Healthcare's Grim Cyber Prognosis Requires Security BoosterHealthcare's Grim Cyber Prognosis Requires Security Booster
As healthcare organizations struggle against operational issues, two-thirds of the industry suffered ransomware attacks in the past year, and an increasing number are caving to extortion and paying up.
October 8, 2024

The healthcare sector continues to grow, but without the proper focus on cybersecurity, the prognosis for the industry's resilience against ransomware and other attacks has only worsened.
Against a backdrop of non-IT disruptions — such as private equity failures, shortages of medicines, and the cutting of services — two-thirds (66%) of healthcare organizations also suffered ransomware attacks in the past year, up from 60% in the prior year, according to a report from cybersecurity firm Sophos. Major attacks on hospitals and medical-service providers have led to disruptions of services, significant financial outlay, and the exposure of sensitive patient data. In some cases, they also affected patient outcomes.
There are also new threats emerging all the time. The Trinity ransomware, for instance, first seen last May, poses a "significant threat" to the healthcare and public health sector, according to an alert this week from the US Department of Health and Human Services.
Overall, more than 14 million US citizens — and an unknown number worldwide — have been affected by healthcare breaches in 2024, according to another data set from security firm SonicWall.
Healthcare suffers such a cyber malaise that Senate Finance Committee chair Ron Wyden (D-Ore.), and Sen. Mark Warner (D-Va.) last week announced legislation to attempt to patch up the system. The bill would require jail time for healthcare CEOs that lie to the government about their cybersecurity postures, offer federal resources to rural and underserved hospitals for cyber improvements, and introduce accountability measures and mandatory cybersecurity requirements for all organizations that hold sensitive data. The bill would also remove the existing cap on fines for data mishandling under the Health Insurance Portability and Accountability Act (HIPAA).
"Mega-corporations like UnitedHealth are flunking Cybersecurity 101, and American families are suffering as a result," Wyden said in a statement announcing the bill. "The healthcare industry has some of the worst cybersecurity practices in the nation despite its critical importance to Americans’ well-being and privacy."
Healthcare Cyber-Profiles Are Ripe for Infection
Healthcare organizations have three attributes that ensure ransomware gangs will continue to focus on the industry: Their operations are critical to society, their technology is often old and rife with vulnerabilities, and individual organizations are willing to pay ransoms, says Doug McKee, executive director of threat research of SonicWall.
"There's a lot of money in healthcare, [and] healthcare is not only notorious for having a lot of money, but they've been painted as an industry that's willing to pay the ransom," he says. "If we're going to keep paying the ransom, the attackers are going to keep ramping up in that industry. The math is that simple."
The cybersecurity problems plaguing the industry are not just affecting the business of healthcare. They're also having real impacts on patients and national health efforts. Attackers used stolen credentials, for example, to compromise UnitedHealth subsidiary Change Healthcare and infect its systems with ransomware in February, leading to stalled payments for doctors, pharmacies, and hospitals — and eventually a $22 million ransom paid to the criminals. In the United Kingdom, an attack on medical-services provider Synnovis in June led to delays in matching patient blood types and other pathology services. The same month, an attack on South Africa's National Health Laboratory Service (NHLS) disrupted the service provided by the government-run testing laboratories, while the nation found itself in the midst of an mpox outbreak.
"I can either pay the ransom, get back up and running, or I can try to rebuild it myself and pray that we get everything back set up running in a week — not an option," says Errol Weiss, chief information security officer (CISO) of the Healthcare Information Sharing and Analysis Center (Health-ISAC). "So now, we've got a sector who is more prevalent to pay, and I think the bad guys — cybercriminals, nation-states that are doing this — figured that out pretty quickly. I think it's getting worse, and I think that they've also figured out the weak spots in the sector."
A Pound of Cure Typically Fails
The weakest spot for healthcare entities is arguably the inter-reliance of hospitals and pharmacies on their third-party providers. When Change Healthcare suffered its weekslong outage, the incident demonstrated that efforts to shore up cyber resilience has to extend all the way to any third-party suppliers on which healthcare providers rely.
"Change Healthcare definitely rocked the sector and made us [realize] that it's a single point of failure for so many services," Weiss says. "We had thousands of patients across the US that couldn't get prescriptions filled because of that outage, and then ... we had hospitals that couldn't file claims."
Similarly, the attacks on Synnovis and NHLS slowed diagnostic services.
While their operational requirements — prioritizing human life, which means keeping open the access to needed data — pose challenging issues, healthcare organizations must gain oversight over their (often legacy) technology and the large variety of medical devices and equipment, which might not be kept totally up to date. Seven out of every eight breaches were caused by exploitable vulnerabilities, compromised credentials, and malicious emails — so focusing on those three areas could pay significant dividends for cybercriminals, says Christopher Budd, director of threat research for Sophos X-Ops.
"Healthcare — along with energy, oil/gas, and utilities — is challenged by higher levels of legacy technology, and infrastructure controls more than most other sectors, which likely makes it harder to secure devices, limit lateral movement, and prevent attacks from spreading," he says.
Time for an Ounce of Prevention
Yet, perhaps most telling is the industry's problems with backups.
In 95% of attacks targeting healthcare organizations, the attacker tried to compromise the backups. Unfortunately, they succeeded in 66%, putting healthcare organizations' defensive shortcomings behind that of only the energy, oil/gas, and utilities sector (79%) and the education sector (71%), according to Sophos' report.
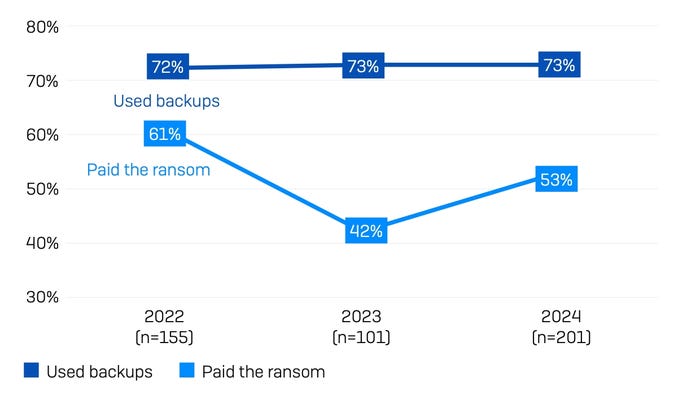
While healthcare organizations continue to use backups to recover, many also pay ransoms. Source: Sophos
The loss of backups results in much worse — and more expensive — outcomes, the report stated. The value of the initial ransom demand more than tripled, to $4.4 million, compared with $1.3 million for organizations with backups, and the organizations were far more likely to pay the ransom, with 63% of organizations with a failed backup paying the ransom, compared with 27% of organizations with complete backups.
In its threat brief, SonicWall recommended the typical trio of cybersecurity best practices: patch management, strong access controls, and continuous monitoring. However, out of those three, monitoring is the most important capability for organizations to establish first, says SonicWall's McKee. Companies with good visibility can detect cybersecurity issues early and remediate them before they are attacked, he says.
While the outlook is currently messy, progress is being made, he added.
"I think that we've gotten better," McKee says. "Over the last five years, I've seen a huge improvement in healthcare, as far as being able to turn around cybersecurity best practices ... but [technology] has to get through all the regulatory requirements ... and that's simply going to take time ... probably years, for healthcare to get to a point that we're able to reduce some of the effectiveness of these attacks."
Read more about:
CISO CornerAbout the Author
You May Also Like




