How Risk-Based Vulnerability Management Has Made Security EasierHow Risk-Based Vulnerability Management Has Made Security Easier
Trying to remediate everything was never a winning strategy. RBVM is an approach that gets organizations better results with less effort.

For the past five years, the National Vulnerability Database (NVD) has broken its own record of reported vulnerabilities and is on pace to do the same in 2022. With a threat landscape growing that quickly, it's no surprise to see security teams can't keep pace.
According to a report from Cobalt, 79% of security teams struggle to consistently monitor for vulnerabilities amid today's labor shortages, and 54% of security respondents are considering quitting their jobs.
Trying to remediate everything was never a winning strategy. Risk-based vulnerability management (RBVM) is an approach that gets organizations better results with less effort than trying to keep up with the daily average of more than 60 new vulnerabilities so far in 2022.
Five years of data backs this up. The top four metrics used to measure success with RBVM have consistently gotten better, even as a record number of common vulnerabilities and exposures (CVEs) has added more noise to the fray each year.
Let's take a deeper look at those metrics, how they've improved, and why they've improved.
RBVM 101
In its early days, RBVM was taboo because everyone saw vulnerability management as an all-or-nothing proposition. Precious few reached "all" status, and getting there meant a lot of time wasted on remediating vulnerabilities that posed no threat.
"Maturity models" attempt to collect the best cybersecurity practices determined by experts and tweak them over time, but there's an even better way: data. A series of research reports from the Cyentia Institute has provided some answers on what organizations should be prioritizing and informed a better approach to RBVM.
Research produced in conjunction with the Cyentia Institute has shown that 23% of published vulnerabilities have associated exploit code and 2% have observed exploits in the wild. That dramatically reduces the amount of effort required … if you're remediating the right way.
We can judge how organizations are doing by looking at remediation capacity, velocity, coverage, and efficiency. The Cyentia Institute analyzed data from Kenna's platform across the past five years and visualized it in the charts below.
Capacity, the proportion of open vulnerabilities being closed on average every month, has generally increased over the past five years for leading and average organizations. While most organizations are remediating more of their open vulnerabilities, the bottom quarter of organizations has remained steady with no meaningful shifts.
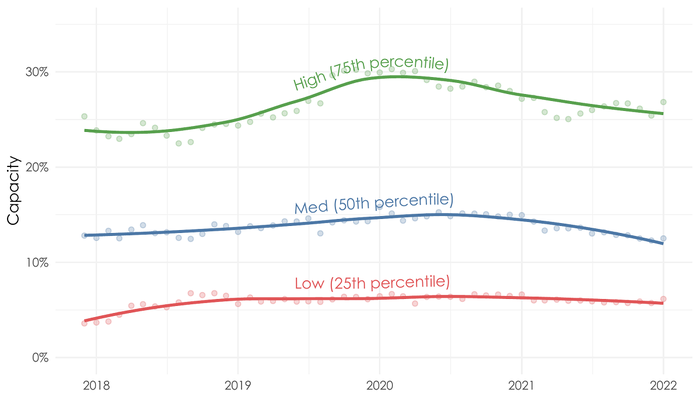
Source: Kenna Security
Remediation velocity saw quick, meaningful progress and has since been improving slowly. Where we are now is a vast advancement over early 2016, when the half-life was more than 125 days. Over the last four years, the half-life — or time it takes to remediate half the newly discovered vulnerabilities — has dropped by more than a third from 32 days to 21 days.
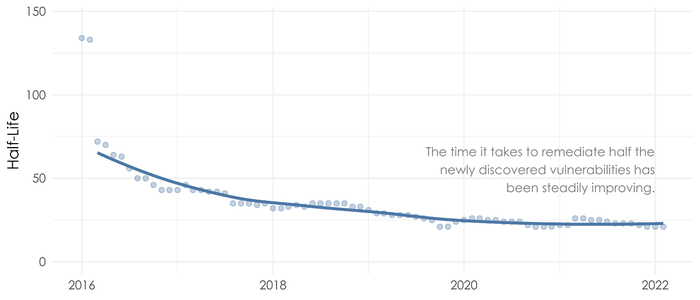
Source: Kenna Security
Efficiency and coverage are related, which is why they're shown together, and without a significant change in prioritization strategy, improving one of those metrics will often lead to a decrease in the other. For example, one way to increase coverage is to simply remediate more, but that makes you less efficient.
Around 2018, both coverage and efficiency were around 35%, but an increase in coverage (more exploited vulns are remediated correctly) causes a decrease in efficiency (fewer of the remediated vulnerabilities are being exploited). This is likely caused by organizations increasing their capacity to remediate more vulnerabilities.
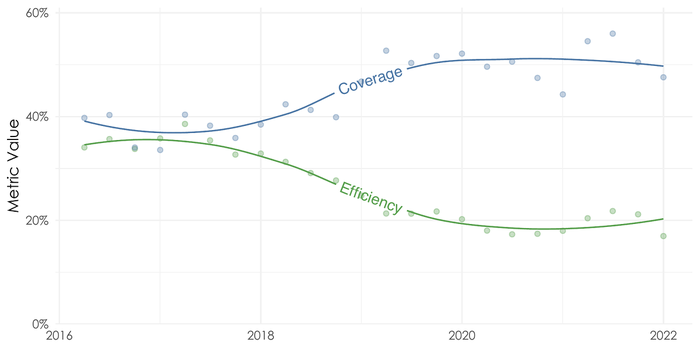
Source: Kenna Security
Keep in mind that this is all happening as we've seen the number of reported vulnerabilities increase each year since 2017. Organizations that have adopted RBVM are filtering out the noise by focusing on risk. They're also remediating more vulnerabilities faster, which is why coverage and efficiency continue to improve.
Explaining the Success
While a more intelligent approach to vulnerability management makes the biggest difference, vendors have gotten smarter, too. Research tells us that Microsoft has more vulnerable assets observed and more exploitation activity than its peers. When the software giant issues patches quickly, it has a heavy impact on remediation velocity (organizations address half their vulnerabilities affecting Microsoft products in roughly 22 days, more than 40 times quicker than SAP or Linux at 900 days).
Between a smarter approach and quick patches from software vendors, vulnerability management is in a far better position than it was five years ago. The proof is in the numbers that organizations have better success when they approach security through a risk lens.
The labor market has further complicated the already complex issue of security, but now organizations know they don't have to fix everything. In fact, it would be silly to and you'll end up driving your valuable security practitioners away. By adopting RBVM, organizations can start to quell the unrelenting pandemonium today's security landscape has become.
About the Author
You May Also Like
Uncovering Threats to Your Mainframe & How to Keep Host Access Secure
Feb 13, 2025Securing the Remote Workforce
Feb 20, 2025Emerging Technologies and Their Impact on CISO Strategies
Feb 25, 2025How CISOs Navigate the Regulatory and Compliance Maze
Feb 26, 2025Where Does Outsourcing Make Sense for Your Organization?
Feb 27, 2025




