The Coronavirus & Cybersecurity: 3 Areas of ExploitationThe Coronavirus & Cybersecurity: 3 Areas of Exploitation
Criminal, political, and strategic factors are combining to create a perfect storm of cyber infections that target the global supply chain.

Times of crisis often create opportunities for those looking for vulnerabilities in their opponents. Today's coronavirus crisis is creating economic and political dislocation, disruption of the commercial status quo, and a breakdown in the fabric of global commerce — not to mention uncertainty and fear.
A rapidly growing number of people are already coming to understand this. But what most still do not know is that hackers are also barging into this grim arena, capitalizing on heightened vulnerability with fresh cyberattacks and the creation of malicious websites.
The US Health and Human Services Department recently suffered a cyberattack related to its coronavirus response. The attack ultimately did not succeed, and no data was accessed, but officials believe the culprit or culprits were likely foreign state actors looking to undermine confidence in and effectiveness of US government institutions.
Other attacks are coming. Already we're seeing malicious infections in the name of Wuhan Coronavirus circulating in the digital world. Specifically, Kaspersky researchers have found that 10 unique files (dubbed as coronavirus-spread) are popping up filled with, among other things, malevolent infections such as file-encrypting and cryptomining malware. Others exfiltrate sensitive data.
Additional factors are combining to create a perfect storm for cyber infections. These include lower staffing levels in enterprise security operations centers (SOCs) as corporations try to virtualize their staffing, placing workers remotely outside enterprise firewalls with only vulnerable single-factor authentication as protection against increased social media access and high interest in COVID-19 news.
3 Targets
Political exploitation: There will be attempted compromises on critical infrastructure, such as power plants and petrochemical facilities, as well as active disinformation campaigns to sow confusion and undermine confidence in political leadership. The DDoS attack on Health and Human Services is just the start. There are also reports of a foreign disinformation campaign warning of a pending "nationwide quarantine," quickly debunked by US government officials, designed to create fear in the US population and undermine confidence in government institutions.
According to research from Prevailion, a cyber intelligence firm focused on nation-state cyberattack schemes, its APEX platform and sensor network shows more than 30 state and local governments have already been unwitting victims of nation-state actors looking to spread dissention and disruption. Among the most affected areas are Texas, New York, Ohio, California, Florida, Washington, DC, Alabama, North Carolina, Louisiana, and Connecticut. The trend has been on a rapid upward trajectory since the COVID-19 outbreak.
Criminal exploitation: Cybercriminals are looking for and exploiting weaknesses. According to Check Point Software's Global Threat Index, coronavirus-themed domain registrations are 50% more likely to be from malicious actors. Whether it is well-honed phishing attacks with labels such as "Corona Virus," "Stock Market Volatility,” “Near Zero Interest Rates,” “Remote Working” news, or ransomware attacks targeting hospitals and critical healthcare providers, the criminals know where vulnerabilities exist and how to exploit them.
As Oren Falkowitz, founder and CEO of anti-phishing company Area 1 Security, wrote me recently in an email: "Since mid-February, we have seen a material increase in the number of phishing campaigns tied to the coronavirus. The reason nine in ten cybersecurity incidents begin with phishing is not technical sophistication or lack of awareness by individual users, but by the overwhelming desire of cyber actors to appear authentic. Whether they use trusted brands, or topical events such as the coronavirus as lures, they are always on the offensive."
Strategic exploitation: While many attacks will be designed to affect the crisis near term, the most sophisticated attackers will take advantage of preoccupied organizations that have their guard down. They will plant malware inside a targeted company's infrastructure for later exploitation.
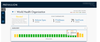
As illustrated in the above graphic, Prevailion is seeing a confirmed influx evidence of compromise in a large Italian vehicle manufacturer with a pattern that matches the reduction of staff and eventual complete shutdown of the facility due to the COVID-19 pandemic. Karim Hijazi, CEO of Prevailion, explained in an email, "The dates of the influx of compromise correlate closely and illustrate the increasing challenge of weaker cybersecurity controls and defenses."
Furthermore, a recent Accenture study shows (page 10, figure 2) that 40% of security breaches are now indirect, as threat actors increasingly target the weak links in the supply chain or business ecosystem. Given what is happening and expected to happen, COVID-19-related security breaches are already alarming officials from the World Health Organization (WHO).
There is no question that the pandemic will continue to amplify cyber threats. Bad actors are experts at exploiting a crisis. But as experience has shown, every crisis and attending threat translates into a learning opportunity. These opportunities are lessons from which we can adapt new strategies and supporting technologies to evolve our digital economy and technology infrastructure to be better prepared the next time we face challenges. In the case of the coronavirus threat, the vulnerabilities of the global supply chain and digital economy are now clear. We are being challenged to rethink the infrastructure by which we manage in this environment. We must be more resilient going forward.
Related Content:
 Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "Untangling Third-Party Risk (and Fourth, and Fifth...)."
Check out The Edge, Dark Reading's new section for features, threat data, and in-depth perspectives. Today's featured story: "Untangling Third-Party Risk (and Fourth, and Fifth...)."
About the Author
You May Also Like


_marcos_alvarado_Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)

