Ransomware Attempts Flag as Payments Also Decline
Telecom and business services see the highest level of attacks, but the two most common ransomware families, which continue to be LockBit and Conti, are seen less often.
July 18, 2022

Attempted ransomware attacks declined in the first quarter of 2022, as companies continued to be less likely to pay requested ransoms and the war between Russia and Ukraine disrupted the Eastern European groups responsible for a significant share of attacks, endpoint detection-and-response firm Trellix states in a new report.
Companies continued to encounter the two most common ransomware families — LockBit and Conti — more than a third of the time, but both ransomware attacks are seen far less often, with detections for LockBit dropping by 44% and Conti by 37%, according to Trellix's "Summer 2022 Threat Report." Globally, ransomware targeted the telecom sector in more than half of attacks, but business services dominated the targeting of US organizations, accounting for 64% of detections.
While cybercriminals often avoid politics, the decline likely comes as a result of Russia's invasion of Ukraine, which has led to more geopolitical-related attacks but fewer ransomware campaigns, says Christiaan Beek, lead scientist at Trellix.
"The attacks are shifting," he says. "While we saw some wipers and some other malware, which continued in April and May, they remain fairly low activity, but we are seeing more activity from hacktivism and [patriot] groups."
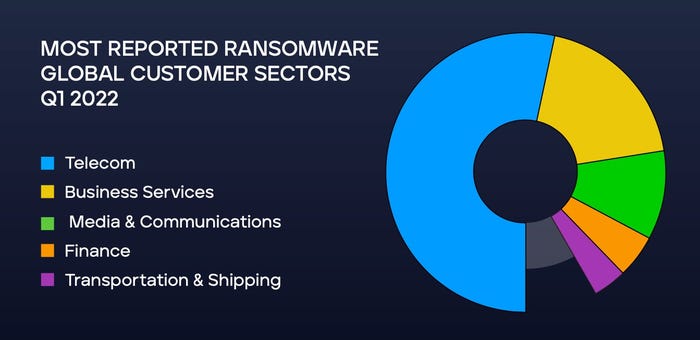
Globally, the telecommunications sector is most targeted by ransomware, but in the US, business services are favored. Source: Trellix's Summer 2022 Threat Report
The report from Trellix's Threat Labs is the first analysis from the company to combine data and telemetry from two acquisitions — McAfee Enterprise and FireEye's product business — bought by Symphony Technology Group in 2021. In January, STG renamed the combined businesses Trellix.
The company also includes references to data from a third party — incident response firm Coveware — that shows only 46% of companies paid a ransom in the first quarter of 2022, down from 85% for the same quarter three years ago. The average victim's payment to ransomware groups also declined to $74,000, down more than a third from the fourth quarter of 2021, Coveware stated in a May blog post.
"This is what progress looks like against ransomware. It is slow," the company stated.
Harder to Compromise Systems
Nation-state activity continues to be a major threat, according to Trellix's report. Following Russia's invasion of Ukraine — two countries that are thought to be home to several ransomware groups — attacks have focused on a goal of data exfiltration while using cybercrime as a way to fund the effort.
In February, for example, the Conti group publicly posted a statement supporting the Russian government. The following month, a Ukrainian researcher leaked years of Conti's internal chats, showing that the group had dozens of coders, operated like a business, and maintained separate sets of tools to hide the actual size of their operations.
"[W]e should consider we might be witnessing the formation of a hybrid group, one that can attack targets chosen by the government, but maintaining the plausible deniability of a crime group after financial gain," Trellix's report states. "The ransomware might have a dual purpose, on the one hand being disruptive in nature and on the other hand serving as a distraction for a data exfiltration operation."
Other major trends include the continued adoption of living-off-the-land (LotL) techniques. While a red-team tool, Cobalt Strike, continues to be the most popular attack tool by far — used in a third (32%) of campaigns — attackers continue to use tools resident on the targeted systems, including Windows Shell, PowerShell, and the Windows Management Interface (WMI), Trellix's report states.
However, attackers do have to work harder to compromise systems, with improving defenses requiring longer attack chains, says Beek. In the past, a victim might click on a link in an email or open an untrusted attachment and have a malicious program installed.
"Now, you see an email with an attachment still, but it has a little script in there that is a URL, for example, and it goes to one website, downloads a little bit of code," Beek says. "There are more stages that are happening before something is definitely being put on the system."
While telecommunications companies and business services are currently the most popular targets of attacks, among the most worrisome trends is the vulnerability of the healthcare industry and the continued ransomware attacks on the organizations that provide medical care, Beek says.
He warns that the trend will likely continue, given the anemic funding for cybersecurity in healthcare.
"This is not just the a ransomware perspective — it's also about the level of vulnerability," he says. "For me, that is a concern. You want to go to a hospital to get treated, and you don't want delays because of ransomware."
About the Author
You May Also Like




