Serverless Computing: 'Function' vs. 'Infrastructure' as-a-Service
How much do companies really gain from offloading security duties to the cloud? Let's do the math.

Security is a shared responsibility between the cloud provider and the customer. This shared model can help relieve customer’s operational burden as cloud providers operate, manage, and control the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.
Up until recently, when deploying applications on infrastructure-as-a-service (IaaS) platforms, the customer assumed responsibility and management of the guest operating system, including updates and security patches, associated application software, and configuration of the network firewalls in the cloud. With virtual instances, customers need to carefully consider the services they chose as their responsibilities depending on the services used, the integration of those services into the IT environment, and applicable laws and regulations.
With the introduction of serverless computing (also known as FaaS, or function-as-a-service), security shifted even more towards cloud providers by allowing organizations to offload many more tasks in order to concentrate on their core business. But just how much do companies really gain by offloading security duties to the cloud? Let's do the math.
Core Requirements: Physical to Application Security
The items below are listed bottom-up, starting with physical security, all the way up to the application layer.
Physical infrastructure, access restrictions to physical perimeter and hardware
Secure configuration of infrastructure devices and systems
Regularly testing the security of all systems/processes (OS, services)
Identification and authentication of access to systems (OS, services)
Patching and fixing flaws in OS
Hardening OS and services
Protecting all systems against malware and backdoors
Patching and fixing flaws in runtime environment and related software packages
Exploit prevention and memory protection
Network segmentation
Tracking and monitoring all network resources and access
Installation and maintenance of network firewalls
Network-layer DoS protection
Authentication of users
Authorization controls when accessing application and data
Log and maintain audit trails of all access to application and data
Deploy an application layer firewall for event-data inspection
Detect and fix vulnerabilities in third-party dependencies
Use least-privileged IAM roles and permissions
Enforce legitimate application behavior
Data leak prevention
Scan code and configurations statically during development
Maintain serverless/cloud asset inventory
Remove obsolete/unused cloud services and functions
Continuously monitor errors and security incidents
IaaS: Provider vs. Customer
When developing applications on IaaS, the security responsibilities are roughly divided as follows:
Cloud Provider Responsibility
Physical infrastructure, access restrictions to physical perimeter and hardware
Secure configuration of infrastructure devices and systems
Customer Responsibility
Regularly testing the security of all systems/processes (OS, services)
Identification and authentication of access to systems (OS, services)
Patching and fixing flaws in OS
Hardening OS and services
Protecting all systems against malware and backdoors
Patching and fixing flaws in runtime environment and related software packages
Exploit prevention and memory protection
Network segmentation
Tracking and monitoring all network resources and access
Installation and maintenance of network firewalls
Network-layer DoS protection
Authentication of users
Authorization controls when accessing application and data
Log and maintain audit trails of all access to application and data
Deploy an application layer firewall for event-data inspection
Serverless (FaaS): Provider vs. Customer
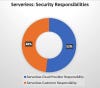
How responsibilities are divided when developing applications on serverless architectures:
Cloud Provider Responsibility
Physical infrastructure, access restrictions to physical perimeter and hardware
Secure configuration of infrastructure devices and systems
Regularly testing the security of all systems/processes (OS, services)
Identification and authentication of access to systems (OS, services)
Patching and fixing flaws in OS
Hardening OS and services
Protecting all systems against malware and backdoors
Patching and fixing flaws in runtime environment and related software packages
Exploit prevention and memory protection
Network segmentation
Tracking and monitoring all network resources and access
Installation and maintenance of network firewalls
Network-layer DoS protection
Customer Responsibility
Authentication of users
Authorization controls when accessing application and data
Log and maintain audit trails of all access to application and data
Deploy an application layer firewall for event-data inspection
Detect and fix vulnerabilities in third-party dependencies
Use least-privileged IAM roles and permissions
Enforce legitimate application behavior
Data leak prevention
Scan code and configurations statically during development
Maintain serverless/cloud asset inventory
Remove obsolete/unused cloud services and functions
Continuously monitor errors and security incidents
FaaS vs. SaaS?
Not all tasks and requirements are created equal — and some of those I've included are obviously more resource and budget intensive than others. If you disagree with my methodology or conclusions, please share your thoughts in the comments.
Related Content:
About the Author
You May Also Like




