The Market Is Teeming: Bargains on Dark Web Give Novice Cybercriminals a Quick Start
A study of the unregulated dark markets shows that the vast majority of malware, exploits, and attacker tools sell for less than $10, giving would-be criminals a fast entry point.
July 21, 2022

Would-be cybercriminals can easily buy advanced tools, common exploits, and stolen credentials on underground markets for a few dollars — a low barrier to entry for novices, according to a study of 33,000 Dark Web marketplaces.
According to new analysis from HP Wolf Security and researchers at Forensic Pathways, there are plenty of bargains to be had. Out of the 174 exploits found advertised on the Dark Web, 91% cost less than $10, while 76% of the more than 1,650 advertisements for malware have a similar price.
Other common attacker assets also have similarly low prices: The average cost, for example, for stolen credentials for accessing a Remote Desktop Protocol (RDP) instance is just $5.
While more advanced malware groups use private forums to trade zero-day exploits, the available credentials, exploits, and tools on offer in the wider underground economy allow novices to quickly create a credible toolset, says Alex Holland, senior malware analyst at HP and primary author of the report.
Novice cybercriminals "can use a freely available open source tool, and — as long as you are skilled enough to encrypt, use a packer, use techniques to evade defenses — then that tool will do a perfectly good job," he says.
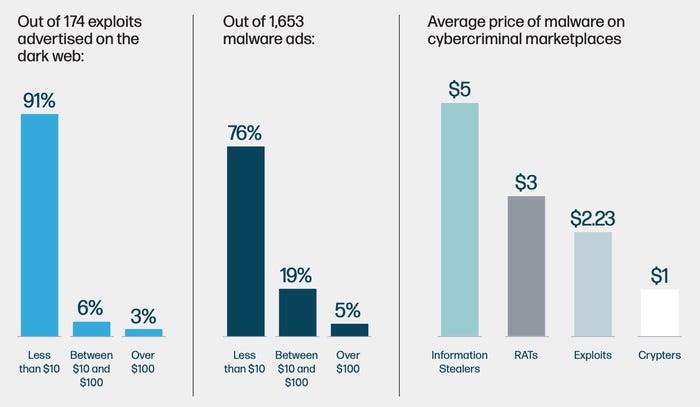
The vast majority of exploits and malware are sold on the Dark Web for less than $10. Source: HP's The Evolution of Cybercrime report.
The study of Dark Web marketplaces analyzed approximately 33,000 active sites, forums, and marketplaces over a two-month period, finding that the market for basic tools and knowledge is well entrenched, and attracting new customers all the time.
The increase in the number of threat actors could mean businesses will find their operations targeted even more than they are today, according to Michael Calce, HP Security Advisory Board member and former hacker (aka MafiaBoy). HP brought in criminologists and former hackers to help put the study in context.
"Today, only a small minority of cybercriminals really code, most are just in it for the money — and the barrier to entry is so low that almost anyone can be a threat actor," Calce says in the report. "That's bad news for businesses."
To protect themselves from the swelling ranks of cyberattackers, HP recommends that companies do the basics, using automation and best practices to reduce their attack surface area. In addition, businesses need to regularly conduct exercises to help plan for and respond to the worst-case attacks, as attackers will increasingly attempt to limit executives choices following an attack to make ransom payments the best worst option.
"If the worst happens and a threat actor breaches your defenses, then you don't want this to be the first time you have initiated an incident response plan," Joanna Burkey, chief information security officer at HP, says in the report. "Ensuring that everyone knows their roles, and that people are familiar with the processes they need to follow, will go a long way to containing the worst of the impact."
Cybercrime Convergence: Nation-State Tactics Blend With Financial Campaigns
The report also found that advanced actors are becoming more professional, using increasingly destructive attacks to scale up the pressure on victims to pay. At the same time, financially motivated cybercriminals groups continue to adopt many of the tactics used by high-end nation-state threat actors.
These especially focus on living-off-the-land attacks where the attacker uses system administration tools to avoid endpoint-detection systems that would otherwise flag malware, according to HP.
While the shift likely comes from the transfer of knowledge as cybercriminals become more skillful and learn the latest tactics used by advanced persistent threats, a number of groups are also blending nation-state activities—such as cyberespionage — and cybercriminal activities aimed at turning a profit. The leak of text messages from the Conti group highlighted that the members occasionally conducted operations at the request of at least two Russian government agencies.
Ransomware Is Here to Stay
Elsewhere in the report, researchers note that ransomware gangs will focus on timing their attacks to put the most pressure on organizations, such as attacking retailers during the holiday seasons, the agriculture sector during harvest seasons, or universities as students return to school.
Ransomware has declined in the first half of the year for various reasons, but HP sees the trend as temporary.
"We don't see ransomware going away, but we do see it evolving over time," Holland says. "Ransomware attacks will actually become more creative."
Enforcing Ethics on the Dark Web
The study also found that trust continues to be a major problem for Dark Web markets in the same way that online businesses have had to deal with fraud and bad actors. The Dark Web, of course, has facets that make trust even harder to come by: A website on the anonymous Tor network, for example, has an average lifespan of 55 days, according to the researchers.
To ensure that vendors and customers play fair, the marketplaces have adopted many of the same strategies as legitimate businesses. Vendors are usually required to offer a bond of thousands of dollars to ensure trust. Customers can leave ratings on every marketplace. And escrow payments have become commonplace, with 85% of transactions using escrow payment systems.
About the Author
You May Also Like




