Emerging Ransomware Group 8Base Doxxes SMBs Globally
A threat you've never heard of is using double extortion attacks on mom-and-pop shops around the globe.
June 21, 2023

A ransomware group that operated under the radar for over a year has come to light in recent weeks, thanks to a series of business data leaks on the Dark Web.
Since at least April 2022, 8base — not to be confused with the Florida-based software company of the same name — has been conducting double-extortion attacks against small and midsized businesses (SMBs). It all came to a head in May, when the group dumped data belonging to 67 organizations on the cyber underground.
It didn't end there. "We've been keeping an eye on what they're doing, and this month they're busy again," says Matt Hull, global head of threat intelligence at NCC Group. 8base has already doxxed 29 new businesses this month.
Not much is known yet about the group's tactics, techniques, and procedures (TTPs), likely due to the low profile of their victims. According to data scraped from their leak site, those victims include a British cleaning company, a sanitation company in Egypt, a private school in a Boston suburb, and a CPA in New York, among others of a similar profile.
The victims span science and technology, manufacturing, retail, construction, healthcare, and more. They're wisely distributed geographically as well: a shipping company in India, a Peruvian gift basket company, and a corrugated cardboard manufacturer in Madagascar. The majority, however, are focused in North America — around a third of the total — and South America. A dozen victims in both May and June were based in Brazil, in line with a recent wave of Brazilian cyberattacks more generally.
How 8base Conducts Its Business
With little yet known about 8base (it's part of a wave of ransomware newbies entering the market), one aspect of the group that is very clear is their preferred mode of operation. In a terms-of-service section of their leak site (see graphic), the group laid out 13 rules for their victims and themselves, written in ersatz legalese: "Participation of police departments is prohibited," and "Personal data will not be shared with third parties by the team."
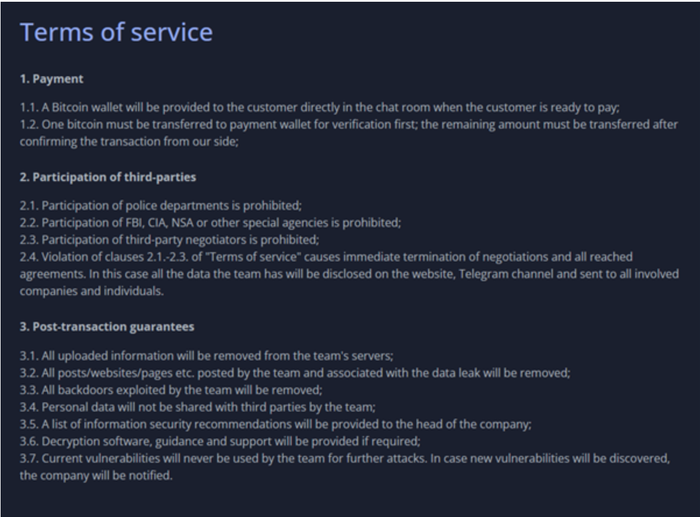
Source: Hackmanac
Whether the gang is as honest as it would like you to think is another matter. On the About Us page, the hackers perfidiously claim, "We are honest and simple pentesters," adding that "this list contains only those companies that have neglected the privacy and importance of the data of their employees and customers."
NCC's Hull says 8base is not the first group to operate like this. "I think it's a result of the successes that other groups are having with these types of tactics," he notes.
Though 8base isn't breaking any new ground, actually defending against their tried-and-true methods is another matter.
"Budgets are tight, particularly for the smaller organizations. These organizations aren't going to be able to pay for a SOC or other advanced detection capabilities," Hull notes. "The main thing that anyone can do, whether it's an individual or small business, is get the fundamentals right." He points to password hygiene, multifactor authentication, and social engineering awareness as three simple changes small businesses can make to better their security without breaking the bank.
"Getting a hold of the basics goes a long way," he adds.
About the Author
You May Also Like




