Charting the Path to Zero Trust: Where to Begin
Your journey to zero trust can be perilous if you are using legacy equipment that wasn’t designed for it. Begin the transformation where it makes the most sense for your organization.

Digital transformation is a journey, and much like any adventure, a bit of preparation can go a long way in driving a successful outcome. Preparing for any adventure includes determining where you want to go, deciding on the best way to get there, and gathering the equipment, services, and supplies you’ll need along the way.
An IT transformation journey typically begins with application transformation, where you move applications out of the data center and into the cloud. Then, network transformation becomes necessary to enable users to access applications that are now widely dispersed—moving from a hub-and-spoke network architecture to a direct connectivity approach. This, in turn, drives a need for security transformation, where you shift from a castle-and-moat security approach to a zero-trust architecture.
While the aforementioned order is typical, there are a few different ways to achieve similar outcomes. You should begin your journey toward zero trust wherever you feel most comfortable or prepared. If it makes more sense for your organization to begin with security transformation before app transformation, you can.
Assess Your Equipment
Castle-and-moat security architectures, leveraging firewalls, VPNs, and centralized security appliances, worked well when applications lived in the data center and users worked in the office. It was the right equipment for the job at the time. Today, though, your workforce works from everywhere, and applications have moved out of the data center and into public clouds, SaaS, and other parts of the internet. Those firewalls, VPNs, and legacy security hardware stacks were not designed to meet the needs of today’s highly distributed business and have outlived their usefulness.
To grant users access to applications, VPNs and firewalls must connect users to your network, essentially extending the network to all your remote users, devices, and locations. This puts your organization at greater risk by giving attackers more opportunities to compromise users, devices, and workloads, and more ways to move laterally to reach high-value assets, extract sensitive data, and inflict damage on your business. Protecting your highly distributed users, data, and applications requires a new approach—a better approach.
Mapping the Best Route
When it comes to security transformation, innovative leaders are turning to zero trust. Unlike perimeter-based security approaches that rely on firewalls and implicit trust and provide broad access once trust is established, zero trust is a holistic approach to security based on the principle of least-privileged access and the idea that no user, device, or workload should be inherently trusted. It begins with the assumption that everything is hostile, and grants access only after identity and context are verified and policy checks are enforced.
Achieving true zero trust requires more than pushing firewalls to the cloud. It requires a new architecture, born in the cloud and delivered natively through the cloud, to securely connect users, devices, and workloads to applications without connecting to the network.
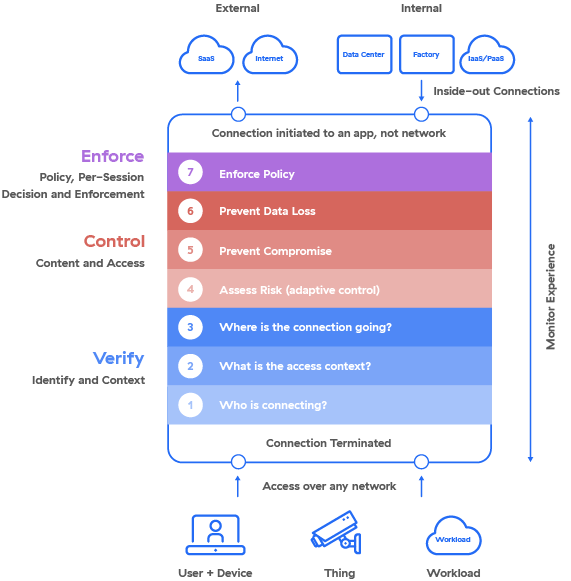
As with any significant journey, it’s helpful to break your way to zero trust into various legs that clearly define the path while keeping the ultimate destination in mind. When considering your approach, seven essential elements will enable you to dynamically and continuously assess risk and securely broker communications over any network, from any location.
Using these elements, your organization can implement true zero trust to eliminate your attack surface, prevent the lateral movement of threats, and protect your business against compromise and data loss.
These elements can be grouped into three sections:
Verify identity and context
Control content and access
Enforce policy
Let’s take a closer look.
Source: Zscaler
Verify Identity and Context
The adventure begins when a connection is requested. The zero-trust architecture will begin by terminating the connection and verifying identity and context. It looks at the who, what, and where of the requested connection.
1. Who is connecting? The first essential element is to verify the user/device, IoT/OT device, or workload identity. This is achieved through integrations with third-party identity providers (IdPs) as part of an enterprise identity access management (IAM) provider.
2. What is the access context? Next, the solution must validate the context of the connection requester by looking into details such as the role, responsibility, time of day, location, device type, and circumstances of the request.
3. Where is the connection going? The solution next needs to confirm that the identity owner has the rights and meets the required context to access the application or resource based on entity-to-resource segmentation rules—the cornerstone of zero trust.
Control Content and Access
After verifying identity and context, the zero-trust architecture evaluates the risk associated with the requested connection and inspects traffic to protect against cyber threats and the loss of sensitive data.
4. Assess risk. The solution should use AI to dynamically compute a risk score. Factors including device posture, threats, destination, behavior, and policy should be continually evaluated throughout the life of the connection to ensure the risk score remains up to date.
5. Prevent compromise. To identify and block malicious content and prevent compromise, an effective zero-trust architecture must decrypt traffic inline and leverage deep content inspection of entity-to-resource traffic at scale.
6. Prevent data loss. Outbound traffic must be decrypted and inspected to identify sensitive data and prevent its exfiltration using inline controls or by isolating access within a controlled environment.
Enforce Policy
Before reaching the end of the journey and ultimately establishing a connection to the requested internal or external application, one final element must be implemented: enforcing policy.
7. Enforce policy. Using the outputs of the previous elements, this element determines what action to take regarding the requested connection. The end goal is not a simple pass/not pass decision. Instead, the solution must constantly and uniformly apply policy on a per-session basis—regardless of location or enforcement point—to provide granular controls that ultimately result in a conditional allow or conditional block decision.
Once an allow decision is reached, a user is granted a secure connection to the internet, SaaS app, or internal application.
Securely Reach Your Destination
Your journey to zero trust can be perilous if you’re trying to get there with legacy equipment that wasn’t designed for it. While finding a solution that enables true zero trust may at first seem daunting, begin where it makes the most sense for your organization, and let the seven elements outlined here serve as your guide.
Read more Partner Perspectives from Zscaler.
About the Author
You May Also Like



_KonstantinNechaev-Alamy.jpg?width=700&auto=webp&quality=80&disable=upscale)
