More Legal Records Stolen in 2023 Than Previous 5 Years Combined
Law firms make the perfect target for extortion, so it's no wonder that ransomware attackers target them and demand multimillion dollar ransoms.
August 1, 2024

2023 was the worst year on record for cybersecurity in the legal industry by some distance.
Just one point of evidence: Since 2018, 2.9 million records have been stolen in association with publicly reported breaches of law firms. Some 1.56 million records were stolen last year alone, an increase of 615% as compared with the down year of 2022 (218,473 records).
A new blog post from Comparitech paints a picture of an industry struggling to grapple with the ransomware problem. Major law firms have been paying multimillion dollar sums to protect their clients' ultra-sensitive data, and flailing in their attempts to fight back.
The State of Legal Industry Cybersecurity
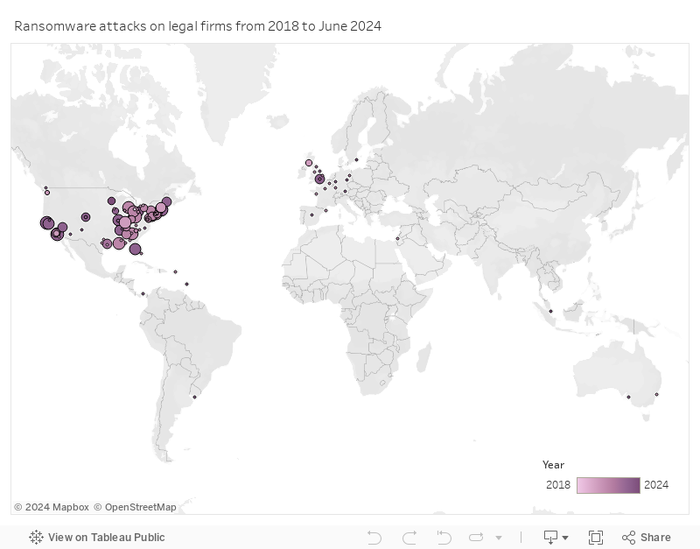
Since 2018, 138 legal firms have publicly admitted being affected by ransomware attacks.
Of those, 107 attacks have been US-based, with approximately 2.9 million records affected. As Comparitech noted, the distance between the US and its next neighbors — the UK, with 9 attacks affecting 9,703 records, and Germany, with 5 affecting an unknown number — may have more to do with reporting requirements than anything else.
Source: Comparitech
Ransom demands vary widely. In 2021, the French law firm Cabinet Remy Le Bonnois paid the Everest group just $30,000 to resolve its attack. At the other end of the spectrum: REvil demanded $21 million from New York's Grubman Shire Meiselas & Sacks in 2020. The attackers doubled that amount to $42 million when the group discovered that Grubman's records included some belonging to Donald Trump. (The firm did not pay.)
The average ransom among publicly reported cases has been $2.47 million, and the average amount actually paid out after negotiations is $1.65 million. These numbers are rough estimates of reality, however, as only 11 reported incidents also reported the ransom demands, with only eight reported ransoms paid.
Consequences to Law Firms
If ransomware attacks against law firms have been trending, it's because they make for perfect targets.
"Legal firms are an interesting case," Paul Bischoff, privacy advocate at Comparitech explains, "because with most any other company, hackers are just looking for low-hanging fruit. They may want as many, say, Social Security numbers or passwords as they can possibly steal. And higher quantities of records is the goal. But with law firms, you have data that's very valuable to very specific people. Documents related to ongoing litigation would be extremely valuable to an opposing party in that case. So it's not so much about the quantity of data as much as it is about the content."
The ultra-sensitivity of legal data puts firms in a difficult negotiating position: pay millions of dollars, and risk achieving nothing, or don't, and risk extra ire from clients. 12% of legal industry ransomware attacks have resulted in lawsuits, and at least 75% of those have been successful.
Another reason to pay up? Comparitech estimates that the 138 attacks recorded might have cost victims around $18.8 billion dollars, purely thanks to the downtime they incurred. One victim of LockBit — the Ince Group, based in London — filed for bankruptcy last year after failing to cover the £5 million ($6.5 million USD) it spent restoring its systems.
Meanwhile, when victims try to use the law in their aid, they usually fail. The UK's Ward Hadaway and Australia's HWL Ebsworth Lawyers both issued injunctions against their attackers to little effect, as anonymous hackers aren't particularly easy to wrangle into court. Canadian firm Robson Carpenter LLP enjoyed seeing its attacker face justice, but in the end received just $2,500 in restitution.
On the bright side, ransomware attacks against law firms in 2024 are noticeably lagging behind last year's numbers. Only 11 have been reported so far, affecting an unknown volume of client data.
"Overall, ransomware attacks happen down in frequency of attacks across all sectors that we've been covering," Bischoff notes. Perhaps, he speculates, attackers have been choosing quality over quantity. Or, more optimistically, "I think it's law enforcement crackdowns, and companies and organizations getting better in general at knowing what these threats are and being prepared."
About the Author
You May Also Like




