Apache ERP Zero-Day Underscores Dangers of Incomplete Patches
Apache fixed a vulnerability in its OfBiz enterprise resource planning (ERP) framework last month, but attackers and researchers found a way around the patch.
January 4, 2024

Unknown groups have launched probes against a zero-day vulnerability identified in Apache's OfBiz enterprise resource planning (ERP) framework — an increasingly popular strategy of analyzing patches for ways to bypass software fixes.
The 0-day vulnerability (CVE-2023-51467) in Apache OFBiz, disclosed on Dec. 26, allows an attacker to access sensitive information and remotely execute code against applications using the ERP framework, according to an analysis by cybersecurity firm SonicWall. The Apache Software Foundation had originally released a patch for a related issue, CVE-2023-49070, but the fix failed to protect against other variations of the attack.
The incident highlights attackers' strategy of scrutinizing any patches released for high-value vulnerabilities — efforts which often result in finding ways around software fixes, says Douglas McKee, executive director of threat research at SonicWall.
"Once someone's done the hard work of saying, 'Oh, a vulnerability exists here,' now a whole bunch of researchers or threat actors can look at that one narrow spot, and you've kind of opened yourself up to a lot more scrutiny," he says. "You've drawn attention to that area of code, and if your patch isn't rock solid or something was missed, it's more likely to be found because you've extra eyes on it."
SonicWall researcher Hasib Vhora analyzed the Dec. 5 patch and discovered additional ways to exploit the issue, which the company reported to the Apache Software Foundation on Dec. 14.
"We were intrigued by the chosen mitigation when analyzing the patch for CVE-2023-49070 and suspected the real authentication bypass would still be present since the patch simply removed the XML RPC code from the application," Vhora stated in an analysis of the issue. "As a result, we decided to dig into the code to figure out the root cause of the auth-bypass issue."
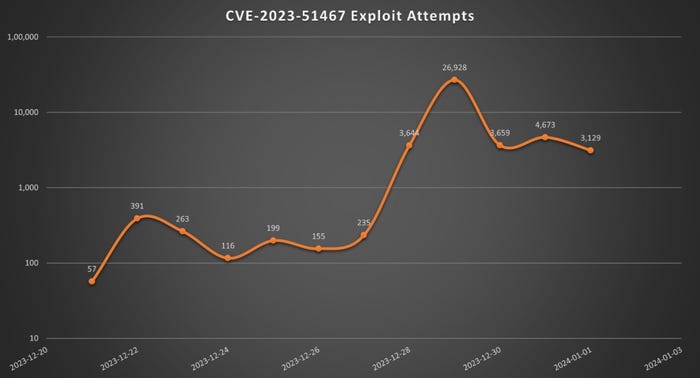
Attacks targeted the Apache OfBiz vulnerability prior to its Dec. 26 disclosure. Source: Sonicwall
By Dec. 21, five days before the issue was made public, SonicWall had already identified exploitation attempts for the issue.
Patch Imperfect
Apache is not alone in releasing a patch that attackers have managed to bypass. In 2020, six out of the 24 vulnerabilities (25%) attacked using zero-day exploits were variations on previously patched security issues, according to data released by Google's Threat Analysis Group (TAG). By 2022, 17 of the 41 vulnerabilities attacked by zero-day exploits (41%) were variants on previously patched issues, Google stated in an updated analysis.
The reasons that companies fail to fully patch an issue are numerous, from not understanding the root cause of the problem to dealing with huge backlogs of software vulnerabilities to prioritizing an immediate patch over a comprehensive fix, says Jared Semrau, a senior manager with Google Mandiant's vulnerability and exploitation group.
"There is no simple, single answer as to why this happens," he says. "There are several factors that can contribute to [an incomplete patch], but [SonicWall researchers] are absolutely right — a lot of times companies are just patching the known attack vector."
Google expects that the share of zero-day exploits that target incompletely patched vulnerabilities to remain a significant factor. From the attacker perspective, finding vulnerabilities in an application is difficult because researchers and threat actors have to look through 100,000s or millions of lines of code. By focusing on promising vulnerabilities that may not have been properly patched, attackers can continue to attack a known weak point rather than start from scratch.
A Way Around OfBiz Fix
In many ways, that's what happened with the Apache OfBiz vulnerability. The original report described two problems: an RCE flaw that required access to the XML-RPC interface (CVE-2023-49070) and an authentication bypass problem that provided untrusted attackers with this access. The Apache Software Foundation believed that removing the XML-RPC endpoint would prevent both issues from being exploited, the ASF security response team said a response to questions from Dark Reading.
"Unfortunately we missed that the same authentication bypass also affected other endpoints, not just the XML-RPC one," the team said. "Once we were made aware, the second patch was issued within hours."
The vulnerability, tracked by Apache as OFBIZ-12873, "allows attackers to bypass authentication to achieve a simple Server-Side Request Forgery (SSRF)," Deepak Dixit, a member at the Apache Software Foundation, stated on the Openwall mailing list. He credited SonicWall threat researcher Hasib Vhora and two other researchers — Gao Tian and L0ne1y — with finding the issue.
Because OfBiz is a framework, and thus part of the software supply chain, the impact of the vulnerability could be widespread. The popular Atlassian Jira project and issue-tracking software, for example, uses the OfBiz library, but whether the exploit could successfully execute on the platform is still unknown, says Sonicwall's McKee.
"It's going to depend on the way each company architects their network, in the way they configure the software," he says. "I would say a typical infrastructure would not have this Internet-facing, that it would require some type of VPN or internal access."
In any event, companies should take steps and patch any applications known to use OfBiz to the latest version, the ASF security response team said.
"Our recommendation for companies that use Apache OFBiz is to follow security best practices, including only giving access to systems to those users that need it, making sure to regularly update your software, and making sure you are well-equipped to respond when a security advisory is published," they said.
About the Author
You May Also Like




