2023: A 'Good' Year for OT Cyberattacks
Attacks increased by "only" 19% last year. But that number is expected to grow significently.

COMMENTARY
Waterfall Security Solutions, in collaboration with ICS Strive, recently released its "2024 Threat Report." The bad news is that, in 2023, there were 68 cyberattacks that took down more than 500 physical operations. The good news (sort of) is that this is only 19% more attacks than the previous year. What's going on? Ransomware attacks with physical consequences are down slightly, hacktivist attacks are constant, and everything else is increasing. The report's authors conclude that the 19% increase is most likely an aberration, and that we'll see an increase closer to 90% to 100% in 2024.
The Details
Waterfall's operational technology (OT) security threat report is the most cautious in the industry — it tracks only deliberate cyberattacks that caused physical consequences in building automation, heavy industry, manufacturing, and critical industrial infrastructures in the public record. That is, no private or confidential disclosures. The complete data set for the report is included in its appendix. This means the report is certain to be an underestimate of what's really happening in the world, because the authors report regular confidential disclosures that they cannot include in their counts.
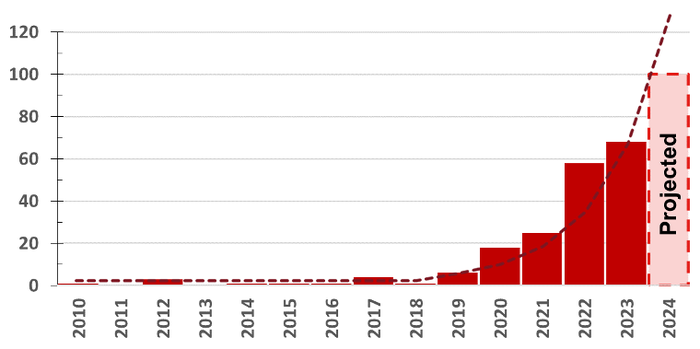
OT incidents since 2010. Source: "2024 Threat Report," Waterfall Security Solutions, in collaboration with ICS Strive
More Attacks
In spite of this underestimate, cyberattacks that met the inclusion criteria continue to increase, nearly doubling annually since 2019. This is a big change from 2010–2019, when OT attacks with physical consequences were flat, bouncing around between zero and five attacks annually.
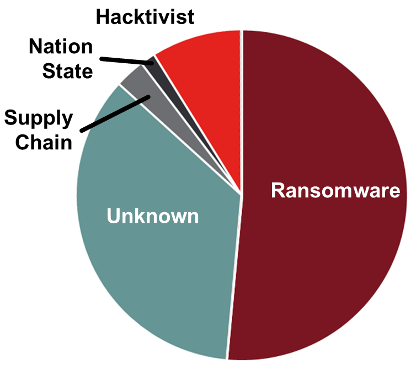
Threat actors. Source: "2024 Threat Report," Waterfall Security Solutions, in collaboration with ICS Strive
What are these attacks? In 24 of 68 cases, there was not enough information in the public record to attribute the attack. Of the remaining, 35 attacks (80%) were ransomware, six (14%) were hacktivists, two were supply chain attacks, and one was attributed to a nation state. The 35 ransomware attacks are down slightly from last year's 41, which is unexpected, given that ransomware attacks on IT networks continue to increase at between 60% to 70% per year, depending on the report. Why? In part, because public reports this year were less detailed, there were many more "unknown" threat actors this year.
Another factor has to do with the fact that most ransomware attacks that impact physical operations did so only accidentally — either because of "abundance of caution" OT shutdowns, when IT is impaired, or physical operations being dependent on crippled IT infrastructure. In 2023, we saw a material fraction of ransomware criminal groups shift away from encrypting and disabling systems to simply stealing the data and demanding ransoms to destroy the stolen data rather than publish it. With fewer IT systems being crippled through encryption, it looks like fewer OT systems and physical operations are being impaired.
We expect this trend to stabilize in 2024, and for OT impacts due to ransomware to go back to the recently historic norm of nearly doubling annually. Why? Because not all businesses have data they are willing to pay to protect. Such businesses, especially critical infrastructures, may still, however, pay a ransom to restore functionality to crippled systems, so it makes sense that at least some ransomware criminals will not leave money on the table and will continue to cripple servers, in addition to stealing what data they can.
Supply Chain
Supply chain attacks with physical consequences showed up this year for the first time in many years. Newag SA was accused of embedding code in its trains to maximize the revenues of authorized repair shops. It is accused of acting to "lock up the train with bogus error codes after some date, or if the train wasn't running for a period of time." Some of the code was found to contain GPS coordinates to confine the behavior to third-party workshops. Newag denies the accusations, blaming "unknown hackers." And in an apparent contractual dispute, ORQA, a manufacturer of first-person view (FPV) virtual reality headsets, had its products locked up by what it describes as a "greedy former contractor."
Wrapping Up
There are many other findings in the report: GPS blocking and spoofing is becoming a widespread problem, manufacturing businesses accounted for more than one half of the attacks with outages, hacktivists are targeting critical infrastructures, and there is an alarming batch of near misses, including the many critical infrastructures and utilities targeted by China's Volt Typhoon "living off the land" campaign. The report also touches on promising new developments on the defensive side, including the Cyber-Informed Engineering Strategy.
About the Author
You May Also Like




