacks."
AhnLab Security noted Trigona is a relatively new ransomware group, first observed last October.
About the Author
You May Also Like




